CHALLENGE ROOM
Training
Level:
EASY
Technology: Linux
Challenge description
With the entire incident, McElferson has been very stressed.
We need all hands on deck now
Challenge Overview
The challenge provides SSH access to a remote Linux machine. The goal is to utilize basic Linux commands to extract specific information and answer a series of questions related to file enumeration, content inspection, and system configuration.
Task 1: How many visible files are there in the home directory (excluding . and ..)?
To determine the number of visible files in the home directory, we use the ls command:
lsThe output lists the visible files, excluding the . and .. directory references.
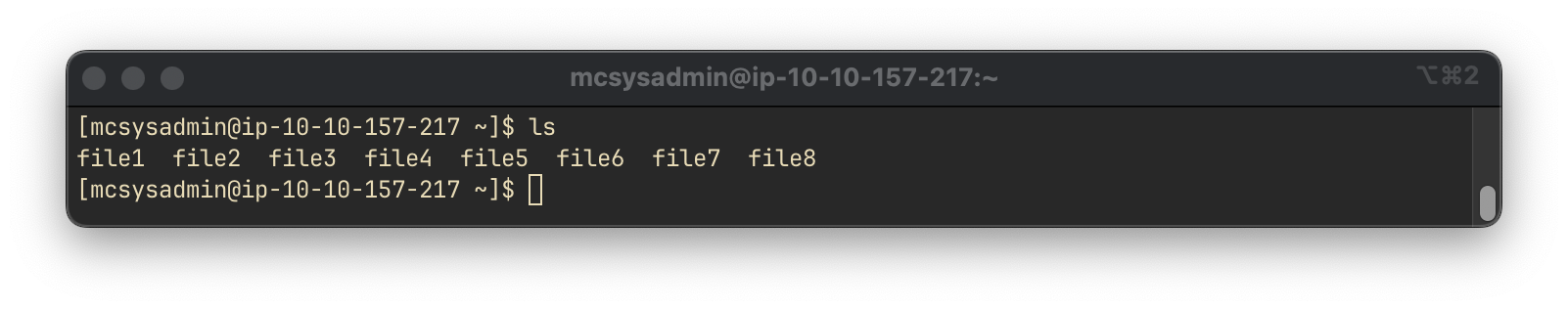
Answer:
8
Task 2: What is the content of file5?
To read the contents of file5, we use the cat command:
cat file5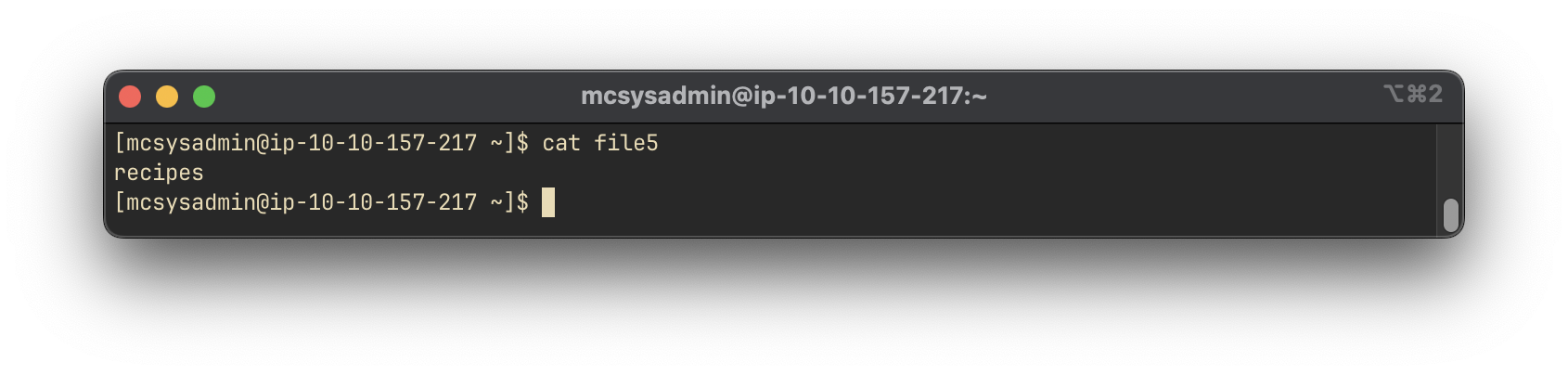
Answer:
recipes
Task 3: Which file contains the string password?
