Challenge description
"McElferson! McElferson! Come quickly!" yelled Elf-ministrator.
"What is it Elf-ministrator?" McElferson replies.
"Data has been stolen off of our servers!" Elf-ministrator says!
"What was stolen?" She replied.
"I... I'm not sure... They hid it very well, all I know is something is missing" they replied.
"I know just who to call" said McElferson...
Challenge Overview
We are provided with a .pcap (packet capture) file for analysis, which contains network traffic potentially used for data exfiltration.
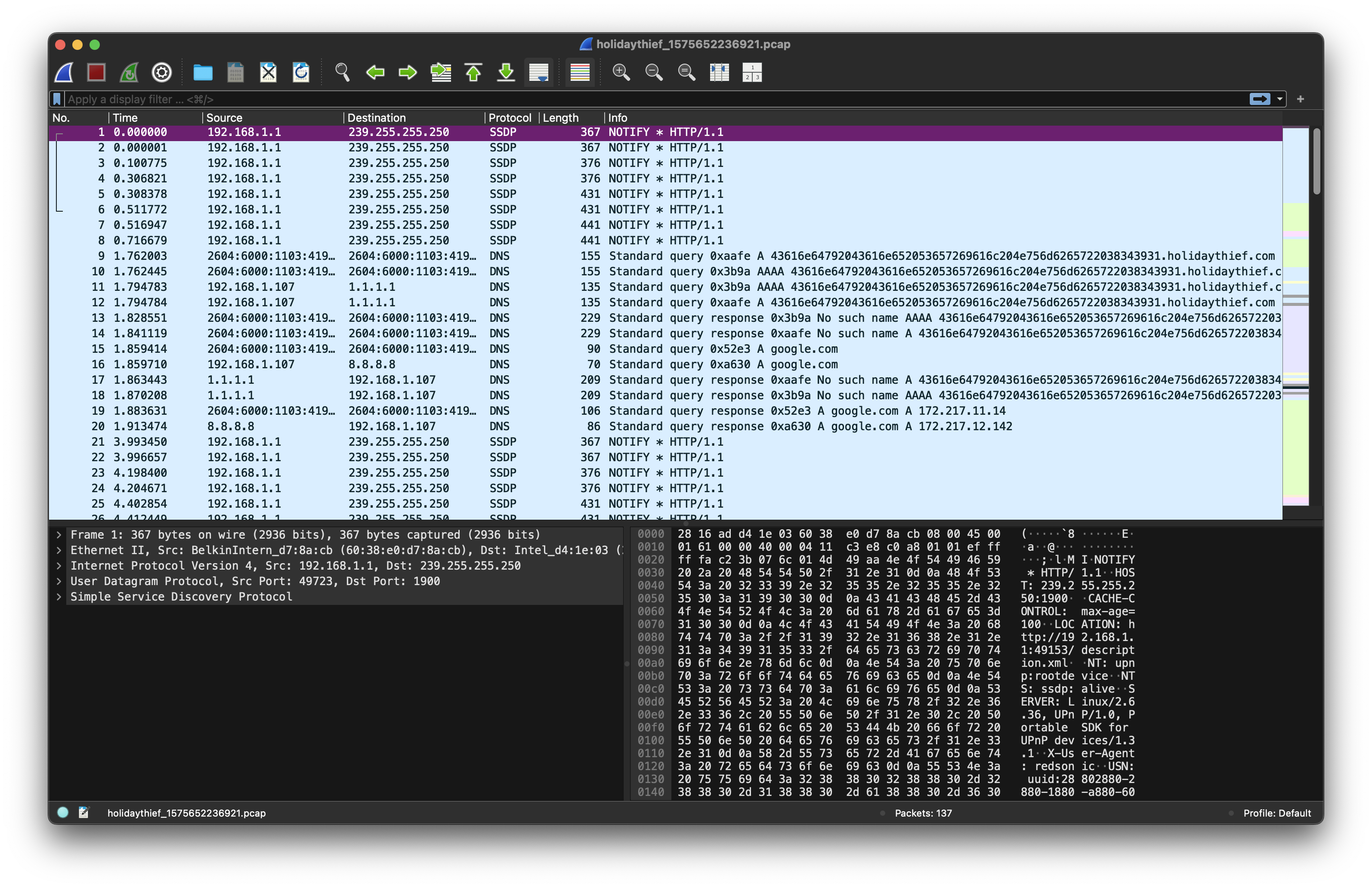
Task 1: What data was exfiltrated via DNS?
Upon opening the .pcap file in Wireshark, we observe a high volume of DNS requests.
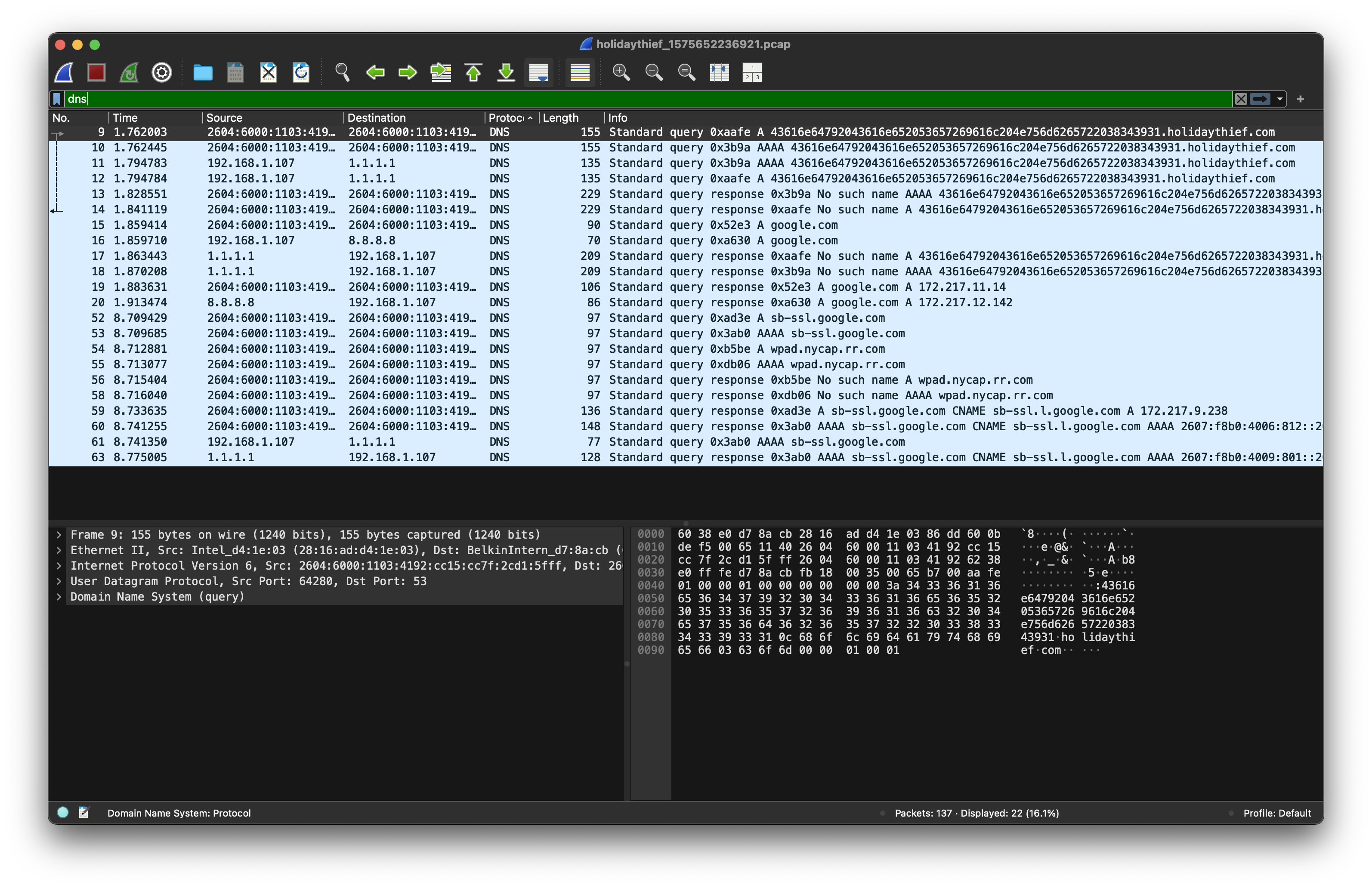
Within the captured DNS traffic, specific queries appear to contain encoded data being sent to the domain holidaythief.com, which is indicative of DNS data exfiltration:
43616e64792043616e652053657269616c204e756d6265722038343931.holidaythief.com: type A, class INThe subdomain portion is hexadecimal-encoded. Decoding the hex string reveals:
Candy Cane Serial Number 8491Answer:
Candy Cane Serial Number 8491
Task 2: What did Little Timmy want to be for Christmas?
