Challenge description
Elves needed a way to submit their inventory - have a web page where they submit their requests and the elf mcinventory can look at what others have submitted to approve their requests. It’s a busy time for mcinventory as elves are starting to put in their orders. mcinventory rushes into McElferson’s office.
I don’t know what to do. We need to get inventory going. Elves can log on but I can’t actually authorise people’s requests! How will the rest start manufacturing what they want.
Challenge Overview
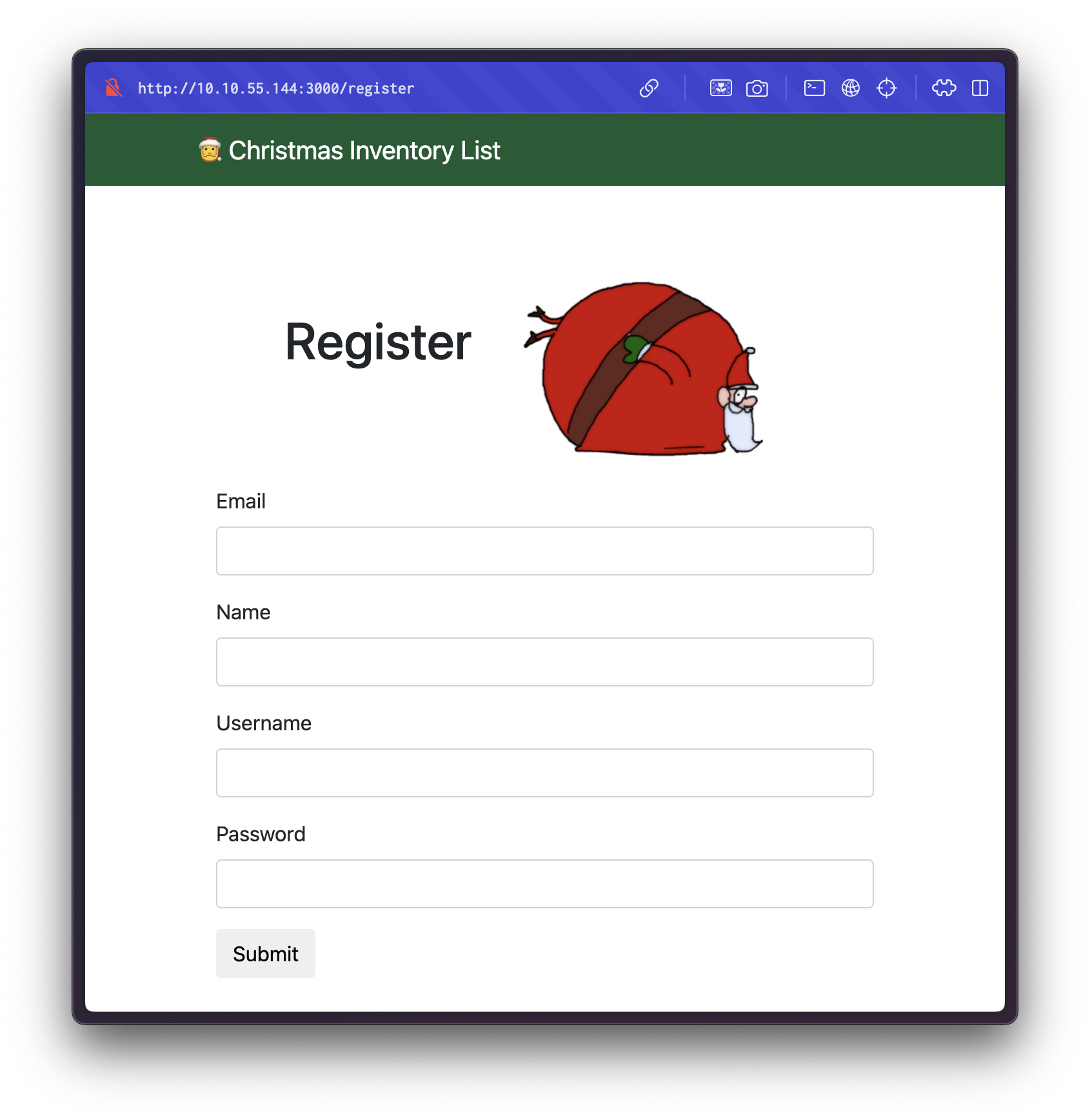
The target website features both login and registration functionalities.