To locate the file containing the string password, we utilize grep with a wildcard to scan all files in the directory:
grep password file*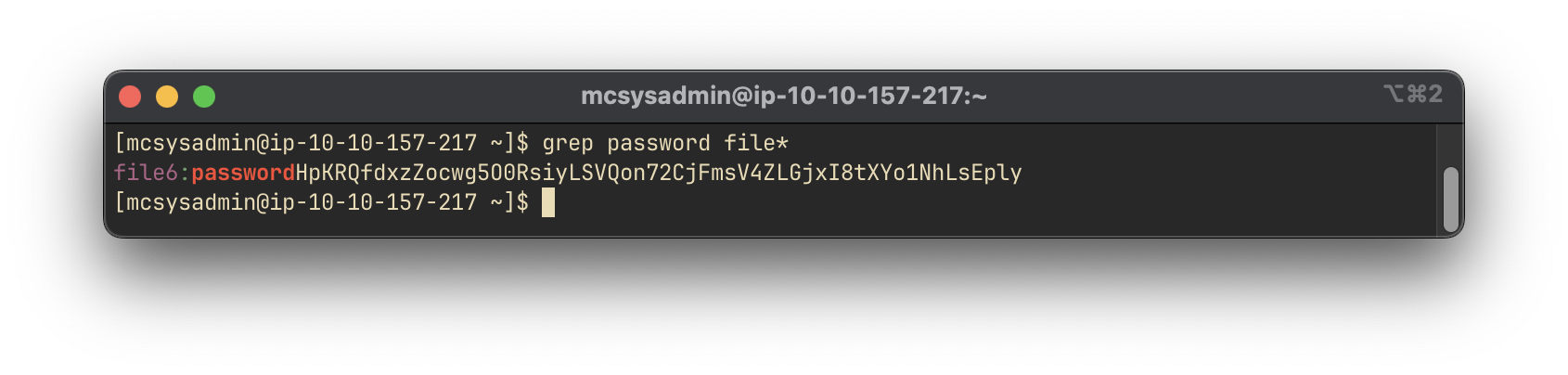
Answer:
file6
Task 4: What is the IP address found in a file in the home folder?
To search for an IP address pattern, we use grep with a regular expression that matches standard IPv4 addresses:
grep -o '[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}\.[0-9]\{1,3\}' file*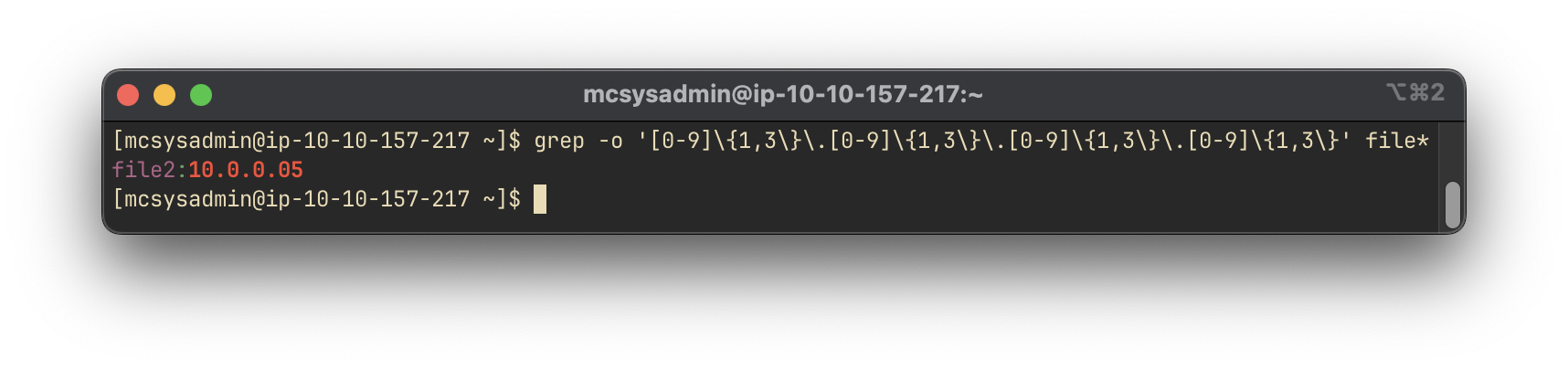
Answer:
10.0.0.05
Task 5: How many users can log into the machine?
To determine the number of users who can log into the system, we inspect the /etc/passwd file and count users with a valid shell (e.g., /bin/bash, /bin/sh):
cat /etc/passwd | grep -E '/bin/(bash|sh)'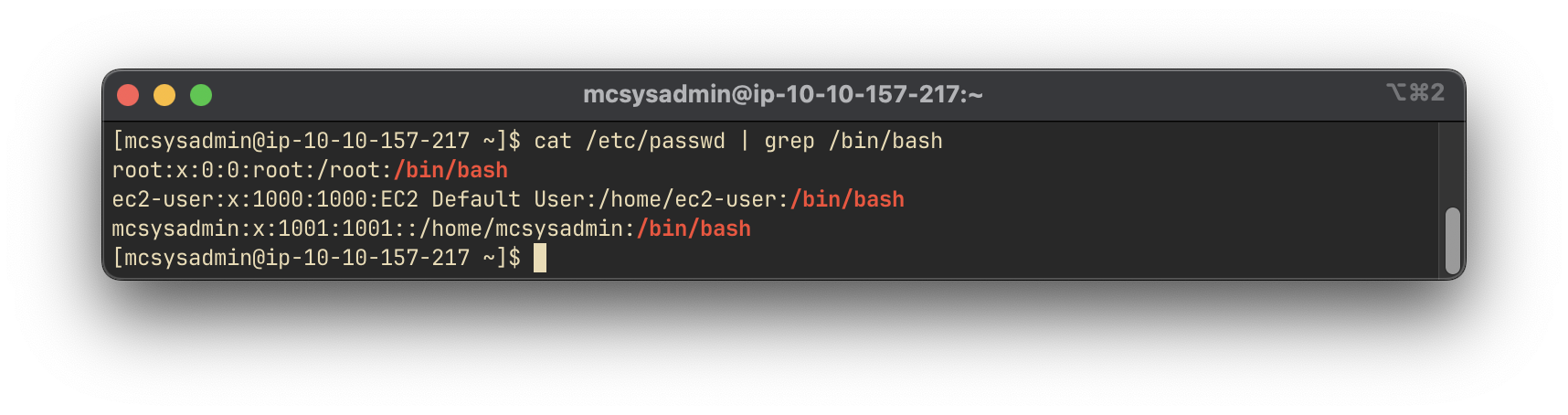
Answer:
3
Task 6: What is the SHA1 hash of file8?
To calculate the SHA1 hash of file8, we use the sha1sum command:
sha1sum file8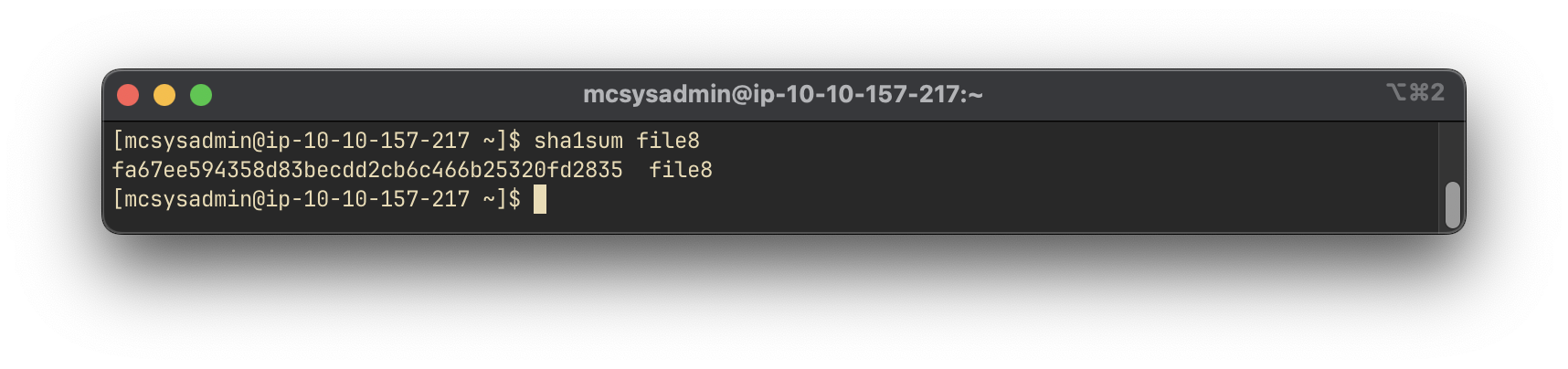
Answer:
fa67ee594358d83becdd2cb6c466b25320fd2835
Task 7: What is mcsysadmin’s password hash?
Although access to /etc/shadow is restricted, a backup file named shadow.bak is discovered in the home directory using the find command:
find / -name '*shadow*' 2>/dev/null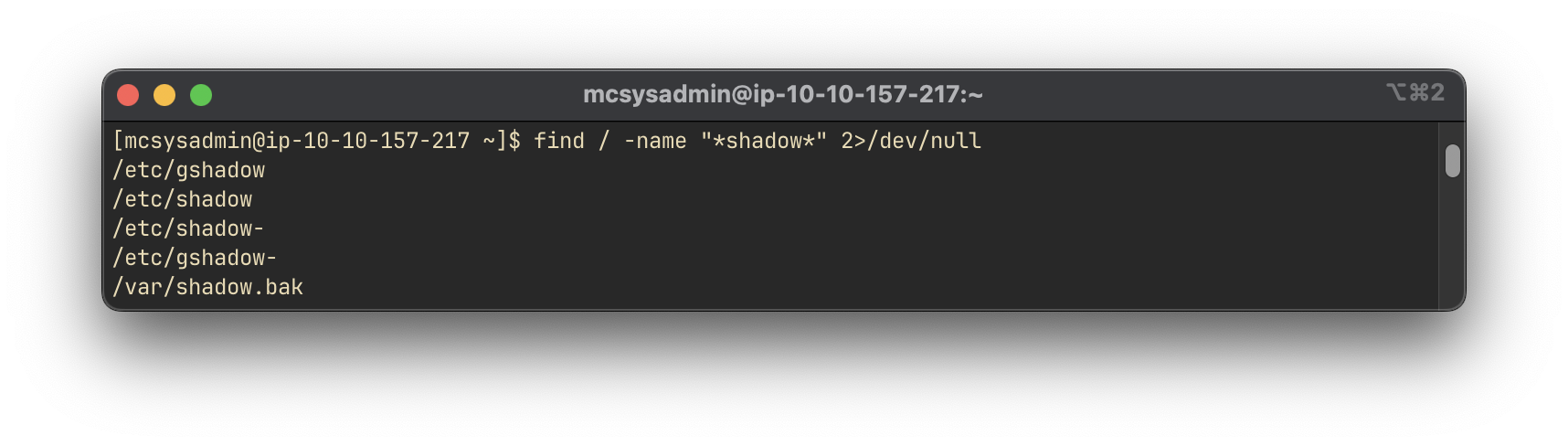
We then inspect the file contents to retrieve the password hash for the user mcsysadmin:
cat /var/shadow.bak | grep mcsysadmin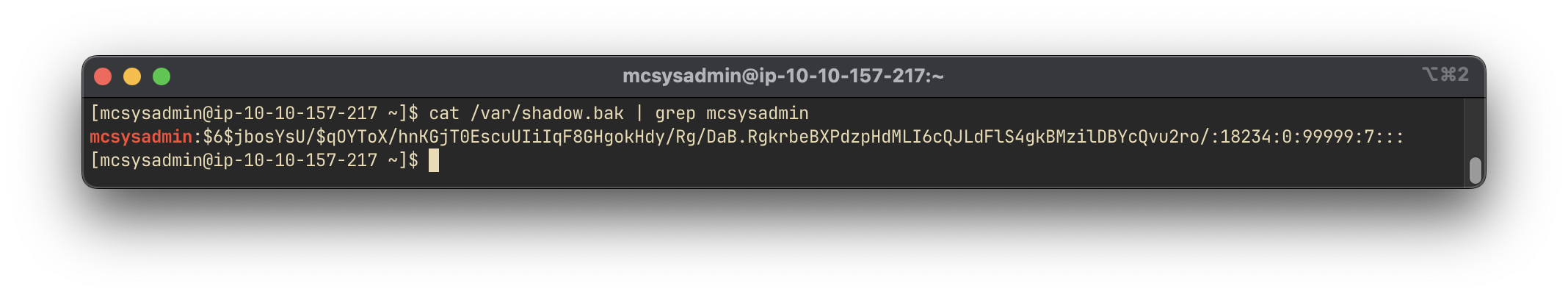
Answer:
$6$jbosYsU/$qOYToX/hnKGjT0EscuUIiIqF8GHgokHdy/Rg/DaB.RgkrbeBXPdzpHdMLI6cQJLdFlS4gkBMzilDBYcQvu2ro/