To answer this question, we analyze HTTP traffic captured in the .pcap file.
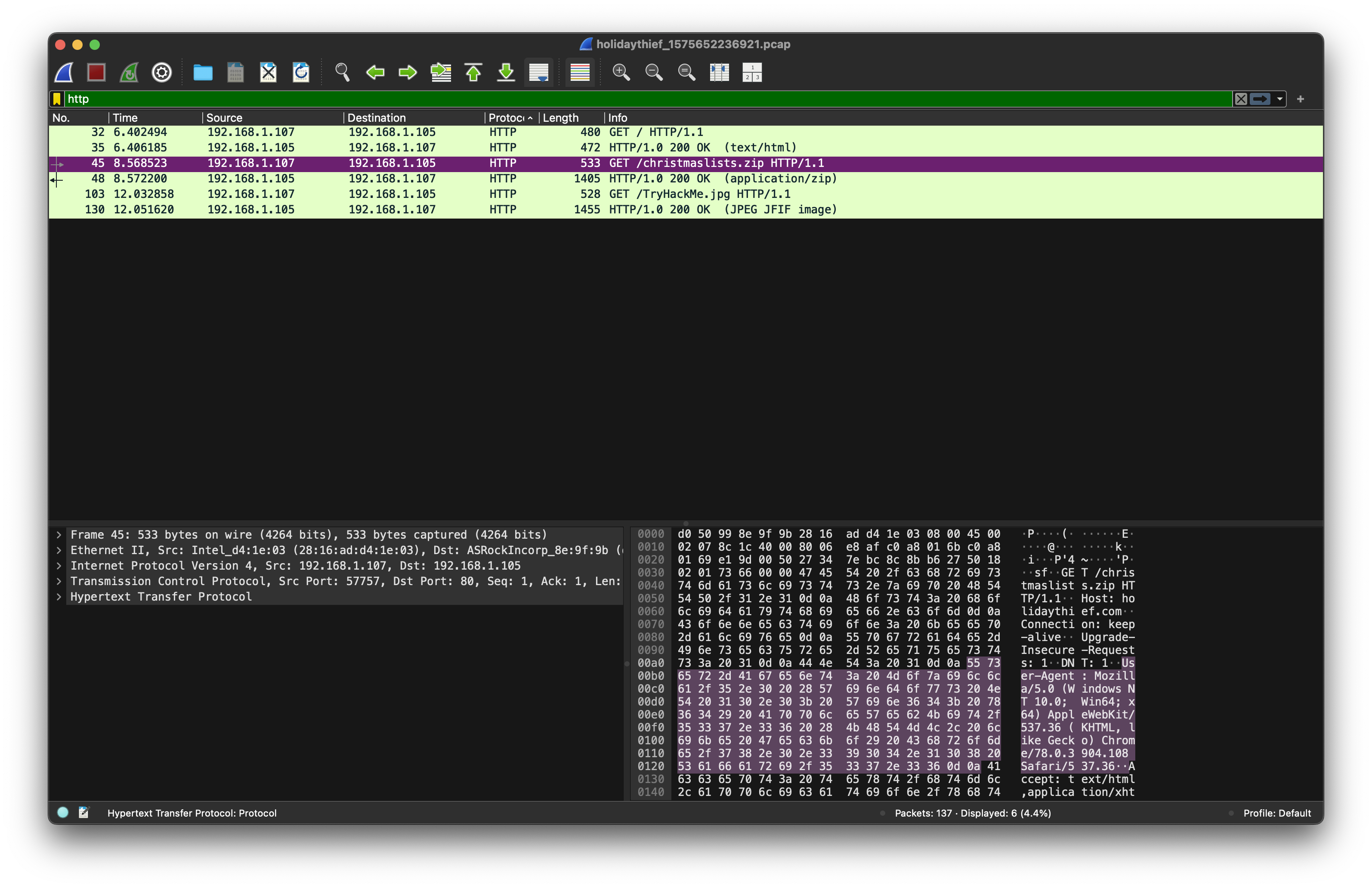
Using Wireshark's Export Objects → HTTP feature:
We observe three downloadable files:
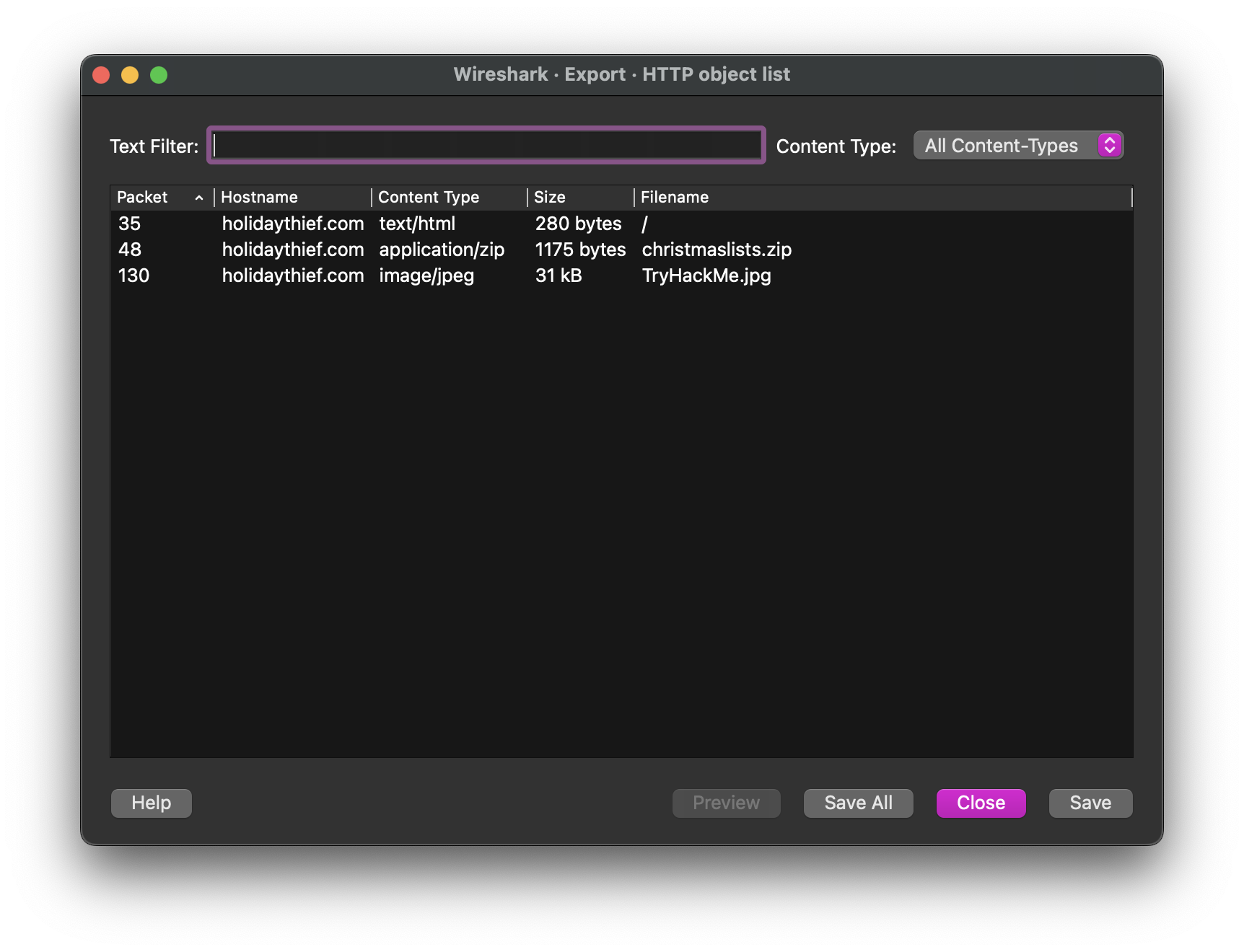
Among them is a file named christmaslists.zip. After downloading, we attempt to extract it but find it is password-protected. We use fcrackzip to brute-force the password using a common wordlist:
fcrackzip -b --method 2 -D -p /usr/share/wordlists/rockyou.txt -v christmaslists.zipThe output reveals the password:
possible pw found: december ()After extracting the archive with the password december, we find a text file listing Timmy’s Christmas wishes.
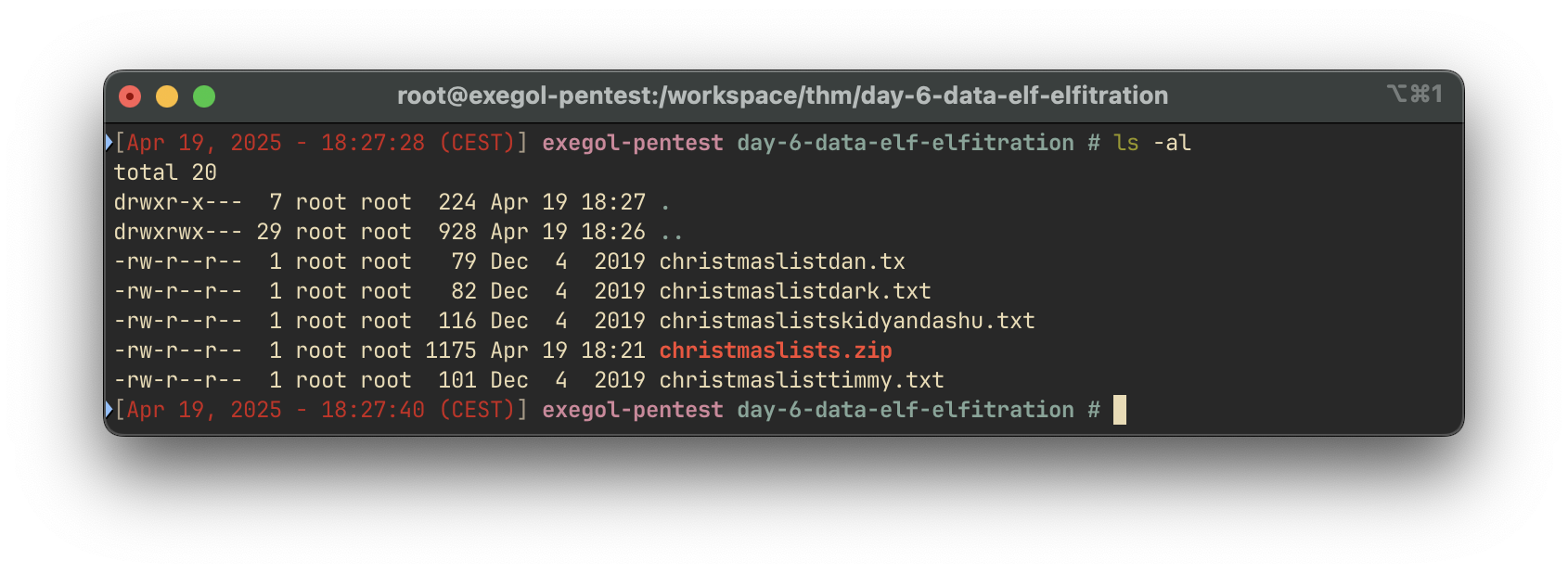
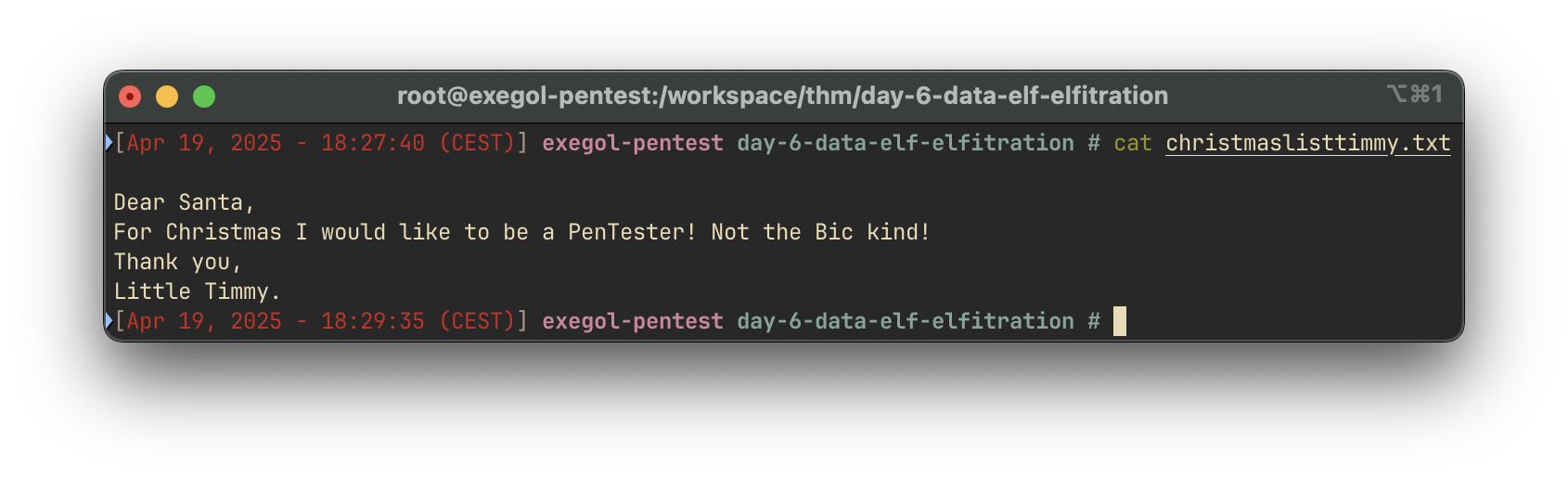
The list reveals that Timmy wants to be a:
Answer:
Pentester
Task 3: What was hidden within the file?
Among the exported HTTP objects is also an image file named TryHackMe.jpg.

To investigate whether this image contains hidden content, we use the steghide tool, which is designed for detecting and extracting steganographically hidden data:
steghide extract -sf TryHackMe.jpgAfter providing the password when prompted (likely the same december), the tool successfully extracts a hidden file.
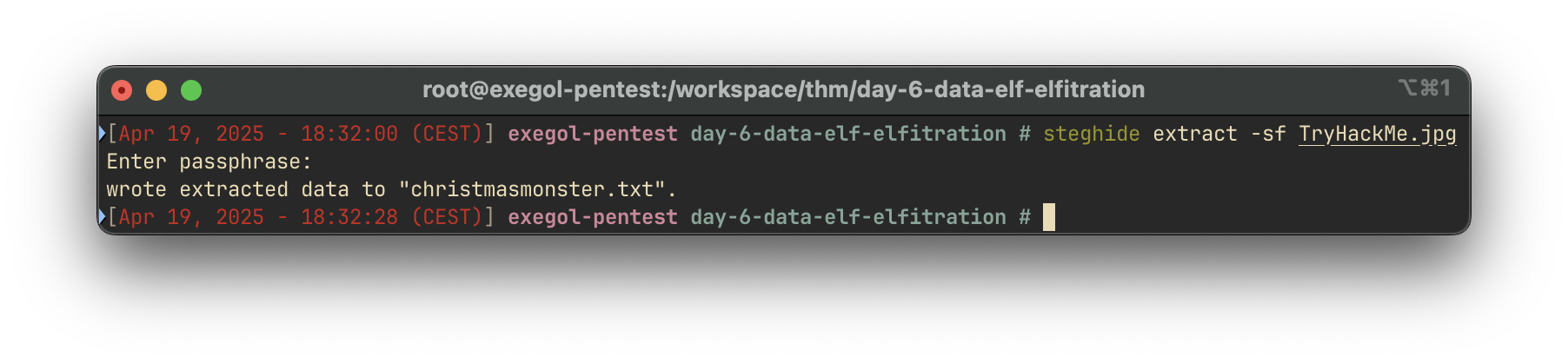
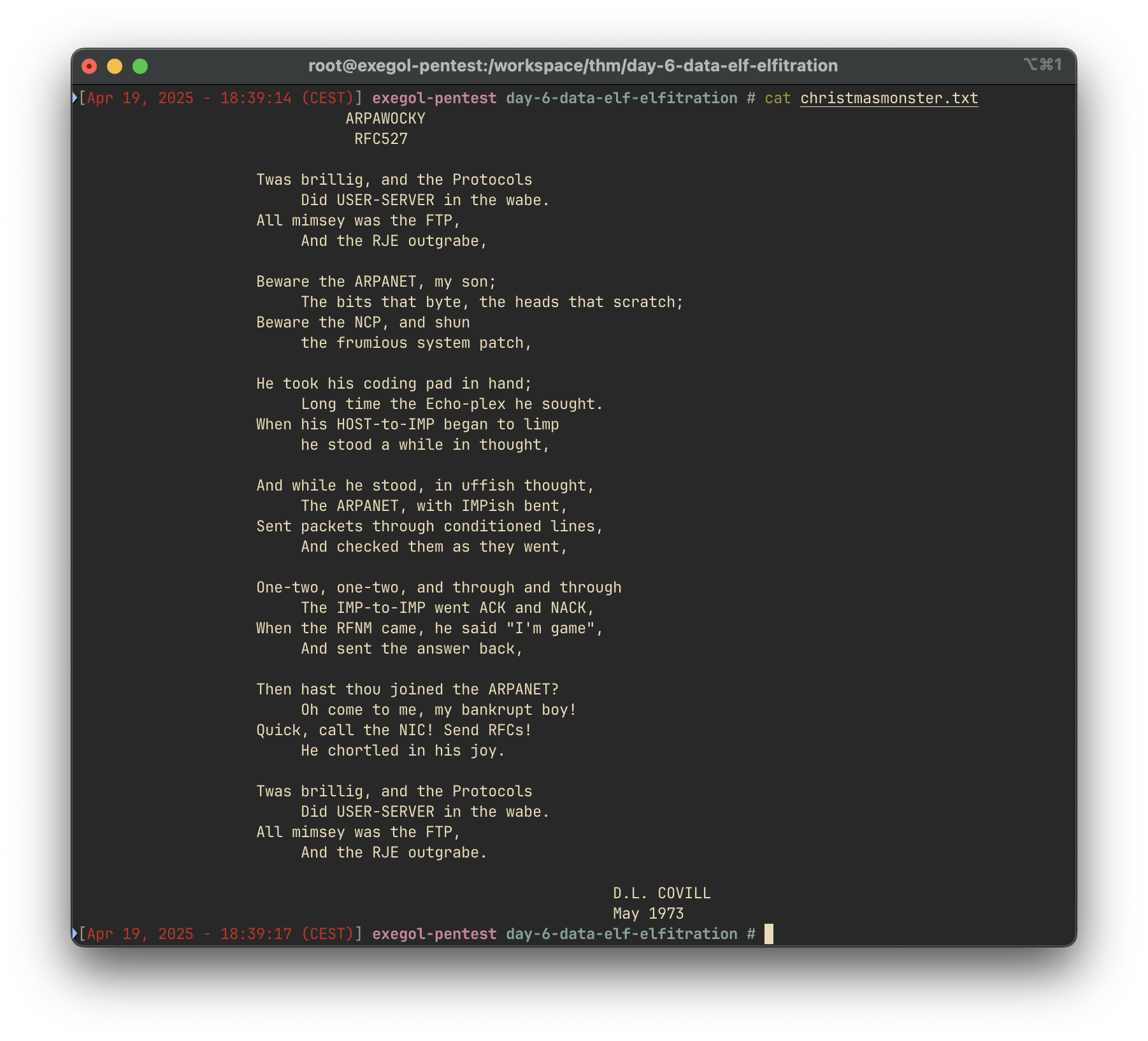
The hidden file is contains the RFC527, which appears to be the final answer.
Answer:
RFC527