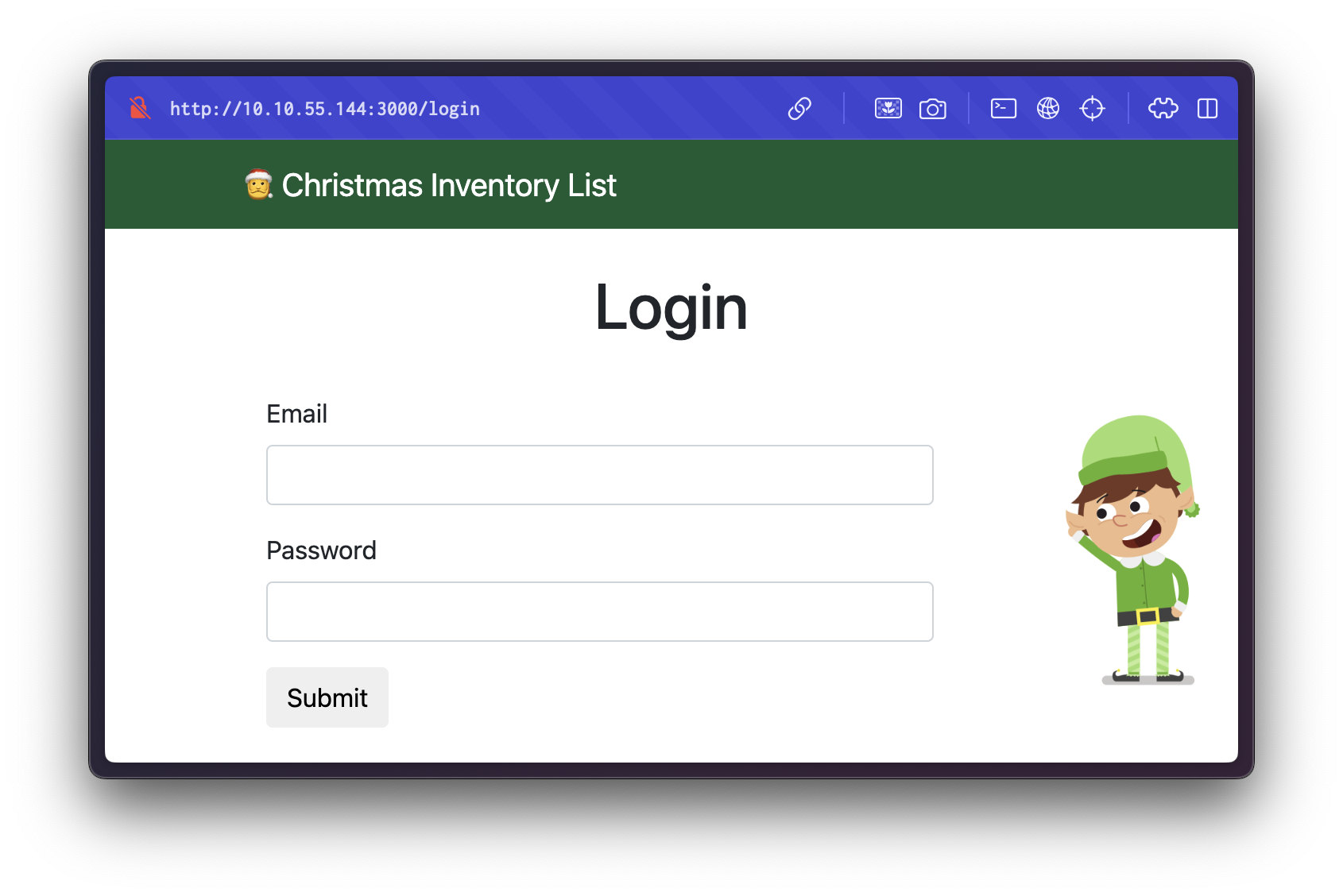
Upon registering a new user account, we are able to successfully log in:
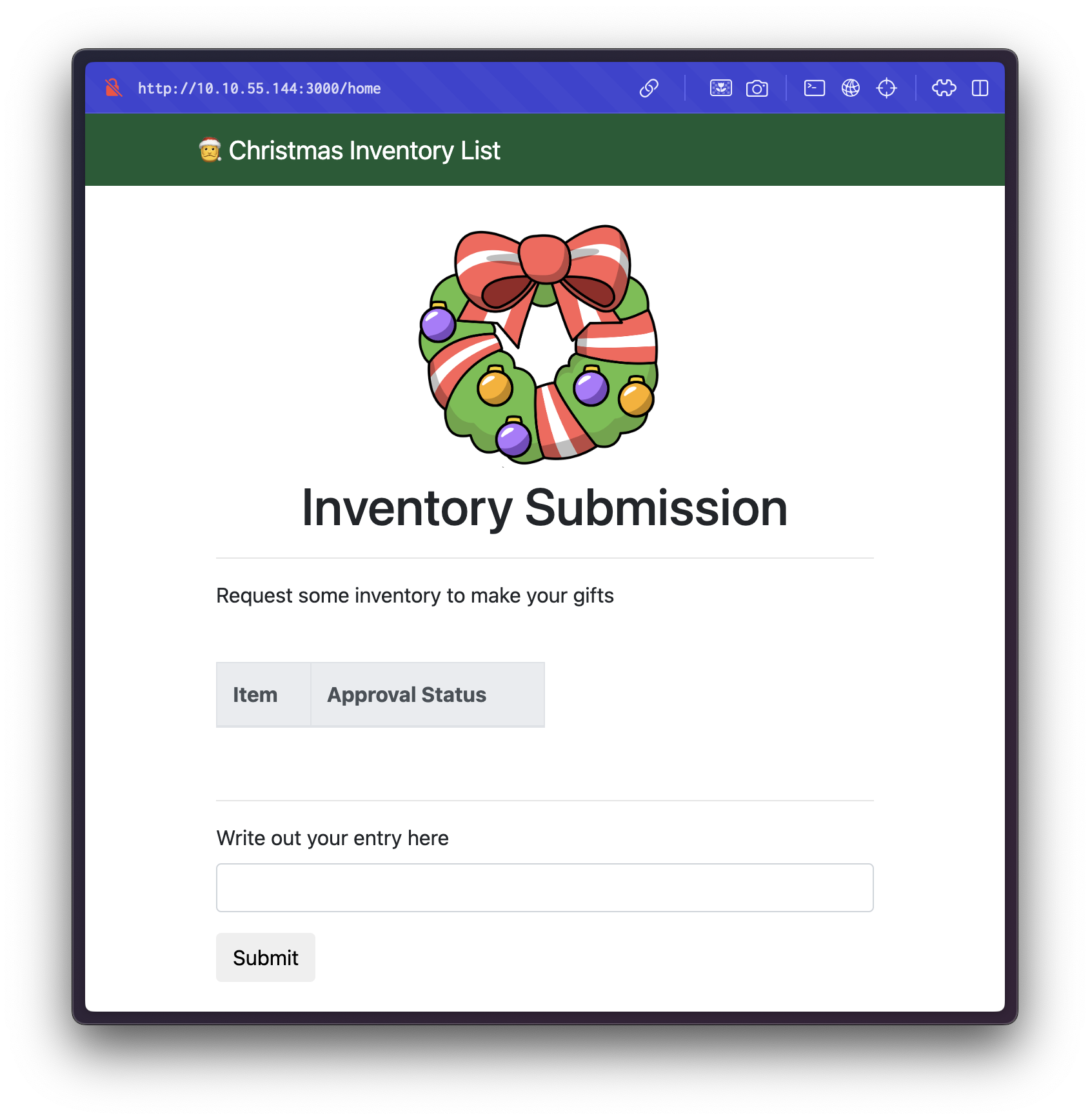
After logging in, the application redirects us to the homepage:
Identifying the Authentication Cookie
Using the browser's Developer Tools (specifically the Application tab), we inspect the cookies set by the application:
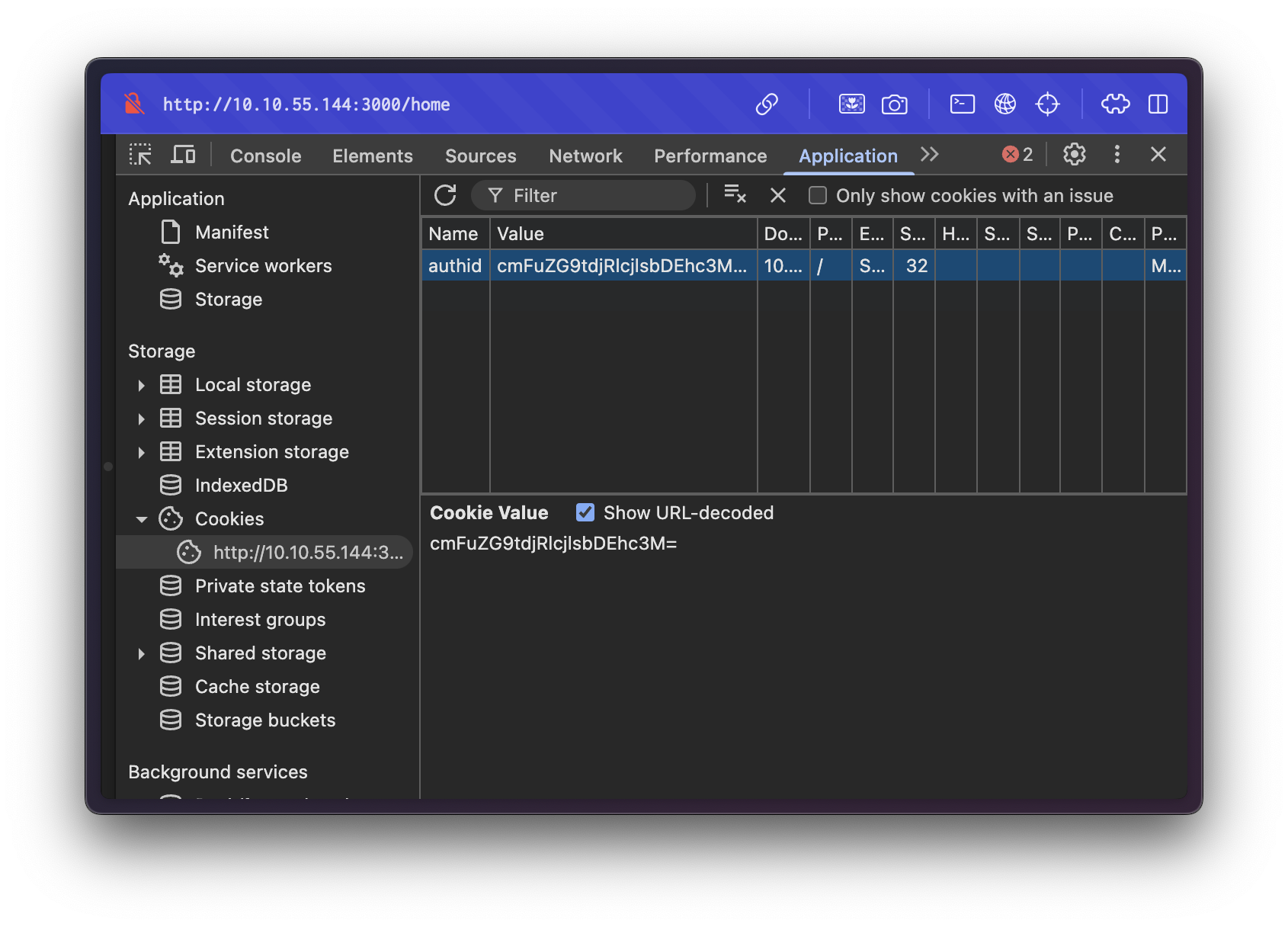
We observe that the application uses a cookie named:
Answer:
authid
This cookie appears to be responsible for session or authentication tracking.
Decoding the Cookie Value
The authid cookie value we received is:
cmFuZG9tdjRlcjlsbDEhc3M%3DUsing CyberChef, we:
- URL-decode the string.
- Base64-decode the result.
The decoded output is:
randomv4er9ll1!ssIn this string:
randomcorresponds to the username.v4er9ll1!ssappears to be a static or fixed suffix, likely used to validate or construct the authentication value.
Answer:
v4er9ll1!ss
Privilege Escalation via Cookie Manipulation
To explore further, we attempt to impersonate another user—mcinventory—by crafting a new authid value:
mcinventoryv4er9ll1!ssUsing CyberChef, we:
- Base64-encode the string.
- URL-encode the result.
This gives us a forged authid cookie. After replacing our current cookie with the manipulated one and refreshing the page, we are redirected to the /admin panel:
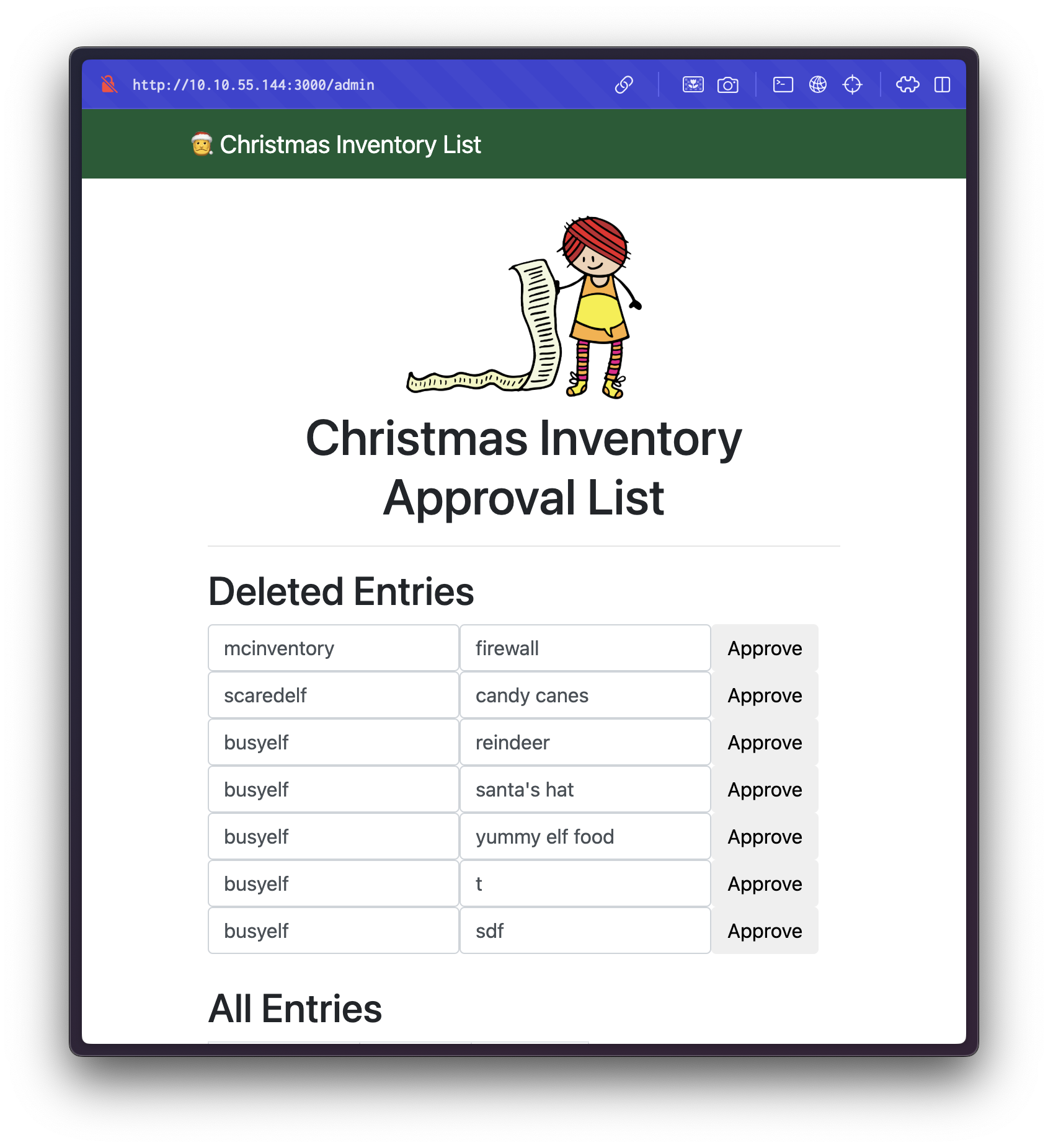
Within the admin panel, we find an entry indicating that the user mcinventory has made a request for a:
Answer:
firewall

