Challenge Description
Check out our new cloud service, Authentication Anywhere -- log in from anywhere you would like! Users can enter their username and password, for a totally secure login process! You definitely wouldn't be able to find any secrets that other people have in their profile, right?
Challenge Overview
To be completed: This section should briefly describe the objective of the challenge, including the environment (e.g., a vulnerable web application), intended difficulty, and any key skills being tested (e.g., input manipulation, authentication bypass).
Web Enumeration
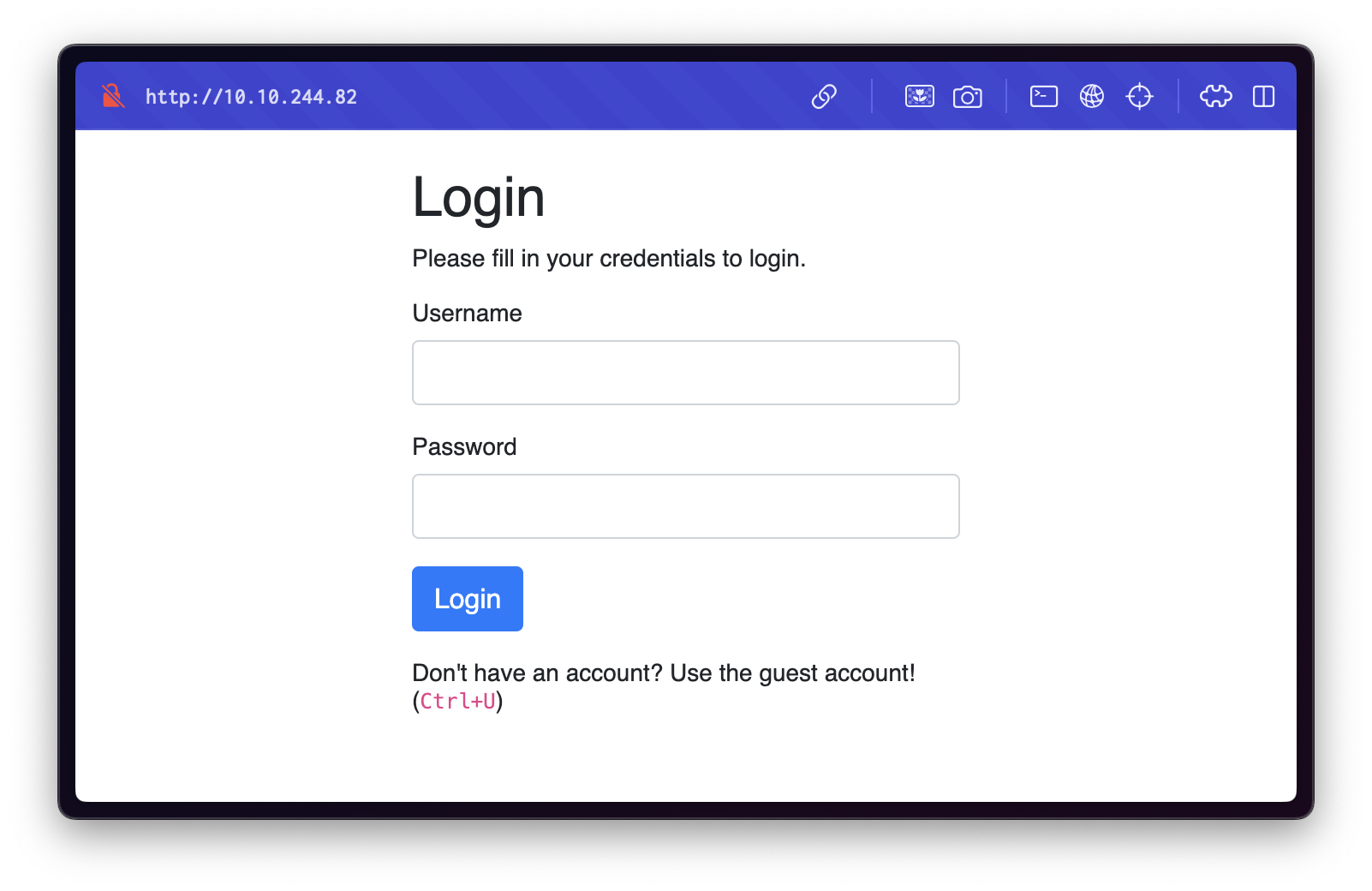
Upon navigating to the target URL http://10.10.244.82, we are presented with a login page:
Inspecting the page source reveals a noteworthy HTML comment:
<!-- use guest:guest credentials until registration is fixed. "admin" user account is off limits!!!!! -->This suggests that the application accepts the guest credentials (guest:guest) for login. It also hints that an admin account exists, but is presumably restricted.
Using the provided guest credentials, we successfully log in and are redirected to a user-specific page:
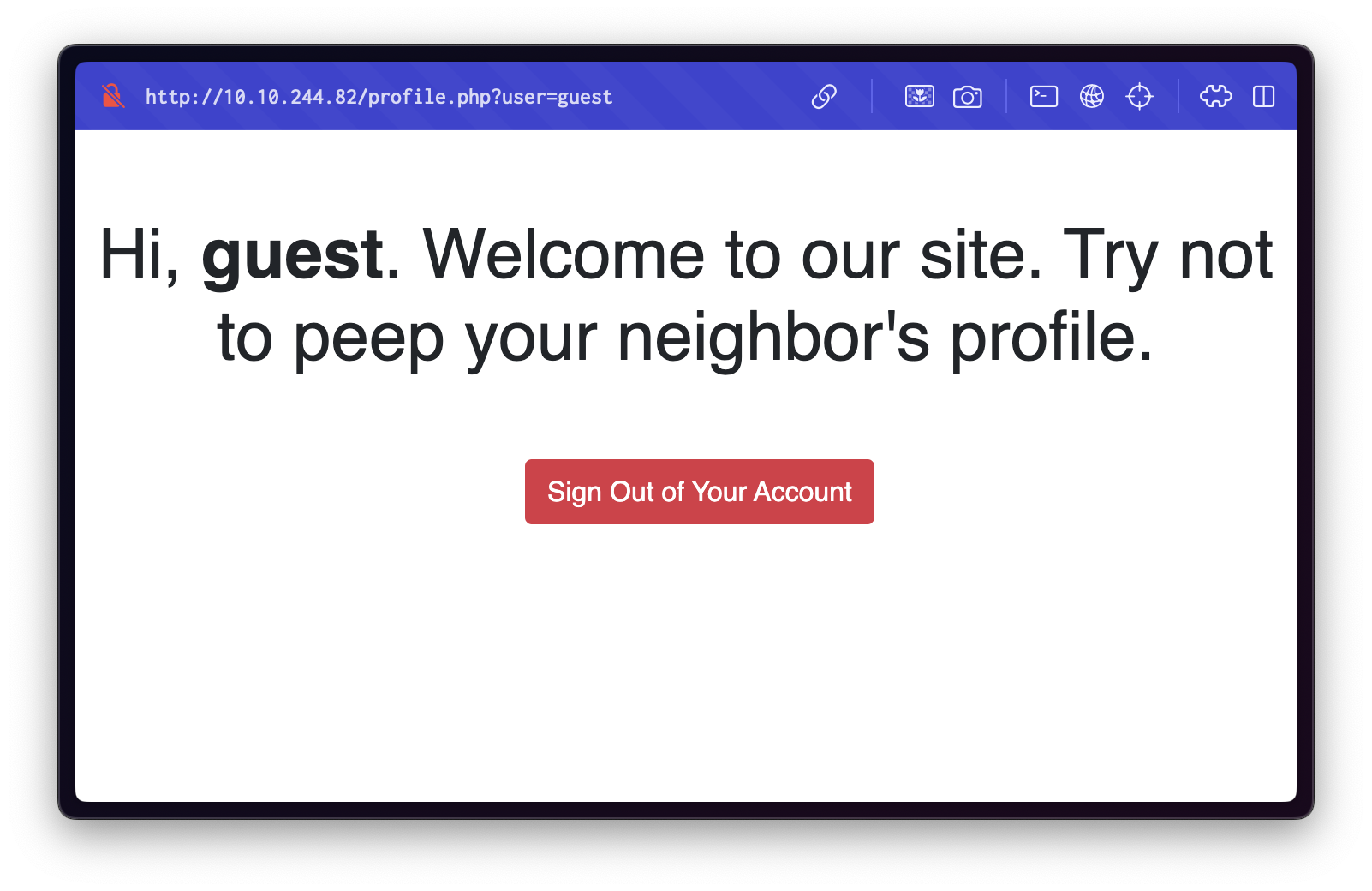
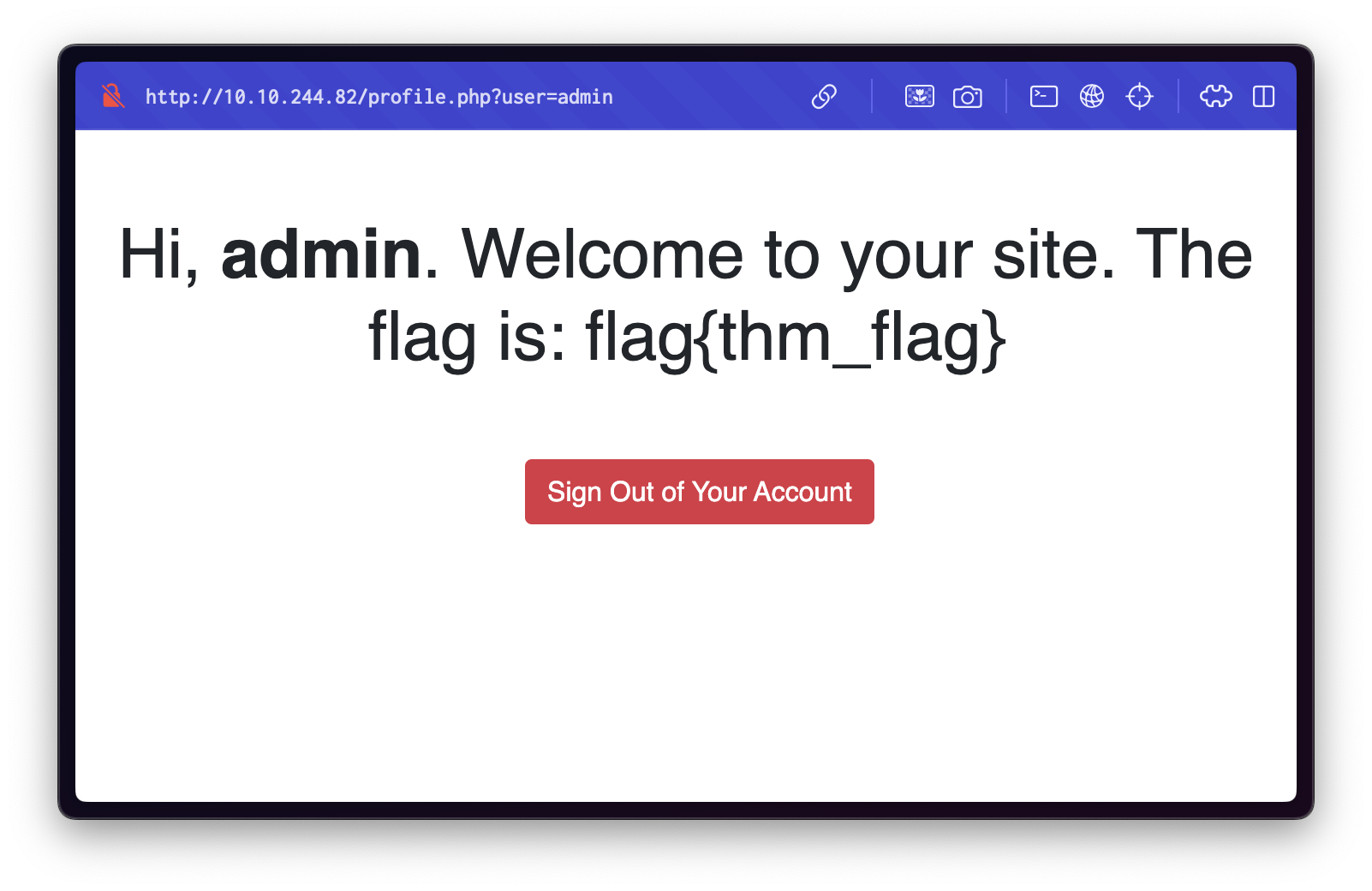
The URL of this page contains a user parameter, which is currently set to guest:
?user=guestBy modifying this parameter to admin, we are able to bypass access controls and retrieve the flag: